Abstract
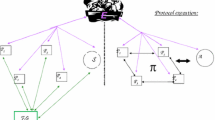
The universal composability framework is a new approach for designing and analyzing the security of cryptographic protocols. In this framework, the security of protocols is maintained under a general protocol composition operation. In the paper, we propose the universal composability framework for the analysis of proxy threshold signature and present a universally composable secure proxy threshold signature scheme which is the first one in this area. The proposed scheme is suitable for the mobile agents, which should migrate across different environment through network. Furthermore, we give the concrete analysis of the reduction to prove the security of the proposed scheme.
Similar content being viewed by others
References
Zhang K. Threshold proxy signature schemes [C]//Proceeding of the 1997 information security workshop. Heidelberg: Springer, 1998: 191–197.
Kim S, Park S, Won D. Proxy signatures, revisited [C]// ICICS’97, LNCS. Heidelberg: Springer, 1997: 223–232.
Sun H, Lee N, Hwang T. Threshold proxy signatures [C]//IEE Proceeding of Computers and Digital technique/ New York: IEEE Computer Society Press, 1999: 259–263.
Hsu C, Wu T, Wong D. New nonrepudiable threshold proxy signature scheme with known signers [J]. Journal of Systems and Software, 2001, 58(1): 119–124.
Hwang M, Lu J, Lin L. A practical (t, n) threshold proxy signature scheme based on the RSA Cryptosystem [C]//ACISP 2004, LNCS. Heidelberg: Springer, 2004: 348–357.
Wang G, Bao G, Zhou J, et al. Comments on a practical threshold proxy signature scheme based on the RSA cryptosystem [J]. IEEE Transaction on Knowledge and Data Engineering, 2004: 16(10): 1309–1311.
Kuo W, Chen M. A modified (t, n) threshold proxy signature scheme based on the RSA cryptosystem [C]//ICITA’05. New York: IEEE Computer Society Press, 2005: 576–579.
Farmer W, Gutmann J, Swarup V. Security for mobile agents: Authentication and state appraisal [C]//ESoRICS 1996, LNCS. Heidelberg: Springer, 1996: 118–130.
Canetti R. Universally composable security: A new paradigm for cryptographic protocols [C]//Proceedings of the 42th IEEE Symposium on Foundations of Computer Science. New York: IEEE Computer Society Press, 2001: 136–145.
Canetti R, Rabin T. Universal composition with joint state [C]//Crypto 2003, LNCS. Heidelberg: Springer, 2003: 265–281.
Canetti R. Universally composable signature, certification, and authentication [C]//Proceedings of the 17th IEEE workshop on Computer Security Foundations. New York: IEEE Computer Society Press, 2004: 112–116
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: the National Natural Science Foundation of China (Nos. 60703031,60703004), the National High Technology Research and Development Program (863) of China (No. 2006AA01Z4220, and the National Basic Research Program (973) of China (No. 2007CB311201)
Rights and permissions
About this article
Cite this article
Hong, X., Li, Xx., Gong, Z. et al. A universal composability framework for analysis of proxy threshold signature. J. Shanghai Jiaotong Univ. (Sci.) 14, 107–111 (2009). https://doi.org/10.1007/s12204-009-0107-2
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12204-009-0107-2