Abstract
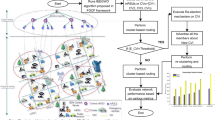
Green edge-assisted unmanned aerial vehicle (eUAV) network is an emerging network architecture enhanced with the energy efficiency technology that provides an ubiquitous communication for air and ground. It is considered a promising technology that can maintain a balance between a clean environment and a rich human life to build a sustainable world. However, the security issues exposed by UAVs have raised concerns about the trust and security for adopting eUAV network for communication. To this end, a trust assessment as a service (TaaS) scheme for secure communication of green eUAV network is proposed. The TaaS can effectively collect the valid data of UAVs about diverse and dynamic quality of service (QoS) attributes related to energy efficiency. To predict the actual data of UAVs about QoS attributes in the real green eUAV environment, an service level object calibration method is presented in TaaS. In addition, to accurately obtain the trust level of UAVs in the eUAV network, TaaS presents a trust level assessment method integrated the interval multi-attribute decision-making method and the objective weight assignment method based on deviation maximization. A case study with open source dataset and a performance analysis experiment are conducted to show that the proposed TaaS scheme can accurately and effectively assess the trust level of UAVs while outperforming other traditional trust assessment methods.









Similar content being viewed by others
Availability of data and material
The data sets supporting the results of this article are included within the article.
Notes
It represents the measurable attributes of a service that bear on its ability to satisfy the stated requirements of a service customer, which aims to implement the concept of measured service.
The QoS attributes are considered to be the metrics of QoS, which can be used as the benchmark to measure the specific non-functional quality of a service.
It is a quantitative commitment made by a service provider for a specific QoS attribute of its service. It aims at specifying quantifiable QoS attributes for the covered service.
It is a legally or formal documented agreement between the service provider and customer used to govern the QoS that the covered service is expected to be provisioned, which includes SLOs for the covered service.
References
Gupta A, Gupta SK (2022) A survey on green unmanned aerial vehicles-based fog computing: Challenges and future perspective. Trans Emerg Telecommun Technol 33(11):e4603
Gupta L, Jain R, Vaszkun G (2016) Survey of important issues in UAV communication networks. IEEE Commun Surv Tutorials 18(2):1123–1152
Chen D, Zhang N, Cheng N, Zhang K, Qin Z, Shen XS (2020) Physical layer based message authentication with secure channel codes. IEEE Trans Dependable Secure Comput 17:1079–1093
Zhi Y, Fu Z, Sun X, Yu J (2020) Security and privacy issues of UAV: a survey. Mob Netw Appl 25:95–101
Adil M, Jan MA, Liu Y, Abulkasim H, Farouk A, Song H (2023) A systematic survey: security threats to UAV-aided IoT applications, taxonomy, current challenges and requirements with future research directions. IEEE Trans Intell Transp Syst 24(2):1437–1455
Wang Y, Wang Q, Chen X, Chen D, Fang X, Yin M, Zhang N (2020) Containerguard: A real-time attack detection system in container-based big data platform. IEEE Trans Ind Inf 18(5):3327–3336
Chen D, Liao Z, Chen R, Wang H, Yu C, Zhang K, Zhang N, Shen XS (2024) Privacy-preserving anomaly detection of encrypted smart contract for blockchain-based data trading. IEEE Trans Dependable Secure Comput
Chen D, Zhang L, Liao Z, Dai H, Zhang N, Shen XS, Pang M (2024) Flexible and fine-grained access control for EHR in blockchain-assisted e-healthcare systems. IEEE Internet Things J 11:10992–11007
Chen D, Wang H, Zhang N, Nie X, Dai H-N, Zhang K, Choo KR (2022) Privacy-preserving encrypted traffic inspection with symmetric cryptographic techniques in IoT. IEEE Internet Things J 9(18):17265–17279
Wang Q, Chen X, Jin X, Li X, Chen D, Qin X (2021) Enhancing trustworthiness of internet of vehicles in space-air-ground integrated networks: attestation approach. IEEE Internet Things J 9(8):5992–6002
Yang M, Huang G, Liu J, Gui Y, Wang Q, Chen X (2023) PIMS: an efficient process integrity monitoring system based on blockchain and trusted computing in cloud-native context. Comput Model Eng Sci 136(2):1879–1898
Liang J, Liu W, Xiong NN, Liu A, Zhang S (2022) An intelligent and trust UAV-assisted code dissemination 5G system for industrial internet-of-things. IEEE Trans Industr Inf 18(4):2877–2889
Refaee E, Shamsudheen S (2022) Trust- and energy-aware cluster head selection in a UAV-based wireless sensor network using FIT-FCM. J Supercomput 78:5610–5625
Huang M, Liu A, Xiong NN, Wu J (2021) A UAV-assisted ubiquitous trust communication system in 5G and beyond networks. IEEE J Sel Areas Commun 39(11):3444–3458
Moualla A, Oumayma A, Aljnidi M (2021) Towards trust model in unmanned aerial vehicle ad hoc networks. J Commun Softw Syst 17:213–220
Ge C, Zhou L, Hancke GP, Su C (2021) A provenance-aware distributed trust model for resilient unmanned aerial vehicle networks. IEEE Internet Things J 8(16):12481–12489
Jiang B, Huang G, Wang T, Gui J, Zhu X (2022) Trust based energy efficient data collection with unmanned aerial vehicle in edge network. Trans Emerg Telecommun Technol 33(6):e3942
Bai J, Zeng Z, Wang T, Zhang S, Xiong NN, Liu A (2023) Tanto: An effective trust-based unmanned aerial vehicle computing system for the internet of things. IEEE Internet Things J 10(7):5644–5661
Li X, Jin X, Wang Q, Cao M, Chen X (2018) SCCAF: a secure and compliant continuous assessment framework in cloud-based IoT context. Wirel Commun Mob Comput 2018:1–18
Kumar RR, Kumari B, Kumar C (2021) CCS-OSSR: a framework based on hybrid mcdm for optimal service selection and ranking of cloud computing services. Clust Comput 24(2):867–883
Sun L, Dong H, Hussain OK, Hussain FK, Liu AX (2019) A framework of cloud service selection with criteria interactions. Futur Gener Comput Syst 94:749–764
Latif R, Ahmed MU, Tahir S, Latif S, Ahmad A (2022) A novel trust management model for edge computing. Complex Intell Systems 8:3747–3763
Mo W, Wang T, Zhang S, Zhang J (2020) An active and verifiable trust evaluation approach for edge computing. J Cloud Computing 9:51–69
Ruan Y, Durresi A, Uslu S (2018) Trust assessment for internet of things in multi-access edge computing. IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA) 1155–1161
Li X, Wang Q, Lan X, Chen X, Zhang N, Chen D (2019) Enhancing cloud-based iot security through trustworthy cloud service: an integration of security and reputation approach. IEEE Access 7:9368–9383
Xu Z (2010) A deviation-based approach to intuitionistic fuzzy multiple attribute group decision making. Group Decis Negot 19(1):57–76
Yadav N, Goraya MS (2018) Two-way ranking based service mapping in cloud environment. Futur Gener Comput Syst 81:53–66
Tran VX, Tsuji H, Masuda R (2009) A new QOS ontology and its QOS-based ranking algorithm for web services. Simul Model Pract Theory 17(8):1378–1398
Funding
This work was supported by the China Post-Doctoral Science Foundation under Project 2020M683296.
Author information
Authors and Affiliations
Contributions
Qixu Wang and Xiang Li wrote the main part of the manuscript. Qixu Wang developed the model. Yunxiang Qiu and Tao Zheng developed the case study. Zhiguang Qin reviewed and revised the manuscript. Xiang Li performed the simulation experiments. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Ethics approval
Not applicable.
Consent to participate
Not applicable.
Consent for publication
Not applicable.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection: Special Issue on Affordable and Clean Energy
Guest Editors: Dajiang Chen, Ning Zhang, and Chunpeng Ge
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Wang, Q., Xiao, P., Li, X. et al. Taas: Trust assessment as a service for secure communication of green edge-assisted UAV network. Peer-to-Peer Netw. Appl. (2024). https://doi.org/10.1007/s12083-024-01701-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12083-024-01701-2