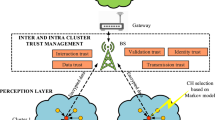
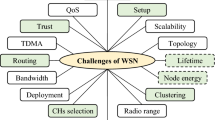
Abstract
Wireless sensor networks (WSNs) are increasingly being used in a variety of applications, such as smart healthcare systems and the Internet of Things (IoT). Trust in WSNs is the confidence in secure, efficient collaboration among nodes, crucial for reliable data packet routing. However, their susceptibility to trust-related challenges such as different threats, high energy use, and communication issues among nodes, pose substantial challenges to data integrity and availability. Recognizing the pivotal role of trust in ensuring secure data exchange and dependable device communication within the IoT framework, this paper introduces a novel trust-aware optimization technique. The approach integrates trust management into routing protocols, employing the resilient decision-making algorithm Dempster-Shafer Theory (DST) for trusted clustering and the Whale Optimization Algorithm (WOA) for routing. The primary objective is to enhance the reliability and energy efficiency of WSNs by incorporating trustworthiness considerations into optimal cluster and route selection. The proposed DST-WOA technique is evaluated using the MATLAB Simulator, demonstrating a significant 23%, 22%, and 4% improvement over existing protocols (TBSIOP, SQEER, SSDBN-TAA) in network lifetime, energy efficiency and throughput, respectively. The proposed research contributes to the development of more robust and sustainable WSNs for applications in areas such as smart healthcare systems, and IoT.









Similar content being viewed by others
Data availability
Sharing data isn’t relevant to this article because no datasets were made or looked at during this study.
Abbreviations
- WSNs:
-
Wireless Sensor Networks
- IoT:
-
Internet of Things
- DST:
-
Dempster-Shafer Theory
- WOA:
-
Whale Optimization Algorithm
- CH:
-
Cluster Head
- QoS:
-
Quality of Service
- MANETs:
-
Mobile Ad-Hoc Networks
- PSO:
-
Particle Swarm Optimization
- ACO:
-
Ant Colony Optimization
- SSDBN:
-
Salp Swarm Optimization, Deep Belief Networks
- TBSEER:
-
Trust-Based Secure and Energy-Efficient Routing
- LEACH:
-
Low Energy Adaptive Clustering Hierarchy
- SEP:
-
Smart Energy Profile
- SQEER:
-
Secure and Quality-Aware Energy-Efficient Routing
References
Li Xr, Jiang H (2022) Energy-aware healthcare system for wireless body region networks in IoT environment using the whale optimization algorithm. Wireless Pers Commun 126:2101–2117. https://doi.org/10.1007/s11277-021-08762-z
Mohan Ch.Ram, Venugopal Reddy A (2018) T-whale: Trust and whale optimization model for secure routing in Mobile ad-hoc network. Int J Artif Life Res 8(2):67–79. https://doi.org/10.4018/IJALR.2018070104
Priyanka BN, Jayaparvathy R, DivyaBharathi D (2022) Efficient and dynamic cluster head selection for improving network lifetime in WSN using whale optimization algorithm. Wireless Pers Commun 123:1467–1481. https://doi.org/10.1007/s11277-021-09192-7
Revanesh M, Sridhar V, Acken JM (2020) Secure coronas based zone clustering and routing model for distributed wireless sensor networks. Wireless Pers Commun 112:1829–1857. https://doi.org/10.1007/s11277-020-07129-0
Liao X, Wu Z, Zhang Y et al (2021) Trust-aware buffer-aided relay selection for secure communications in cooperative wireless systems. Comput Netw. https://doi.org/10.1016/j.comnet.2021.108456
Sharmin A, Anwar F, Motakabber SMA, Hashim A-HA (2021) Secure ACO-based wireless sensor network routing algorithm for IoT. 2021 8th International Conference on Computer and Communication Engineering (ICCCE), Kuala Lumpur, Malaysia, pp 190–195. https://doi.org/10.1109/ICCCE50029.2021.9467223
Bangotra DK, Singh Y, Selwal A et al (2022) A trust based secure intelligent opportunistic routing protocol for wireless sensor networks. Wireless Pers Commun 127:1045–1066. https://doi.org/10.1007/s11277-021-08564-3
Althubiti SA (2022) A trust aware authentication scheme for wireless sensor networks optimized by salp swarm optimization and deep belief networks. Math Probl Eng 2022:Article ID 7842287, 9 pages. https://doi.org/10.1155/2022/7842287
Selvi M, Thangaramya K, Ganapathy S et al (2019) An energy aware trust based secure routing algorithm for effective communication in wireless sensor networks. Wireless Pers Commun 105:1475–1490. https://doi.org/10.1007/s11277-019-06155-x
Liao X, Wu Z, Zhang Y, Jiang X (2021) Trust-aware buffer-aided relay selection for secure communications in cooperative wireless systems. Comput Netw 199:108456. https://doi.org/10.1016/j.comnet.2021.108456
Hu H, Han Y, Yao M, Song X (2022) Trust based secure and energy efficient routing protocol for wireless sensor networks. IEEE Access 10:10585–10596. https://doi.org/10.1109/ACCESS.2021.3075959
Sudha G, Tharini C (2023) Trust-based clustering and best route selection strategy for energy efficient wireless sensor networks. Automatika 64(3):634–641. https://doi.org/10.1080/00051144.2023.2208462
Li C, Dong M, Xin X, Li J, Chen X-B, Ota K (2023) Efficient privacy preserving in IoMT with blockchain and lightweight secret sharing. IEEE Internet Things J 10(24):22051–22064. https://doi.org/10.1109/JIOT.2023.3296595
Zhao X, Fang Y, Min H, Wu X, Wang W, Teixeira R (2024) Potential sources of sensor data anomalies for autonomous vehicles: An overview from road vehicle safety perspective. Exp Syst Appl 236:121358,ISSN 0957–4174. https://doi.org/10.1016/j.eswa.2023.121358
Liu C, Wu T, Li Z, Ma T, Huang J (2023) Robust online tensor completion for IoT streaming data recovery. IEEE Trans Neural Netw Learn Syst 34(12):10178–10192. https://doi.org/10.1109/TNNLS.2022.3165076
Li Z, Kong Y, Jiang C (2023) A transfer double deep Q network based DDoS detection method for internet of vehicles. IEEE Trans Veh Technol 72(4):5317–5331. https://doi.org/10.1109/TVT.2022.3233880
Qiao F, Li Z, Kong Y A privacy-aware and incremental defense method against GAN-based poisoning attack. IEEE Trans Comput Soc Syst. https://doi.org/10.1109/TCSS.2023.3263241
Rajkumar Y, Kumar SVNS (2023) An elliptic curve cryptography based certificate-less signature aggregation scheme for efficient authentication in vehicular ad hoc networks. Wireless Netw. https://doi.org/10.1007/s11276-023-03473-8
Jayashree S, Santhosh Kumar SVN (2023) LAPEP—Lightweight Authentication Protocol with Enhanced Privacy for effective secured communication in vehicular ad-hoc network. Wireless Netw. https://doi.org/10.1007/s11276-023-03459-6
Dinesh K, Santhosh Kumar SVN (2023) Energy-efficient trust-aware secured neuro-fuzzy clustering with sparrow search optimization in wireless sensor network. Int J Inf Secur. https://doi.org/10.1007/s10207-023-00737-4
Santhosh Kumar SVN, Palanichamy Y, Selvi M et al (2021) Energy efficient secured K means based unequal fuzzy clustering algorithm for efficient reprogramming in wireless sensor networks. Wireless Netw 27:3873–3894. https://doi.org/10.1007/s11276-021-02660-9
Thangaramya K, Kulothungan K, Indira Gandhi S et al (2020) Intelligent fuzzy rule-based approach with outlier detection for secured routing in WSN. Soft Comput 24:16483–16497. https://doi.org/10.1007/s00500-020-04955-z
Selvi M, Santhosh Kumar SVN, Ganapathy S et al (2021) An energy efficient clustered gravitational and fuzzy based routing algorithm in WSNs. Wireless Pers Commun 116:61–90. https://doi.org/10.1007/s11277-020-07705-4
Basir O, Yuan X (2007) Engine fault diagnosis based on multi-sensor information fusion using dempster-Shafer evidence theory. Information fusion 8(4):379–386
Kalidoss T, Rajasekaran L, Kanagasabai K, Sannasi G, Kannan A (2020) QoS aware trust based routing algorithm for wireless. Wireless Pers Commun 110(4):1637–1658
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
We developed a novel trust-aware optimization technique for trustworthy and energy-efficient routing in WSNs. By integrating trust management mechanisms using Dempster-Shafer Theory (DST) for clustering and Whale Optimization Algorithm (WOA) for routing, my work aimed to enhance reliability and energy efficiency. Proposed protocol assessed through MATLAB Simulator, exhibits substantial enhancements of 23% in network lifetime, 22% in energy efficiency, and 4% in throughput compared to existing protocols (TBSIOP, SQEER, SSDBN-TAA). The proposed research contributes to the development of more robust and sustainable WSNs for applications in areas such as smart healthcare systems, and IoT.
Corresponding author
Ethics declarations
Ethics approval
Not applicable.
Consent to publish
Not applicable.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Singh, S., Anand, V. & Yadav, S. Trust-based clustering and routing in WSNs using DST-WOA. Peer-to-Peer Netw. Appl. (2024). https://doi.org/10.1007/s12083-024-01651-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12083-024-01651-9