Abstract
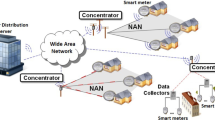
Authentication and key agreement (AKA) methods are designed to ensure that only authorized entities are communicating and to ensure that their communications are secure. In contrast, the majority of designed protocols are homogeneous, meaning that communicating entities share the same cryptographic setting. A smart grid (SG) is nonetheless a complex system with a diverse network. Thus, SG interconnects a large number of end devices, intermediary devices, and systems that are part of distinct cryptographic environments. We therefore suggested a heterogeneous authentication protocol for smart grids (HAP-SG). In the proposed protocol, the smart meter (SM) belongs to a certificateless public key cryptography (CL-PKC) environment, whereas the service provider (SP) belongs to a public key infrastructure environment (PKI). HAP-SG ensures that only authorized SM and SP communicate and that their communications are kept secret, despite the fact that they belong to separate cryptographic environments. Security of HAP-SG depends on the difficulty of the elliptic curve discrete logarithm (ECDL) problem. On the other hand, for security analysis, the random oracle model (ROM) is utilized. Experiments show that our protocol is more efficient in terms of computation costs and communication costs.








Similar content being viewed by others
Data availability
Not applicable.
References
Simoes MG, Roche R, Kyriakides E, Suryanarayanan S, Blunier B, McBee KD, Nguyen PH, Ribeiro PF, Miraoui à (2012) A comparison of smart grid technologies and progresses in europe and the us. IEEE Trans Ind Appl 48(4):1154–1162
Amin SM, Wollenberg BF (2005) Toward a smart grid: power delivery for the 21st century. IEEE Power Energ Mag 3(5):34–41
Amin M (2004) Balancing market priorities with security issues. IEEE Power Energ Mag 2(4):30–38
Pillitteri VY, Brewer TL (2014) Guidelines for smart grid cybersecurity. NIST Pubs
Li X, Liang X, Lu R, Shen X, Lin X, Zhu H (2012) Securing smart grid: cyber attacks, countermeasures, and challenges. IEEE Commun Mag 50(8):38–45
Marmol FG, Sorge C, Ugus O, Perez GM (2012) Do not snoop my habits: preserving privacy in the smart grid. IEEE Commun Magazine 50(5):166–172
Kim T, Hyun M, Kim J, Kim J, Kim J, Lee D (2015) The pki-based device authentication system for ami. In: 23rd International Conference on Electricity Distribution
Shamir A (1984) Identity-based cryptosystems and signature schemes, in: Workshop on the theory and application of cryptographic techniques. Springer, pp 47–53
Al-Riyami SS, Paterson KG (2003) Certificateless public key cryptography, in: International conference on the theory and application of cryptology and information security. Springer, pp 452–473
Wu D, Zhou C (2011) Fault-tolerant and scalable key management for smart grid. IEEE Transactions on Smart Grid 2(2):375–381
Xia J, Wang Y (2012) Secure key distribution for the smart grid. IEEE Transactions on Smart Grid 3(3):1437–1443
Park JH, Kim M, Kwon D (2013) Security weakness in the smart grid key distribution scheme proposed by xia and wang. IEEE Transactions on Smart Grid 4(3):1613–1614
Li X, Liu S, Kumari S, Chen CM (2023) Psap-wsn: A provably secure authentication protocol for 5g-based wireless sensor networks. CMES-Computer Modeling in Engineering & Sciences 135(1):711–732
Li X, Wu F, Kumari S, Xu L, Sangaiah AK, Choo K-KR (2019) A provably secure and anonymous message authentication scheme for smart grids. Journal of Parallel and Distributed Computing 132:242–249
Wu L, Wang J, Zeadally S, He D (2019) Anonymous and efficient message authentication scheme for smart grid. Security and Communication Networks, Article ID 4836016
Mahmood K, Chaudhry SA, Naqvi H, Kumari S, Li X, Sangaiah AK (2018) An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Futur Gener Comput Syst 81:557–565
Abbasinezhad-Mood D, Nikooghadam M (2018) Design and hardware implementation of a security-enhanced elliptic curve cryptography based lightweight authentication scheme for smart grid communications. Futur Gener Comput Syst 84:47–57
Chen Y, Martinez J.-F, Castillejo P, Lopez L (2019) A bilinear map pairing based authentication scheme for smart grid communications: Pauth. IEEE Access 7:22633–22643
Wu TY, Lee YQ, Chen CM, Tian Y, Al-Nabhan NA (2021) An enhanced pairing-based authentication scheme for smart grid communications. J Ambient Intell Human Comput 1–13
Nkurunziza E, Mwitende G, Tandoh L, Li F (2021) Certificateless authentication and consensus for the blockchain based smart grid, in: International Conference on Frontiers in Cyber Security. Springer, pp 134–151
Nkurunziza E, Tandoh L, Elfadul I, Li F (2023) Ecaap-sg: Efficient certificateless anonymous authentication protocol for sg. Secur Priv 6(1):e273
Miller VS (1985) Use of elliptic curves in cryptography, in: Conference on the theory and application of cryptographic techniques. Springer, pp 417–426
Koblitz N (1987) Elliptic curve cryptosystems. Math Comput 48(177):203–209
Hankerson D, Menezes AJ, Vanstone S (2006) Guide to elliptic curve cryptography. Springer Science and Business Media
Mwitende G, Ye Y, Ali I, Li F (2020) Certificateless authenticated key agreement for blockchain-based wbans. J Syst Archit 110:101777
Huang X, Mu Y, Susilo W, Wong DS, Wu W (2007) Certificateless signature revisited, in: Australasian Conference on Information Security and Privacy. Springer, pp 308–322
Johnson D, Menezes A, Vanstone S (2001) The elliptic curve digital signature algorithm (ecdsa). Int J Inf Secur 1(1):36–63
Bellare M, Rogaway P (1993) Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security, pp 62–73
Wu T-Y, Tseng Y-M (2010) An efficient user authentication and key exchange protocol for mobile client-server environment. Comput Netw 54(9):1520–1530
Choon JC, Cheon JH (2003) An identity-based signature from gap Diffie-Hellman groups, in: International workshop on public key cryptography. Springer, pp 18–30
Pointcheval D, Stern J (2000) Security arguments for digital signatures and blind signatures. J Cryptol 13(3):361–396
Blake-Wilson S, Johnson D, Menezes A (1997) Key agreement protocols and their security analysis. In: IMA International Conference on Cryptography and Coding. Springer, pp 30–45
Lo N-W, Tsai J-L (2015) An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings. IEEE Trans Intell Transp Syst 17(5):1319–1328
Liu J, Zhang L, Sun R (2016) 1-raap: An efficient 1-round anonymous authentication protocol for wireless body area networks. Sensors 16(5):728
Wazid M, Das AK, Kumar N, Conti M, Vasilakos AV (2017) A novel authentication and key agreement scheme for implantable medical devices deployment. IEEE J Biomed Health Inform 22(4):1299–1309
Funding
This work is supported by Sichuan Science and Technology Program (Grant No. 2022ZHCG0037).
Author information
Authors and Affiliations
Contributions
Nkurunziza egide conceived the entire research, including the text, figures, and tables. Fagen Li oversaw the entire research project.
Corresponding author
Ethics declarations
Ethics approval
Not applicable.
Consent for publication
All authors consent to the publication of every detail of this article’s content in peer-to-peer networking and applications.
Conflicts of interest
The authors report having no conflicts of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection: Special Issue on 2 - Track on Security and Privacy
Guest Editor: Rongxing Lu
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Egide, N., Li, F. HAP-SG: Heterogeneous authentication protocol for smart grid. Peer-to-Peer Netw. Appl. 16, 1365–1379 (2023). https://doi.org/10.1007/s12083-023-01485-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-023-01485-x