Abstract
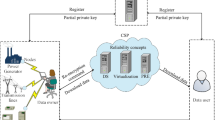
Cloud-Assisted Internet of Things (IoT) has become an increasingly widespread technological trend that can significantly improve the performance of IoT applications by outsourcing massive data from IoT devices to the cloud due to their limited storage and computation capabilities. Since the cloud is not fully trusted, the outsourced data has security issues, such as confidentiality, authenticity, and access control. Attribute-based Signcryption (ABSC) is a promising cryptographic solution to address the above problems. However, the existing ABSC schemes create heavy computation overhead and are unsuitable for some resource-constrained IoT devices. This paper proposes a lightweight pairing-free ciphertext-policy ABSC for Cloud-Assisted IoT (PF-CP-ABSC). This scheme uses elliptic curve cryptography (ECC) to reduce computation overhead instead of bilinear-pairings. Further, we adopt CP-ABSC to provide confidentiality, authenticity, and fine-grained access control. In the security analysis, we prove the security of the PF-CP-ABSC scheme under the hardness of Elliptic Curve Decisional Diffie-Hellman (ECDDH) and Elliptic-curve Discrete Logarithm problem (ECDLP). The theoretical analysis and experimental results show that this scheme is lightweight and is suitable for resource-constrained IoT applications.






Similar content being viewed by others
References
Xu P, He S, Wang W, Susilo W, Jin H (2017) Lightweight searchable public-key encryption for cloud-assisted wireless sensor networks. IEEE Transactions on Industrial Informatics 14(8), 3712–3723
Wang W, Xu P, Yang LT (2018) Secure data collection, storage and access in cloud-assisted iot. IEEE cloud computing 5(4):77–88
Gagné M, Narayan S, Safavi-Naini R (2010) Threshold attribute-based signcryption. In: International Conference on Security and Cryptography for Networks, Springer, pp 154–171
Wang C, Huang J (2011) Attribute-based signcryption with ciphertext-policy and claim-predicate mechanism. In: 2011 Seventh International Conference on Computational Intelligence and Security, IEEE, pp 905–909
Chen C, Chen J, Lim HW, Zhang Z, Feng D (2012) Combined public-key schemes: The case of abe and abs. In: International Conference on Provable Security, Springer, pp 53–69
Emura K, Miyaji A, Rahman MS (2012) Dynamic attribute-based signcryption without random oracles. Int J Appl Cryptogr 2(3):199–211
Han Y, Lu W, Yang X (2013) Attribute-based signcryption scheme with non-monotonic access structure. In: 2013 5th International Conference on Intelligent Networking and Collaborative Systems, IEEE, pp 796–802
Rao YS, Dutta R (2014) Expressive bandwidth-efficient attribute based signature and signcryption in standard model. In: Australasian Conference on Information Security and Privacy, Springer, pp 209–225
Pandit T, Pandey SK, Barua R (2014) Attribute-based signcryption: Signer privacy, strong unforgeability and ind-cca2 security in adaptive-predicates attack. In: International Conference on Provable Security, Springer, pp 274–290
Hu C, Cheng X, Tian Z, Yu J, Akkaya K, Sun L (2015) An attribute-based signcryption scheme to secure attribute-defined multicast communications. In: International Conference on Security and Privacy in Communication Systems, Springer, pp 418–437
Liu J, Huang X, Liu JK (2015) Secure sharing of personal health records in cloud computing: Ciphertext-policy attribute-based signcryption. Future Generation Computer Systems 52:67–76
Rao YS (2017) A secure and efficient ciphertext-policy attribute-based signcryption for personal health records sharing in cloud computing. Future Generation Computer Systems 67:133–151
Belguith S, Kaaniche N, Mohamed M, Russello G (2018) C-absc: cooperative attribute based signcryption scheme for internet of things applications. In: 2018 IEEE International Conference on Services Computing (SCC), IEEE, pp 245–248
Alsharif A, Shafee A, Nabil M, Mahmoud M, Alasmary W (2019) A multi-authority attribute-based signcryption scheme with efficient revocation for smart grid downlink communication. In: 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), IEEE, pp 1025–1032
Khasawneh S, Kadoch M (2021) Ecs-cp-abe: A lightweight elliptic curve signcryption scheme based on ciphertext-policy attribute-based encryption to secure downlink multicast communication in edge envisioned advanced metering infrastructure networks. Transactions on Emerging Telecommunications Technologies 32(8):e4102
Zheng Y (1997) Digital signcryption or how to achieve cost. In: Annual international cryptology conference, Springer, pp 165–179
Sahai A, Waters B (2005) Fuzzy identity-based encryption. In: Annual international conference on the theory and applications of cryptographic techniques, Springer, pp 457–473
Waters B (2011) Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In: International Workshop on Public Key Cryptography, Springer, pp 53–70
Li J, Huang Q, Chen X, Chow SS, Wong DS, Xie D (2011) Multi-authority ciphertext-policy attribute-based encryption with accountability. In: Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, pp 386–390
Liang K, Fang L, Susilo W, Wong DS (2013) A ciphertext-policy attribute-based proxy re-encryption with chosen-ciphertext security. In: 2013 5th International Conference on Intelligent Networking and Collaborative Systems, IEEE, pp 552–559
Maji HK, Prabhakaran M, Rosulek M (2008) Attribute-based signatures: Achieving attribute-privacy and collusion-resistance. IACR Cryptol ePrint Arch 2008:328
Yao X, Chen Z, Tian Y (2015) A lightweight attribute-based encryption scheme for the internet of things. Future Generation Computer Systems 49:104–112
Ullah I, Amin NU, Khan J, Rehan M, Naeem M, Khattak H, Khattak SJ, Ali H (2019) A novel provable secured signcryption scheme????: A hyper-elliptic curve-based approach. Mathematics 7(8):686
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kiran, M.A., Pasupuleti, S.K. & Eswari, R. A lightweight pairing-free ciphertext-policy attribute-based signcryption for cloud-assisted IoT. Peer-to-Peer Netw. Appl. 15, 2390–2403 (2022). https://doi.org/10.1007/s12083-022-01356-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-022-01356-x