Abstract
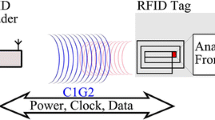
The rapid proliferation of Radio Frequency Identification (RFID) tags in the past decade has made tremendous impact on our daily lives. As part of Internet of Things (IoT), RFID technology ensures an efficient, secure and reliable system to identify tagged objects in supply chain environment such as manufacturing, automotive and healthcare. Several lightweight authentication solutions have been proposed to satisfy optimal security and privacy features of RFID communication. Hopper-Blum (HB) family of protocols that rely on the hard problem of Learning Parity with Noise (LPN) is a series of lightweight authentication protocol used to identify RFID tags. Our study shows that recent RFID authentication protocols from HB family that mostly focus on two party authentication such as tag-reader authentication, in general, cannot be applied directly to a three party authentication such as tag-reader-server authentication. In contrast to typical RFID authentication system, we consider the channel between the reader and back-end server insecure. We focus HB protocol and its variants and propose a modified protocol where the entire system is authenticated under LPN-based scheme.





Similar content being viewed by others
References
Wu F, Xu L, Kumari S, Li X, Das AK, Shen J (2018) A lightweight and anonymous RFID tag authentication protocol with cloud assistance for e-healthcare applications. J Ambient Intell Human Comput 9(4):919–930
Zheng L, Xue Y, Zhang L, Zhang R (2017) Mutual Authentication Protocol for RFID based on ECC. In: IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), vol 2. IEEE, pp 320–323
Gope P, Lee J, Quek TQS (2018) Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions. IEEE Trans Inf Forensic Secur 13.11:2831–2843
BD D, Al-Turjman F, Mostarda L (2019) A Hash-Based RFID Authentication Mechanism for Context-Aware Management in IoT-Based Multimedia Systems. Sensors 19.18:3821
Welbourne E, Battle L, Cole G, Gould K, Rector K, Raymer S, Balazinska M, Borriello G (2009) Building the internet of things using RFID: the RFID ecosystem experience. IEEE Internet Comput 13(3):48–55
Juels A, Weis SA (2005) Authenticating pervasive devices with human protocols. In: Annual international cryptology conference. Springer, Berlin, pp 293–308
Batina L et al (2006) An elliptic curve processor suitable for RFID tags. International Association for Cryptologic Research ePrint Archive
Hopper NJ, Blum M (2001) Secure human identification protocols. In: International conference on the theory and application of cryptology and information security. Springer, Berlin, pp 52–66
Gilbert H, Robshaw M, Sibert H (2005) An active attack against HB+ - a provably secure lightweight authentication protocol: An active attack against HB+ - a provably secure lightweight authentication. Cryptology ePrint Archive Report 2005/237
Bringer J, Chabanne H, Dottax E (2006) HB++: A lightweight authentication protocol secure against some attacks. In: SecPerU, pp 28–33
Munilla J, Alberto P (2007) HB-MP A Further step in the HB-family of lightweight authentication protocols. Comput Netw 51(9):2262–2267
Gilbert H, Robshaw MJB, Seurin Y (2008) Good variants of HB+ are hard to find. In: Tsudik G (ed) FC 2008, volume 5143 of LNCS. Springer, pp 156–170
Ouafi K, Overbeck R, Vaudenay S (2008) On the security of HB# against a man-in-the-middle attack. In: International Conference on the Theory and Application of Cryptology and Information Security. Springer, Berlin, pp 108–124
Nguyen TD, Pham HTB, Van HD (2010) An efficient Pseudo Inverse matrix-based solution for secure auditing. In: IEEE RIVF International Conference on Computing & Communication Technologies, Research, Innovation, and Vision for the Future (RIVF). IEEE, pp 1–6
MSI Mamun, Miyaji A (2014) A privacy-preserving efficient RFID authentication protocol from SLPN assumption. International Journal of Computational Science and Engineering (IJCSE), Special Issue on Converged Networks, Technologies and Applications, Inderscience Publishers, vol 9
Li X, Xu J, Zhang Z (2019) Revisiting the Security of Qian others.’s Revised tree-LSHB+ Protocol. Wirel Person Commun 106(2):321–343
Cao X, O’Neill M (2011) F-HB: An efficient forward private protocol. In: 2011 Workshop on Lightweight Security & Privacy: Devices, Protocols, and Applications. IEEE, pp 53–60
Billet O, Etrog J, Gilbert H (2010) Lightweight privacy preserving authentication for RFID using a stream cipher. In: International Workshop on Fast Software Encryption. Springer, Berlin, pp 55–74
Leng X, Mayes K, Markantonakis K (2008) HB-MP+ protocol: An improvement on the HB-MP protocol. In: 2008 IEEE international conference on RFID. IEEE, pp 118–124
Applebaum B, Ishai Y, Kushilevitz E (2009) Cryptography with constant input locality. J Cryptol 22(4):429–469
Mamun MSI, Miyaji A, Rahman M (2012) A Secure and Private RFID Authentication Protocol under SLPN Problem. NSS2012, LNCS 7645, pp 476–489
Jain A, Krenn S, Pietrzak K, Tentes A (2012) Commitments and Efficient Zero-Knowledge Proofs from Learning Parity with Noise. ASIACRYPT 2012, LNCS 7658, pp 663–680
Park T, Seo H, Kim J, Park H, Kim H (2018) Efficient parallel implementation of matrix multiplication for Lattice-Based cryptography on modern ARM processor. Security and Communication Networks
Deng RH, Li Y, Yung M, Zhao Y (2010) A new framework for RFID privacy. In: European Symposium on Research in Computer Security. Springer, Berlin, pp 1–18
Rizomiliotis P, Gritzalis S (2012) GHB#: A provably secure HB-like lightweight authentication protocol. In: International Conference on Applied Cryptography and Network Security. Springer, Berlin, pp 489–506
Micciancio D, Mol P (2011) Pseudorandom Knapsacks and the Sample Complexity of LWE Search-to-Decision Reductions. CRYPTO 2011, volume 6841 of LNCS. Springer, pp 465–484
Katz J, Shin JS, Smith A (2010) Parallel and concurrent security of the HB and HB+ protocols. J Cryptol 23(3):402–421
Moriyama D, Matsuo SI, Ohkubo M (2012) Relations among notions of privacy for RFID authentication protocols. In: Computer Security– ESORICS. Springer LNCS, pp 661–678
IoT and RFID: What’s the Connection?. RFID journal expert views. https://rfidjournal.com/iot-and-rfid-whats-the-connection, Accessed 7 July 2020
The Role of RFID Technology and Internet of Things in Healthcare. Digitium IoT Software, https://digiteum.com/rfid-technology-internet-of-things. Accessed 10 July 2020
Jo S, Lee J, Han J, Ghose S (2020) P2P Computing for intelligence of things. Peer-to-Peer Netw Appl 13(2):575–578
Get smarter about the many benefits of P2P IoT. Nabto Inc. P2P IoT solution. https://www.nabto.com/p2p-explainer/, Accessed 10 July 2020
He XU, WANG SP, WANG RC, WANG ZQ (2011) Efficient P2P-based mutual authentication protocol for RFID system security of EPC network using asymmetric encryption algorithm. J China Univ Posts Telecommun 18:40–47
Guo Q, Johansson T (2020) Carl löndahl Solving LPN Using Covering Codes. J Cryptol 33.1:1–33
Bagadia K, Urbi Chatterjee DBR, Mukhopadhyay D, Chakraborty RS (2019) Revisiting the Security of LPN Based RFID Authentication Protocol and Potential Exploits in Hardware Implementations. In: International Conference on Security, Privacy, and Applied Cryptography Engineering. Springer, Cham, pp 214–230
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mamun, M., Miyaji, A., Luv, R. et al. A lightweight multi-party authentication in insecure reader-server channel in RFID-based IoT. Peer-to-Peer Netw. Appl. 14, 708–721 (2021). https://doi.org/10.1007/s12083-020-01007-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-020-01007-z