Abstract
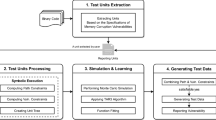
The P2P network has the characteristics of opening and sharing, and a large number of managing and controlling software are deployed on the distributed network nodes. Hence, it is a significant problem to protect software on these untrusted nodes from being maliciously reversed and tampered, and eventually guarantee the P2P network security. Function calls are often the important targets of reverse analysis, which can reveal the software structure and functionality and contribute to malicious attacks. Attackers can identify function calls and execution paths through static code analysis, and can also obtain function call sequences and determine function call relations through dynamic stack backtracking analysis. In terms of these problems, this paper proposes a code protection method against function call analysis. In the static aspect, the techniques such as function address mapping and instruction overlap are employed to hide the function execution paths. In the dynamic aspect, the techniques such as stack frame migration are used to protect the function call sequences and relations from stack backtracking. The method is evaluated in terms of validity, space overhead and time overhead respectively. The experimental results indicate that the method can effectively resist some specific static and dynamic reverse analysis of function calls, and has good space and time overhead performances.











Similar content being viewed by others
References
Balachandran V, Keong NW, Emmanuel S (2014) Function level control flow obfuscation for software security. In: 2014 8th international conference on complex, intelligent and software intensive systems (CISIS), pp 133–140. IEEE
Barak B, Goldreich O, Impagliazzo R, Rudich S, Sahai A, Vadhan S, Yang K (2001) On the (im) possibility of obfuscating programs. In: Annual international cryptology conference, pp 1–18. Springer
Ceccato M, Di Penta M, Falcarin P, Ricca F, Torchiano M, Tonella P (2014) A family of experiments to assess the effectiveness and efficiency of source code obfuscation techniques. Empir Softw Eng 19 (4):1040–1074
Choudhary U, Yadav M (2015) Review on reverse engineering techniques of software engineering. International Journal of Computer Applications 119(14):7–10
Collberg C, Thomborson C, Low D (1997) A taxonomy of obfuscating transformations. Tech. rep., Department of Computer Science, The University of Auckland, New Zealand
Collberg CS, Thomborson C, Low DWK (2003) Obfuscation techniques for enhancing software security. US Patent 6:668,325
Gautam P, Saini H (2017) A novel software protection approach for code obfuscation to enhance software security. International Journal of Mobile Computing and Multimedia Communications (IJMCMC) 8(1):34–47
Jang Y, Kim J, Lee W (2018) Development and application of internet of things educational tool based on peer to peer network. Peer-to-Peer Networking and Applications 11(6):1217–1229
Klimek I, Keltika M, Jakab F (2011) Reverse engineering as an education tool in computer science. In: 2011 9th international conference on emerging eLearning technologies and applications (ICETA), pp 123–126. IEEE
Kulkarni A, Metta R (2014) A new code obfuscation scheme for software protection. In: 2014 IEEE 8th international symposium on service oriented system engineering (SOSE), pp 409–414. IEEE
LeDoux C, Sharkey M, Primeaux B, Miles C (2012) Instruction embedding for improved obfuscation. In: Proceedings of the 50th annual southeast regional conference, pp 130–135. ACM
Madou M, Anckaert B, Moseley P, Debray S, De Sutter B, De Bosschere K (2005) Software protection through dynamic code mutation. In: International Workshop on information security applications, pp 194–206. Springer
Majumdar A, Thomborson C (2006) Manufacturing opaque predicates in distributed systems for code obfuscation. In: Proceedings of the 29th Australasian computer science conference-volume 48, pp 187–196. Australian Computer Society, Inc
Mavrogiannopoulos N, Kisserli N, Preneel B (2011) A taxonomy of self-modifying code for obfuscation. Comput Secur 30(8):679–691
Ogiso T, Sakabe Y, Soshi M, Miyaji A (2003) Software obfuscation on a theoretical basis and its implementation. IEICE Trans Fundam Electron Commun Comput Sci 86(1):176–186
Pavlovic D (2011) Gaming security by obscurity. In: Proceedings of the 2011 new security paradigms workshop, pp 125–140. ACM
Schrittwieser S, Katzenbeisser S (2011) Code obfuscation against static and dynamic reverse engineering. In: International workshop on information hiding, pp 270–284. Springer
Sebastian SA, Malgaonkar S, Shah P, Kapoor M, Parekhji T (2016) A study & review on code obfuscation. In: World conference on futuristic trends in research and innovation for social welfare (Startup Conclave), pp 1–6. IEEE
Shi Z, Zhou C, Gu Y, Goodman NA, Qu F (2017) Source estimation using coprime array: A sparse reconstruction perspective. IEEE Sensors J 17(3):755–765
Suenaga M (2009) A museum of api obfuscation on win32. In: Proceedings of 12th association of anti-virus asia researchers international conference, AVAR, vol 2009
Wang C, Hill J, Knight J, Davidson J (2000) Software tamper resistance: Obstructing static analysis of programs. Tech. rep., Technical Report CS-2000-12, University of Virginia, 12 2000
Xie X, Liu F, Lu B (2014) A data obfuscation based on state transition graph of mealy automata. In: International conference on intelligent computing, pp 520–531. Springer
Xie X, Liu F, Lu B, Xiang F (2016) An iteration obfuscation based on instruction fragment diversification and control flow randomization. International Journal of Computer Theory and Engineering 8(4):303
Yang G, He S, Shi Z (2017) Leveraging crowdsourcing for efficient malicious users detection in large-scale social networks. IEEE Internet Things J 4(2):330–339
Yang G, He S, Shi Z, Chen J (2017) Promoting cooperation by the social incentive mechanism in mobile crowdsensing. IEEE Commun Mag 55(3):86–92
You I, Yim K (2010) Malware obfuscation techniques: A brief survey. In: 2010 International conference on broadband, wireless computing, communication and applications (BWCCA), pp 297–300. IEEE
Zhou C, Gu Y, He S, Shi Z (2018) A robust and efficient algorithm for coprime array adaptive beamforming. IEEE Trans Veh Technol 67(2):1099–1112
Zhou Y, Tang W, Zhang D, Lan X, Zhang Y (2017) A case for software-defined code scheduling based on transparent computing. Peer-to-Peer Networking and Applications, pp 1–11
Acknowledgements
This research was supported by the National Natural Science Foundation of China (No. 61272489, 61302159, 61379151, 61602508, 61772549).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection: Special Issue on Networked Cyber-Physical Systems
Guest Editors: Heng Zhang, Mohammed Chadli, Zhiguo Shi, Yanzheng Zhu, and Zhaojian Li
Appendix
Appendix

Rights and permissions
About this article
Cite this article
Xiang, F., Gong, D., Li, J. et al. A code protection method against function call analysis in P2P network. Peer-to-Peer Netw. Appl. 12, 1799–1809 (2019). https://doi.org/10.1007/s12083-019-00757-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-019-00757-9