Abstract
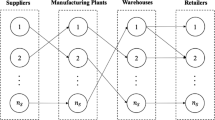
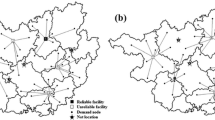
In today’s world, intentional disruptions in networks are expanding and the impacts are seen in many parts of the world. An effective approach for reducing the impact of such disruptions is to confuse invaders. Increasing ambiguity in the network is one of the effective ways which may confuse the invaders. To attain this goal, dummy facilities are added to the network. Dummy facilities are the facilities which are exactly the same as the real ones thus making it hard for the invader to make the distinction. In this paper, a new multi-objective mathematical model is presented to suitably design a network consisting of real and dummy warehouses. One objective is to minimize the total cost and the other is set to maximize reliability. An index for assessing network reliability is also introduced and used. The model is solved using AUGMECON and NSGA-II. Results demonstrate that establishing dummy facilities in the network will increase reliability while no significant cost is imposed.









Similar content being viewed by others
Notes
Non-dominated sorting chemical reaction optimization.
References
Razmi J, Zahedi-Anaraki A and Zakerinia M 2013 A bi-objective stochastic optimization model for reliable warehouse network redesign. Math. Comput. Model.. 58:1804–1813.
Snyder L V, Atan Z, Peng P, Rong Y, Schmitt A J and Sinsoysal, B 2016 OR/MS models for supply chain disruptions: A review. IIE Trans.. 48:89–109
Thompson D J 2017 Southeastern state local law enforcement preparedness in domestic terrorism interdiction: A quantitative ex-post facto study. Doctor of Philosophy Degree, Capella University, Minneapolis, MN
Ouyang M, Xu M, Zhang C and Huang S 2017 Mitigating electric power system vulnerability to worst-case spatially localized attacks. Reliab. Eng. Syst. Saf. 165:144–154.
Tran T H, O’Hanley J R and Scaparra M P 2016 Reliable hub network design: Formulation and solution techniques. Transp. Sci. 51(1):1–19
DuHadway S, Carnovale S and Hazen B 2019 Understanding risk management for intentional supply chain disruptions: Risk detection, risk mitigation, and risk recovery. Ann. Oper. Res.. 283:179–198
Snyder L V 2003 Supply chain robustness and reliability: Models and algorithms. Doctor of Philosophy Degree, Northwestern University, Evanston, IL.
Snyder L V and Daskin M S 2005 Reliability models for facility location: the expected failure cost case. Transp. Sci. 39:400–416
Scaparra M P and Church R L 2015 Location Problems Under Disaster Events. Location Science. Switzerland: Springer, pp. 623–642
Smith J C and Song Y 2019 A Survey of Network Interdiction Models and Algorithms. Eur. J. Oper. Res. (in press)
Church R L, Scaparra M P and Middleton R S 2004 Identifying critical infrastructure: the median and covering facility interdiction problems. Ann. Assoc. Amer. Geograph.. 94:491–502
Church R L and Scaparra M P 2007 Protecting critical assets: the r-interdiction median problem with fortification. Geograph. Anal. 39:129–146
Scaparra M P and Church R L 2008 An exact solution approach for the interdiction median problem with fortification. Eur. J. Oper. Res. 189:76–92
Khanduzi R and Maleki H 2018 A novel bilevel model and solution algorithms for multi-period interdiction problem with fortification. Appl. Intell. 48(9):2770–2791
Bao S, Zhang C, Ouyang M and Miao L 2019 An integrated tri-level model for enhancing the resilience of facilities against intentional attacks. Ann. Oper. Res. 283:87–117.
Fathollahi-Fard A M and Hajiaghaei-Keshteli M 2018 A bi-objective partial interdiction problem considering different defensive systems with capacity expansion of facilities under imminent attacks. Appl. Soft Comput. 68: 343–359
Maiyar L M and Thakkar J J 2018 Modelling and analysis of intermodal food grain transportation under hub disruption towards sustainability. Int. J. Product. Econ. 217: 281–297
Li Q, Zeng B and Savachkin A 2013 Reliable facility location design under disruptions. Comput. Oper. Res. 40:901–909
Losada C, Scaparra M P and O’Hanley J R 2012 Optimizing system resilience: a facility protection model with recovery time. Eur. J. Oper. Res. 217:519–530
Aksen D, Akca S Ş and Aras N 2014 A bilevel partial interdiction problem with capacitated facilities and demand outsourcing. Comput. Oper. Res. 41:346–358
Zhang C, Ramirez-Marquez J E and Li Q 2018 Locating and protecting facilities from intentional attacks using secrecy. Reliab. Eng. Syst. Saf. 169:51–62
Jiang J and Liu X 2018 Multi-objective Stackelberg game model for water supply networks against interdictions with incomplete information. Eur. J. Oper. Res.. 266:920–933
Aksen D, Aras N and Piyade N 2013 A bilevel p-median model for the planning and protection of critical facilities. J. Heurist. 19:373–398
Aksen D and Aras N 2012 A bilevel fixed charge location model for facilities under imminent attack. Comput. Oper. Res. 39:1364–1381
Shishebori D, Jabalameli M S and Jabbarzadeh A 2013 Facility location-network design problem: reliability and investment budget constraint. J. Urban Plan. Dev.. 140(3):04014005
Rocco C, Ramirez-Marquez J, Salazar D and Hernandez I 2010 Implementation of multi-objective optimization for vulnerability analysis of complex networks. Proc. Inst. Mech. Eng. O J. Risk Reliab. 224:87–95.
Royset J O and Wood R K 2007 Solving the bi-objective maximum-flow network-interdiction problem. IINFORMS J. Comput.. 19:175–184
Ramirez-Marquez J E 2010 A bi-objective approach for shortest-path network interdiction. Comput. Ind. Eng. 59:232–240
Parvaresh F, Husseini S M, Golpayegany S H and Karimi B 2014 Hub network design problem in the presence of disruptions. J. Intell. Manuf. 25:755–774
Farmani R, Walters G A and Savic D A 2005 Trade-off between total cost and reliability for Anytown water distribution network. J. Water Resour. Plan. Manag. 131:161–171
Brown G, Carlyle M, Salmerón J and Wood K 2006 Defending critical infrastructure. Interfaces. 36:530–544
Brown G G, Carlyle W M, Salmeron J and Wood K 2005 Analyzing the vulnerability of critical infrastructure to attack and planning defenses. INFORMS TutORials Oper. Res., 102–123
Wood R K 2010 Bilevel network interdiction models: Formulations and solutions. Wiley Encyclopedia of Operations Research and Management Science. New York: Wiley
Towle E and Luedtke J 2018 New solution approaches for the maximum-reliability stochastic network interdiction problem. Comput. Manag. Sci. 15:455–477
Losada C, Scaparra M P, Church R L and Daskin M S 2012 The stochastic interdiction median problem with disruption intensity levels. Ann. Oper. Res. 201:345–365
Li Q and Savachkin A 2016 Reliable distribution networks design with nonlinear fortification function. Int. J. Syst. Sci. 47:805–813
Berman O, Krass D and Menezes M B 2007 Facility reliability issues in network p-median problems: strategic centralization and co-location effects. Oper. Res. 55:332–350.
Cui T, Ouyang Y and Shen Z -J M 2010 Reliable facility location design under the risk of disruptions. Oper. Res. 58:998–1011.
Lei T L and Tong D 2013 Hedging against service disruptions: an expected median location problem with site-dependent failure probabilities. J. Geograph. Syst.. 15:491–512
Lim M, Daskin M S, Bassamboo A and Chopra S 2010 A facility reliability problem: formulation, properties, and algorithm. Naval Res. Log. 57:58–70
Ukkusuri S and Yushimito W 2008 Location routing approach for the humanitarian prepositioning problem. Transp. Res. Rec.: J. Transp. Res. Board.. 2089(1):18-25
Shen Z -J M, Zhan R L and Zhang J 2011 The reliable facility location problem: Formulations, heuristics, and approximation algorithms. INFORMS J. Comput. 23:470–482.
Hatefi S and Jolai F 2014 Robust and reliable forward–reverse logistics network design under demand uncertainty and facility disruptions. v 38:2630–2647
Akgün İ, Gümüşbuğa F and Tansel B 2015 Risk based facility location by using fault tree analysis in disaster management. Omega 52:168–179
An Y, Zeng B, Zhang Y and Zhao L 2014 Reliable p-median facility location problem: two-stage robust models and algorithms. Transp Res.B: Methodol. 64:54–72
Baghalian A, Rezapour S and Farahani R Z 2013 Robust supply chain network design with service level against disruptions and demand uncertainties: A real-life case. Eur. J. Oper. Res. 227:199–215
Vahdani B, Tavakkoli-Moghaddam R and Jolai F 2013 Reliable design of a logistics network under uncertainty: A fuzzy possibilistic-queuing model. Appl. Math. Model. 37:3254–3268
Zarrinpoor N, Fallahnezhad M S and Pishvaee M S 2017 Design of a reliable hierarchical location-allocation model under disruptions for health service networks: A two-stage robust approach. Comput. Ind. Eng. 109:130–150
Azizi N, Chauhan S, Salhi S and Vidyarthi N 2016 The impact of hub failure in hub-and-spoke networks: Mathematical formulations and solution techniques. Comput. Oper. Res. 65:174-188
Mohammadi M, Tavakkoli-Moghaddam R, Siadat A and Dantan J -Y 2016 Design of a reliable logistics network with hub disruption under uncertainty. Appl. Math. Model. 40:5621-5642
Lei T L 2013 Identifying critical facilities in hub-and-spoke networks: a hub interdiction median problem. Geograph. Anal. 45:105–122
Azad N, Saharidis G K, Davoudpour H, Malekly H and Yektamaram S A 2013 Strategies for protecting supply chain networks against facility and transportation disruptions: an improved Benders decomposition approach. Ann. Oper. Res. 210:125-163
Peng P, Snyder L V, Lim A and Liu Z 2011 Reliable logistics networks design with facility disruptions. Transp Res. B: Methodol. 45:1190–1211
Yu R 2015 The Capacitated Reliable Fixed-charge Location Problem: Model and Algorithm. Master of Science Degree, Lehigh University, Bethlehem, PA
Salmerón J 2012 Deception tactics for network interdiction: A multiobjective approach. Networks: An International Journal 60:45–58
Donald D and Herbig K 1981 Strategic military deception. New York:Pergamon Press
Vollmer T and Manic M 2014 Cyber-physical system security with deceptive virtual hosts for industrial control networks. IEEE Trans. Ind. Inf.. 10:1337–1347
. Jeon S, Yun J -H and Kim W -N 2014 Obfuscation of critical infrastructure network traffic using fake communication, In: Proceedings of the International Conference on Critical Information Infrastructures Security, pp. 268–274
Teixeira A, Amin S, Sandberg H, Johansson K H and Sastry S S 2010 Cyber security analysis of state estimators in electric power systems, In: Proceedings of the 49th IEEE Conference on Decision and Control (CDC), pp. 5991–5998
Amoroso E G 2012 Cyber attacks: protecting national infrastructure. MA: Elsevier
Rauti S and Leppanen V 2017 A survey on fake entities as a method to detect and monitor malicious activity, In: Proceedings of the 25th Euromicro International Conference on Parallel, Distributed and Network-based Processing (PDP), pp. 386–390
Hamidi M R, Gholamian M R and Shahanaghi K 2014 Developing prevention reliability in hub location models. Proc. Inst. Mech. Eng. O J. Risk Reliab.. 228:337–346
Hamidi M R, Gholamian M R, Shahanaghi K and Yavari A 2017 Reliable warehouse location-network design problem under intentional disruption. Comput. Ind. Eng. 113:123–134
Crowdy T 2011 Deceiving Hitler: Double-Cross and Deception in World War II. New York: Osprey Publishing
Chaturvedi S K 2016 Network reliability: measures and evaluation. New York: Wiley.
Ross S 2018 A first course in probability. 10th edn, New York: Pearson
Marler RT and Arora J S 2004 Survey of multi-objective optimization methods for engineering. Struct. Mmultidiscipl. Optim.. 26:369–395
Deb K 2001 Multi-objective optimization using evolutionary algorithms. New York: Wiley.
Zavala G R, Nebro A J, Luna F and Coello C A C 2014 A survey of multi-objective metaheuristics applied to structural optimization. Struct. Mmultidiscipl. Optim. 49:537–558
Mogale D, Kumar M, Kumar S K and Tiwari M K 2018 Grain silo location-allocation problem with dwell time for optimization of food grain supply chain network. Transp. Res. E: Log. Transp. Rev.. 111:40–69
Mogale D, Kumar S K and Tiwari M K 2016 Two stage Indian food grain supply chain network transportation-allocation model. IFAC-PapersOnLine. 49(12):1767–1772
Bottani E, Murino T, Schiavo M and Akkerman R 2019 Resilient food supply chain design: Modelling framework and metaheuristic solution approach. Comput. Ind. Eng.. 135: 177–198
Mogale D, Dolgui A, Kandhway R, Kumar S K and Tiwari M K 2017 A multi-period inventory transportation model for tactical planning of food grain supply chain. Comput. Ind. Eng.. 110:379–394
Ghaffarinasab N and Motallebzadeh A 2018 Hub interdiction problem variants: Models and metaheuristic solution algorithms. Eur. J. Oper. Res.. 267:496–512.
Kheirkhah A, Navidi H and Bidgoli M M 2016 An improved benders decomposition algorithm for an arc interdiction vehicle routing problem. IEEE Trans. Eng. Manag. 63:259–273
Mavrotas G 2009 Effective implementation of the ε-constraint method in multi-objective mathematical programming problems. Appl. Math. Comput.. 213:455–465.
Beasley J E 1988 An algorithm for solving large capacitated warehouse location problems. Eur. J. Oper. Res. 33:314–325
Coello C A C, Lamont G B and Van Veldhuizen D A 2007 Evolutionary algorithms for solving multi-objective problems. New York: Springer
Author information
Authors and Affiliations
Corresponding author
Appendix A. Date set 1, small size data set
Appendix A. Date set 1, small size data set
Potential locations for warehouses | Demand | |||||||
|---|---|---|---|---|---|---|---|---|
1 | 2 | 3 | 4 | 5 | 6 | 7 | ||
Demand nodes | ||||||||
1 | 7280 | 2920 | 8240 | 4420 | 3900 | 2574 | 6248 | 10000 |
2 | 2040 | 8510 | 3400 | 15360 | 7563 | 4228 | 23010 | 5000 |
3 | 6280 | 7540 | 2310 | 12300 | 10315 | 11598 | 12881 | 4000 |
4 | 5120 | 4110 | 11990 | 10630 | 14065 | 16506 | 18947 | 1000 |
5 | 3960 | 680 | 1670 | 8960 | 17815 | 6953 | 2501 | 3000 |
6 | 5500 | 1520 | 5965 | 6595 | 11066 | 5485 | 8922 | 6000 |
7 | 4600 | 821 | 7545 | 8711 | 4487 | 1410 | 7544 | 2000 |
Real fixed cost | 3.5× 1010 | 5×1010 | 6×1010 | 8×1010 | 8.5×1010 | 9.5×1010 | 9.9×1010 | |
Dummy fixed cost | 3.5×108 | 5×108. | 6×108 | 8×108 | 8.5×108 | 9.5×108 | 9.9×108 | |
Rights and permissions
About this article
Cite this article
Hamidi, M.R., Gholamian, M.R. Optimizing warehouse network reliability under intentional disruption by increasing network ambiguity: a multi objective optimization model. Sādhanā 45, 76 (2020). https://doi.org/10.1007/s12046-020-1295-6
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12046-020-1295-6