Abstract
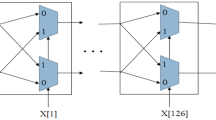
In order to reduce physical unclonable function (PUF) response instability and imbalance caused by the metastability and the bias of arbiter, this paper uses an improved balanced D flip-plop (DFF) based on the unbalanced DFF to reduce the bias in response output and enhances the security of PUF by adopting two balanced DFFs in series. The experimental results show that two cascaded balanced DFFs improve the stability of the DFF, and the output of two balanced DFFs is more reliable. The entropy of output is fixed at 98.7%.
Similar content being viewed by others
References
Capovilla J, Cortes M, Araujo G. Improving the statistical variability of delay-based physical unclonable functions [C] // Proc 28th Symposium on Integrated Circuits and Systems Design. New York: ACM Press, 2015: 1–7.
Bhargava M, Mai K. An efficient reliable PUF-based cryptographic key generator in 65 nm CMOS [C] // Proc 2014 Design, Automation & Test in Europe Conference & Exhibition. Washington D C: IEEE Press, 2014: 1–6.
Che W J, Saqib F, Plusquellic J. PUF-based authentication [C] // Proc IEEE/ACM International Conference on Computer-Aided Design. New York: ACM Press, 2015: 337–344.
Herrewege A V, Katzenbeisser S, Maes R, et al. Reverse fuzzy extractors: Enabling lightweight mutual authentication for PUF-enabled RFIDs [J]. Financial Cryptography and Data Security, 2012, 7397: 374–389.
Zhang J L, Wu Q, Lyu Y Q, et al. Design and implementation of a delay-based PUF for FPGA IP protection [C] // Proc 2013 International Conference on Computer-Aided Design and Computer Graphics. Washington D C: IEEE Press, 2013: 107–114.
Gao M Z, Lai K, Qu G. A highly flexible ring oscillator PUF [C] // Proc 51st Annual Design Automation Conference. New York: ACM Press, 2014: 1–6.
Guajardo J, Kumar S, Schrijen G, et al. FPGA intrinsic PUFs and their use for IP protection [C] // Proc 9th International Workshop on Cryptographic Hardware and Embedded Systems. Berlin: Springer-Verlag, 2007: 63–80.
Kumar S, Guajardo J, Maes R, et al. The butterfly PUF protecting IP on every FPGA [C] // Proc IEEE International Workshop on Hardware-Oriented Security and Trust. Washington D C: IEEE Press, 2008: 67–70.
Eichhorn I, Koeberl P, van der Leest V. Logically reconfigurable PUFs: Memory-based secure key storage [C] // Proc 6th ACM Workshop on Scalable Trusted Computing. New York: ACM Press, 2011: 59–64.
Hussain SU, Yellapantula S, Majzoobi M, et al. BIST-PUF: Online, hardware-based evaluation of physically unclonable circuit identifiers [C] // Proc 2014 IEEE/ACM International Conference on Computer-Aided Design. Washington D C: IEEE Press, 2014: 162–169.
Kang H, Hori Y, Katashita T, et al. Cryptographie key generation from PUF data using efficient fuzzy extractors [C] // Proc 16th International Conference on Advanced Communication Technology. Washington D C: IEEE Press, 2014: 23–26.
Cortez M, Roelofs G, Hamdioui S, et al. Testing PUF-based secure key storage circuits [C] // Proc Conference on Design, Automation & Test in Europe. Washington D C: IEEE Press, 2014: 1–6.
Gassend B, Clarke D E, Dijk M V, et al. Silicon physical random functions [C] // Proc 9th ACM Conference on Computer and Communications Security. New York: ACM Press, 2002: 148–160.
Suh G E, Devadas S. Physical unclonable functions for device authentication and secret key generation [C] // Proc 44th ACM/IEEE Design Automation Conference. Washington D C: IEEE Press, 2007: 9–14.
Majzoobi M, Koushanfar F, Devadas S. FPGA PUF using programmable delay lines [C] // Proc IEEE International Workshop on Information Forensics and Security. Washington D C: IEEE Press, 2010: 1–6.
Majzoobi M, Rostami M, Koushanfar F, et al. Slender PUF protocol: A lightweight, robust, and secure authentication by substring matching [C] // Proc IEEE Symposium on Security and Privacy Workshops. Washington D C: IEEE Press, 2012: 33–44.
Rührmair U, Sölter J. PUF modeling attacks: An introduction and overview [C] // Proc Conference on Design, Automation & Test in Europe. Washington D C: IEEE Press, 2014: 1–6.
Rührmair U, Sehnke F, Sölter J, et al. Modeling attacks on physical unclonable functions [C] // Proc 17th ACM Conference on Computer and Communications Security. New York: ACM Press, 2010: 237–249.
Rührmair U, Solter J, Sehnke F, et al. PUF modeling attacks on simulated and silicon data [J]. IEEE Transactions on Information Forensics and Security, 2013, 8(11): 1876–1891.
Chen D, Singh D, Chromczak J, et al. A comprehensive approach to modeling, characterizing and optimizing for metastability in FPGAs [C] // Proc 18th Annual ACM/SIGDA International Symposium on Field Programmable Gate Arrays. New York: ACM Press, 2010: 167–176.
Beer S, Ginosar R, Cox J, et al. Metastability challenges for 65 nm and beyond: Simulation and measurements [C] // Proc Conference on Design, Automation and Test in Europe. New York: ACM Press, 2013: 1297–1302.
Sannena G, Prasad B. A metastability immune timing error masking flip-flop for dynamic variation tolerance [C] // Proc 26th Edition on Great Lakes Symposium on VLSI. New York: ACM Press, 2016: 151–156.
Beer S, Cannizzaro M, Cortadella J, et al. Metastability in better-than-worst-case designs [C] // Proc 20th IEEE International Symposium on Asynchronous Circuits and Systems. Washington D C: IEEE Press, 2014: 101–102.
Cherif Z, Danger J L, Lozac H F, et al. Evaluation of delay PUFs on CMOS 65 nm technology: ASIC vs FPGA [C] // Proc 2nd International Workshop on Hardware and Architectural Support for Security and Privacy. New York: ACM Press, 2013: 1–8.
Rostami M, Majzoobi M, Koushanfar F, et al. Robust and reverse-engineering resilient PUF authentication and key-exchange by substring matching [J]. IEEE Transactions on Emerging Topics in Computing, 2014, 2(1): 374–389.
Majzoobi M, Koushanfar F, Potkonjak M. Testing techniques for hardware security [C] // Proc IEEE International Test Conference. Washington D C: IEEE Press, 2008: 1–10.
Ebeling C, How D, Lewis D, et al. Stratix™ 10 high performance routable clock networks [C] // Proc ACM/ SIGDA International Symposium on Field-Programmable Gate Arrays. New York: ACM Press, 2016: 64–73.
Konigsmark S T C, Hwang L K, Chen D, et al. System-of-PUFs: Multilevel security for embedded systems [C] // Proc International Conference on Hardware/Software Codesign and System Synthesis. Washington D C: IEEE Press, 2014: 1–10.
Kong J, Koushanfar F, Pendyala P K, et al. PUFatt: Embedded platform attestation based on novel processor-based PUFs [C] // Proc 51st Annual Design Automation Conference. New York: ACM Press, 2014: 1–6.
van den Berg R, Skoric B, van der Leest V. Bias-based modeling and entropy analysis of PUFs [C] // Proc 3rd International Workshop on Trustworthy Embedded Devices. New York: ACM Press, 2013: 13–20.
Yang B, Rožic V, Mentens N, et al. Embedded HW/SW platform for on-the-fly testing of true random number generators [C] // Proc 2015 Design, Automation & Test in Europe Conference & Exhibition. Washington D C: IEEE Press, 2015: 345–350.
Lewis D, Chiu G, Chromczak J, et al. The Stratix™ 10 highly pipelined FPGA architecture [C] // Proc ACM/SIGDA International Symposium on Field Programmable Gate Arrays. New York: ACM Press, 2016: 159–168.
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: Supported by the National Natural Science Foundation of China (41371402) and the Fundamental Research Funds for the Central Universities (2015211020201)
Biography: WANG Jun, male, Ph.D. candidate, research direction: information security and privacy in wireless / mobile networks.
Rights and permissions
About this article
Cite this article
Wang, J., Liu, S., Xiong, X. et al. Security enhancement of arbiter-based physical unclonable function on FPGA. Wuhan Univ. J. Nat. Sci. 22, 127–133 (2017). https://doi.org/10.1007/s11859-017-1225-6
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11859-017-1225-6
Key words
- physical unclonable function
- metastability
- balanced D flip-flop
- field programmable gate arrays (FPGA)
- security