Abstract
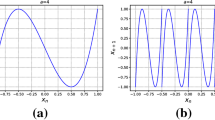
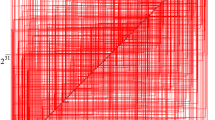
Wheeler pointed out that the period of Matthews’ chaotic function (MCF) is often too short to be suitable for cryptographic usage in the manner of computer statistics, but this statement was given only through digital computation. In this paper, we proved by theoretical and practical method that period exists in MCF and analyzed the underlying reason. With two chaotic functions working together we presented a modified MCF (MMCF) that is non-periodic. The simulation tests with reconstruction of phase space showed that our modified MCF is of no period. And we described how to implement a cryptographic usage with MMCF.
Similar content being viewed by others
References
Vernam G S. Cipher Printing Telegraph Systems for Secret Wire and Telegraphic Communications[J]. Journal American Inst Elec, 1926, 55: 109–115.
Tang Y S, Mees A I, Chua L O. Synchronization and Chaos[J]. IEEE Trans Circuits Sys, 1983, 30: 620–626.
Lorenz E N. Deterministic Nonperiodic Flow[J]. Journal of the Atmospheric Sciences, 1963, 20(2):130–141.
Li T Y, Yorke J A. Period Three Implies Chaos[J]. American Mathematical Monthly, 1975, 82: 985–992.
Auerbach D, Cvitanovic P, Eckmann J P, et al. Exploring Chaotic Motion through Periodic Orbits[J]. Phys Rev Lett, 1987, 58(6): 2387–2389.
Pecora L M, Corroll T L. Synchronization in Chaotic Systems[J]. Phys Rev Lett, 1990, 64(8): 821–824.
Wheeler D D. Problems with Chaotic Cryptosystems [J]. Cryptologia, 1989, 13: 243–250.
Matthews R. On the Derivation of a “Chaotic” Encryption Algorithm [J]. Cryptologia, 1989, 13: 29–42.
Perez G, Cerderia H A. Extracting Messages Masked by Chaos [J]. Phys Rev Lett, 1995, 74(11): 1970–1973.
Zhou Xueguang. The Proof of Period of Two Kinds of Chaotic Functions[C]//Proceedings of 2000 Chinese Control and Decision Conference, Shenyang: Northeast University Press, 2000: 39–42 (Ch).
Packard N H, Crutchfield J P, Farmer J D, et al. Geometry from a Time Series[J]. Phys Rev Lett, 1980, 45(9): 712–715.
Takens F. Detecting Strange Attractors in Turbulence [J]. Lecture Notes in Mathematica, 1981, 898: 366–381.
Liu Bingzheng, Peng Jianhua. Nonlinear Dynamics[M]. Beijing: High Education Press, 2003: 389(Ch).
Huang Benwen, LÜ Yuxiang, Liao Xiangjun. Quick Trickle Permutation [J]. J Wuhan Univ (Nat Sci Ed), 2003, 49(5): 589–591(Ch).
Luo Qibin, Zhang Jian, Zhou Jie. Complexity Analysis of the Chaotic Key Sequence[C]//Advances in Cryptology-CHINACRYPT’ 2006. Beijing: China Science and Technology Press. 2006: 110–114(Ch).
Roman S. Coding and Information Theory [M]. New York: Springer-Verlag, 1992.
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: Supported by the National Natural Science Foundation of China (60673071)
Rights and permissions
About this article
Cite this article
Zhou, X., Zhang, H. A new chaotic function and its cryptographic usage. Wuhan Univ. J. Nat. Sci. 13, 557–561 (2008). https://doi.org/10.1007/s11859-008-0509-2
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11859-008-0509-2
Key words
- chaos
- period
- Matthews’ chaotic function (MCF)
- modified Matthews’ chaotic function (MMCF)
- reconstruction of phase space (RPS)
- variable-structure attractor
- invariable-structure attractor