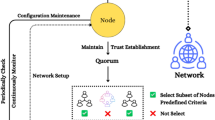
Abstract
In P2P Grid computing systems, the authorization decision is often tackled by two different trust management methods: policy-based approach, where authorization are built on logical rules and verifiable properties encoded in signed credentials, and reputation-based approach, based on collecting, aggregating and disseminating reputation among the peers. However, the overhead caused by proof of compliance on authorization and the absence of certifying authorities may negate the strong and objective security advantages of policy-based approach, whilst vagueness, complexity and inaccurate characterization caused by reputation evolution may eliminate the quantitative and flexible advantages of reputation-based approach. We propose an adaptive trust management framework, which combines the merit of policy proof and reputation evolution such that authorization is aware of not only the strong and objective security traits, but also the calculability and the availability security traits. Finally, the framework of system is proposed.
Similar content being viewed by others
References
Berman F, Fox G, Hey T. Grid Computing: Making the Global Infrastructure a Reality [M]. London: John Wiley & Sons Press, 2003.
Ren S, Guo L, Jiang S. SAT-Match: A Self-Adaptive Topology Matching Method to Achieve Low Lookup Latency in Structured P2P Overlay Networks[C]// Proc of the 18th Int’l Parallel and Distributed Processing Symp (IPDPS 2004). New York: IEEE Press, 2004: 83–91.
Grandison T. Trust Management for Internet Applications [D]. London: Imperial College, 2003.
Kamvar S D, Schlosser M T, Garcia-Molina H. Eigenrep: Reputation Management in P2P Networks[C]// Proc of 12th International www Conference, New York: ACM Press, 2003: 640–651.
Li Ninghui, Winsborough W H, Mitchell J C. Beyond Proof-of-Compliance: Safety and Availability Analysis in Trust Management[C]// Proceedings of IEEE Symposium on Security and Privacy, Oakland, California, 2003: 123–139.
Blaze M, Feigenbaum J, Lacy J. Decentralized Trust Management[C]//Proceedings of the 17th Symposium on Security and Privacy. Okaland: IEEE Computer Society Press, 1996: 164–173.
Staab S, Bhargava B K, Lilien L, et al. The Pudding of Trust. IEEE Intelligent Systems[J], 2004, 19(5): 74–88.
Grandison T, Sloman M. Specifying and Analyzing Trust for Internet Applications in Towards the Knowledge Society: eCommerce, eBusiness, and eGovernment[C]//The Second IFIP Conference on E-Commerce, E-Business, E-Government (I3E 2002), New York: Springer, 2002: 145–157.
Beth T, Borcherding M, Klein B. Valuation of Trust in Open Networks[C]//Proceedings of the European Symposium on Research in Security (ESORICS). Brighton: Springer-Verlag, 1994:3–18.
Dimmock N, Belokosztolszki A, Eyers D. Using Trust and Risk in Role-Based Access Control Policies [C]//Proceedings of the Ninth ACM Symposium on Access Control Models and Technologies (SACMAT). New York: ACM Press, 2004: 156–162.
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: Supported by the Open Research Foundation of National Key Laboratory (SKLSE04-018), National Social Science Foundation of China (06BTQ024) and the Science and Technical Key Project of Hubei Province (2005AA101C43)
Biography: WANG Yinglong(1958–), male, Ph.D. candidate, research direction: computer network & information security
Rights and permissions
About this article
Cite this article
Wang, Y., Hu, J. Adaptive trust management framework in P2P grid computing. Wuhan Univ. J. Nat. Sci. 13, 33–36 (2008). https://doi.org/10.1007/s11859-008-0107-3
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11859-008-0107-3