Abstract
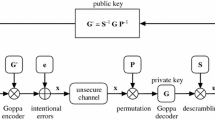
We cryptanalyse here two variants of the McEliece cryptosystem based on quasi-cyclic codes. Both aim at reducing the key size by restricting the public and secret generator matrices to be in quasi-cyclic form. The first variant considers subcodes of a primitive BCH code. The aforementioned constraint on the public and secret keys implies to choose very structured permutations. We prove that this variant is not secure by producing many linear equations that the entries of the secret permutation matrix have to satisfy by using the fact that the secret code is a subcode of a known BCH code. This attack has been implemented and in all experiments we have performed the solution space of the linear system was of dimension one and revealed the permutation matrix. The other variant uses quasi-cyclic low density parity-check (LDPC) codes. This scheme was devised to be immune against general attacks working for McEliece type cryptosystems based on LDPC codes by choosing in the McEliece scheme more general one-to-one mappings than permutation matrices. We suggest here a structural attack exploiting the quasi-cyclic structure of the code and a certain weakness in the choice of the linear transformations that hide the generator matrix of the code. This cryptanalysis adopts a polynomial-oriented approach and basically consists in searching for two polynomials of low weight such that their product is a public polynomial. Our analysis shows that with high probability a parity-check matrix of a punctured version of the secret code can be recovered with time complexity O(n 3) where n is the length of the considered code. The complete reconstruction of the secret parity-check matrix of the quasi-cyclic LDPC codes requires the search of codewords of low weight which can be done with about 237 operations for the specific parameters proposed.
Similar content being viewed by others
References
Baldi, M., Chiaraluce, G.F.: Cryptanalysis of a new instance of McEliece cryptosystem based on QC-LDPC codes. In: IEEE International Symposium on Information Theory, pp. 2591–2595, Nice, France, March 2007
Berger T.P., Loidreau P.: How to mask the structure of codes for a cryptographic use. Des. Codes Cryptography 35(1), 63–79 (2005)
Berlekamp E.R., McEliece R.J., van Tilborg H.C.A.: On the intractability of certain coding problems. IEEE Trans. Inf. Theory 24(3), 384–386 (1978)
Berstein, D.J., Lange, T., Peters, C.: Attacking and defending the McEliece cryptosystem. PQCrypto, pp. 31–46 (2008)
Bosma W., Cannon J.J., Playoust C.: The Magma algebra system I: the user language. J. Symb. Comput. 24(3/4), 235–265 (1997)
Canteaut, A., Chabanne, H.: A further improvement of the work factor in an attempt at breaking McEliece’s cryptosystem. In: EUROCODE 94, pp. 169–173. INRIA (1994)
Canteaut, A., Chabaud, F.: Improvements of the attacks on cryptosystems based on error-correcting codes. Technical Report 95-21, INRIA (1995)
Canteaut A., Chabaud F.: A new algorithm for finding minimum-weight words in a linear code: application to McEliece’s cryptosystem and to narrow-sense BCH codes of length 511. IEEE Trans. Inf. Theory 44(1), 367–378 (1998)
Cayrel, P.L., Otmani, A., Vergnaud, D.: On Kabatianskii-Krouk-Smeets signatures. In: Proceedings of the First International Workshop on the Arithmetic of Finite Fields (WAIFI 2007). Springer Verlag Lecture Notes, pp. 237–251, Madrid, Spain, 21–22 June 2007
Engelbert D., Overbeck R., Schmidt A.: A summary of McEliece-type cryptosystems and their security. J. Math. Cryptol. 1, 151–199 (2007)
Gabidulin, E.M.: Public-Key Cryptosystems Based on Linear Codes. 1995
Gaborit, P.: Shorter keys for code based cryptography. In: Proceedings of the 2005 International Workshop on Coding and Cryptography (WCC 2005), pp. 81–91, Bergen, Norway, March 2005
Gaborit, P., Girault, M.: Lightweight code-based authentication and signature. In: IEEE International Symposium on Information Theory (ISIT 2007), pp. 191–195, Nice, France, March 2007
Gaborit, P., Lauradoux, C., Sendrier, N.: Synd: a fast code-based stream cipher with a security reduction. In: IEEE International Symposium on Information Theory (ISIT 2007), pp. 186–190, Nice, France, March 2007
Lee, P.J., Brickell, E.F.: An observation on the security of McEliece’s public-key cryptosystem. In: Advances in Cryptology—EUROCRYPT’88, volume 330/1988 of Lecture Notes in Computer Science, pp. 275–280. Springer, New York (1988)
Leon J.S.: A probabilistic algorithm for computing minimum weights of large error-correcting codes. IEEE Trans. Inf. Theory 34(5), 1354–1359 (1988)
Li Y.X., Deng R.H., Wang X.-M.: On the equivalence of McEliece’s and Niederreiter’s public-key cryptosystems. IEEE Trans. Inf. Theory 40(1), 271–273 (1994)
McEliece, R.J.: A Public-Key System Based on Algebraic Coding Theory, pp. 114–116. DSN Progress Report 44. Jet Propulsion Lab (1978)
Minder, L., Shokrollahi, A.: Cryptanalysis of the Sidelnikov cryptosystem. In: Eurocrypt 2007, Lecture Notes in Computer Science, vol. 4515, pp. 347–360, Barcelona, Spain (2007)
Niederreiter H.: Knapsack-type cryptosystems and algebraic coding theory. Probl. Control Inf. Theory 15(2), 159–166 (1986)
Pless, V.S., Huffman, W.C. (eds.): Handbook of Coding Theory. North Holland (1998)
Sendrier N.: On the concatenated structure of a linear code. AAECC 9(3), 221–242 (1998)
Shokrollahi, A., Monico, C., Rosenthal, J.: Using low density parity check codes in the McEliece cryptosystem. In: IEEE International Symposium on Information Theory (ISIT 2000), p. 215, Sorrento, Italy (2000)
Sidelnikov V.M.: A public-key cryptosystem based on binary Reed-Muller codes. Discrete Math. Appl. 4(3), 191–207 (1994)
Sidelnikov V.M., Shestakov S.O.: On the insecurity of cryptosystems based on generalized Reed-Solomon codes. Discrete Math. Appl. 1(4), 439–444 (1992)
Stern, J.: A method for finding codewords of small weight. In: Cohen, G.D., Wolfmann, J. (eds.) Coding Theory and Applications, volume 388 of Lecture Notes in Computer Science, pp. 106–113. Springer, New York (1988)
Wieschebrink, C.: An Attack on a Modified Niederreiter Encryption Scheme. Public Key Cryptography—PKC 2006, Lecture Notes in Computer Science, vol. 3958/2006, pp. 14–26. Springer, New York (2006)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Otmani, A., Tillich, JP. & Dallot, L. Cryptanalysis of Two McEliece Cryptosystems Based on Quasi-Cyclic Codes. Math.Comput.Sci. 3, 129–140 (2010). https://doi.org/10.1007/s11786-009-0015-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11786-009-0015-8