Abstract
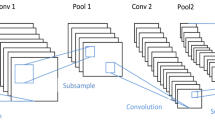
Face anti-spoofing is a relatively important part of the face recognition system, which has great significance for financial payment and access control systems. Aiming at the problems of unstable face alignment, complex lighting, and complex structure of face anti-spoofing detection network, a novel method is presented using a combination of convolutional neural network and brightness equalization. Firstly, multi-task convolutional neural network (MTCNN) based on the cascade of three convolutional neural networks (CNNs), P-net, R-net, and O-net are used to achieve accurate positioning of the face, and the detected face bounding box is cropped by a specified multiple, then brightness equalization is adopted to perform brightness compensation on different brightness areas of the face image. Finally, data features are extracted and classification is given by utilizing a 12-layer convolution neural network. Experiments of the proposed algorithm were carried out on CASIA-FASD. The results show that the classification accuracy is relatively high, and the half total error rate (HTER) reaches 1.02%.
摘要
人脸活体检测是人脸识别系统中比较重要的一环, 对金融支付、门禁系统等具有重大意义。针 对人脸对齐不稳定、复杂光照、活体检测网络结构复杂等问题, 论文提出使用卷积神经网络和亮度均 衡结合的方法。论文首先使用基于P-net, R-net, O-net 三个CNN 进行级联的MTCNN 算法, 实现对 人脸的精准定位并将检测出的人脸边界框按指定倍数裁剪人脸, 接下来使用亮度均衡对人脸图像不同 亮度区域进行亮度补偿, 最后使用一个设计的12 层卷积神经网络提取数据特征并进行分类。论文将 所提算法在CASIA-FASD 上进行实验, 结果表明分类准确率比较高, HTER 达到了1.02%。
Similar content being viewed by others
References
RAMACHANDRA R, BUSCH C. Presentation attack detection methods for face recognition systems: A comprehensive survey [J]. ACM Computing Surveys (CSUR), 2017, 50(1): 1–37. DOI: https://doi.org/10.1145/3038924.
ZHANG C, GU Y, HU K, WANG Y G. Face recognition using SIFT features under 3D meshes [J]. Journal of Central South University, 2015, 22(5): 1817–1825. DOI: https://doi.org/10.1007/s11771-015-2700-x.
MEHRASA N, ALI A, HOMAYUN M. A supervised multimanifold method with locality preserving for face recognition using single sample per person [J]. Journal of Central South University, 2017, 24(12): 2853–2861. DOI: https://doi.org/10.1007/s11771-017-3700-9.
MAATTA J, HADID A, PIEKIKAINEN M. Face spoofing detection from single images using micro-texture analysis [C]//2011 International Joint Conference on Biometrics (IJCB). Washington: IEEE, 2011: 1–7. DOI: https://doi.org/10.1109/IJCB.2011.6117510.
TAN X, LI Y, LIU J, LIN J. Face liveness detection from a single image with sparse low rank bilinear discriminative model [C]//European Conference on Computer Vision. Berlin, Heidelberg: Springer, 2010: 504–517. DOI: https://doi.org/10.5555/1888212.1888251.
de FREITAS P T, ANJOS A, de MARTINO J M, MARCEL S. Can face anti-spoofing countermeasures work in a real world scenario? [C]//2013 International Conference on Biometrics (ICB). Madrid: IEEE, 2013: 1–8. DOI: https://doi.org/10.1109/ICB.2013.6612981.
CHINGOVSKA I, ANJOS A, MARCEL S. On the effectiveness of local binary patterns in face anti-spoofing [C]//2012 BIOSIG-Proceedings of the International Conference of Biometrics Special Interest Group (BIOSIG). Darmstadt: IEEE, 2012: 1–7. https://ieeexplore.ieee.org/document/6313548.
KOLLREIDER K, FRONTHAREL H, FARAJ M I, BIGUN J. Real-time face detection and motion analysis with application in “liveness” assessment [J]. IEEE Transactions on Information Forensics and Security, 2007, 2(3): 548–558. DOI: https://doi.org/10.1109/TIFS.2007.902037.
de MARSICO M, NAPPI M, RICCIO D, DUGELAY J. Moving face spoofing detection via 3D projective invariants [C]//5th IAPR International Conference on Biometrics (ICB). New Delhi: IEEE, 2012: 73–78. DOI: https://doi.org/10.1109/ICB.2012.6199761.
PAVLIDIS I, SYMOSEK P. The imaging issue in an automatic face/disguise detection system [C]//Proceedings IEEE Workshop on Computer Vision Beyond the Visible Spectrum: Methods and Application (Cat. No. PR00640). South Carolina: IEEE, 2000: 15–24. DOI: https://doi.org/10.1109/CVBVS.2000.855246.
YANG J, LEI Z, LI S Z. Learn convolutional neural network for face anti-spoofing [J]. Computer Science, 2014, 9218: 373–384. https://arxiv.org/abs/1408.5601.
LIU Y, JOURABLOO A, LIU X. Learning deep models for face anti-spoofing: Binary or auxiliary supervision [C]//Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition 2018. Salt Lake City: IEEE, 2018: 389–398. DOI: https://doi.org/10.1109/CVPR.2018.00048.
ATOUM Y, LIU Y, JOURABLOO A, LIU X. Face anti-spoofing using patch and depth-based CNNs [C]//2017 IEEE International Joint Conference on Biometrics (IJCB). Denver: IEEE, 2017: 319–328. DOI: https://doi.org/10.1109/BTAS.2017.8272713.
REHMAN Y A U, PO L M, LIU M. Deep learning for face anti-spoofing: An end-to-end approach [C]//2017 Signal Processing: Algorithms, Architectures, Arrangements, and Applications (SPA). Poznan: IEEE, 2017: 195–200. DOI: https://doi.org/10.23919/SPA.2017.8166863.
VIOLA P, JONES M J. Robust real-time face detection [J]. International Journal of Computer Vision, 2004, 57(2): 137–154. DOI: https://doi.org/10.1023/VISI.B:0000013087.49260.fb.
ZHANG K, ZHANG Z, LI Z, QIAO Y. Joint face detection and alignment using multitask cascaded convolutional networks [J]. IEEE Signal Processing Letters, 2016, 23(10): 1499–1503. DOI: https://doi.org/10.1109/LSP.2016.2603342.
PENG Xing-bang, JIANG Jian-guo. An image segmentation thresholding method based on luminance proportion [J]. Computer Technology and Development, 2006, 16(11): 10–12. DOI: https://doi.org/10.3969/j.issn.1673-629X.2006.11.004. (in Chinese)
ZHANG Z, YAN J, LIU S, LEI Z,YI D, LI S Z. A face antispoofing database with diverse attacks [C]//5th IAPR International Conference on Biometrics (ICB). New Delhi: IEEE, 2012: 26–31. DOI: https://doi.org/10.1109/ICB.2012.6199754.
XU Z, LI S, DENG W. Learning temporal features using LSTM-CNN architecture for face anti-spoofing [C]//2015 3rd IAPR Asian Conference on Pattern Recognition (ACPR). Kuala Lumpur: IEEE, 2015: 141–145. DOI: https://doi.org/10.1109/ACPR.2015.7486482.
LI L, FENG X, BOULKENAFET Z, XIA Z, LI M, HADID A. An original face anti-spoofing approach using partial convolutional neural network [C]//Sixth International Conference on Image Processing Theory, Tools and Applications (IPTA). Oulu: IEEE, 2016: 1–6. DOI: https://doi.org/10.1109/IPTA.2016.7821013.
GAN J, LI S, ZHAI Y, LIU C. 3d convolutional neural network based on face anti-spoofing [C]//2nd international conference on multimedia and image processing (ICMIP). Wuhan: IEEE, 2017: 1–5. DOI: https://doi.org/10.1109/ICMIP.2017.9.
Author information
Authors and Affiliations
Contributions
CAI Pei provided the concept, established the models and analyzed experimental results. QUAN Hui-min wrote the initial draft of the manuscript. Both authors replied to reviewers’ comments and revised the final version.
Corresponding author
Additional information
Conflict of interest
CAI Pei and QUAN Hui-min declare that they have no conflict of interest.
Foundation item
Project(61671204) supported by National Natural Science Foundation of China; Project(2016WK2001) supported by Hunan Provincial Key R & D Plan, China
Rights and permissions
About this article
Cite this article
Cai, P., Quan, Hm. Face anti-spoofing algorithm combined with CNN and brightness equalization. J. Cent. South Univ. 28, 194–204 (2021). https://doi.org/10.1007/s11771-021-4596-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11771-021-4596-y