Abstract
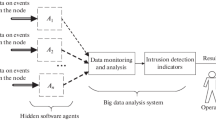
Static secure techniques, such as firewall, hierarchy filtering, distributed disposing, layer management, autonomy agent, secure communication, were introduced in distributed intrusion detection. The self-protection agents were designed, which have the distributed architecture, cooperate with the agents in intrusion detection in a loose-coupled manner, protect the security of intrusion detection system, and respond to the intrusion actively. A prototype self-protection agent was implemented by using the packet filter in operation system kernel. The results show that all the hosts with the part of network-based intrusion detection system and the whole intrusion detection system are invisible from the outside and network scanning, and cannot apperceive the existence of network-based intrusion detection system. The communication between every part is secure. In the low layer, the packet streams are controlled to avoid the buffer leaks existing in some system service process and back-door programs, so as to prevent users from misusing and vicious attack like Trojan Horse effectively.
Similar content being viewed by others
References
Edward G A. Intrusion detection: An introduction to internet surveillance, correlation, trace back, and response[M]. Alaska: IEEE Press, 1999. 123–128.
Heady R, Luger G, Hofmeyr A, et al. Computer immunology[J]. Communications of the ACM, 1997 (10):88–96.
Biswanath M, Tood L H, Karl N L. Network intrusion detection[J]. IEE Network, 1994, 8(3): 26–41.
Herve D, Marc D, Andreas W, Towards a taxonomy of intrusion-detection systems [J]. Computer Networks, 1999, 31:805–822.
HUANG Chen-lin, ZHAO Hui, HU Hua-ping. Distributed autonomous agent based layered intrusion detection system design [J]. Computer Application, 2001, (4):110–121.
Wenke L, Salvatore J S. Data mining approaches for intrusion detection[A]. 7th USENIX Security Symposium (SECURITY98)[C], San Diego, 1998. 88–98.
HE Yan-xiang, SHI Li, ZHANG Ge. Algorithms of discovering association rules and their tradeoffs[J]. Mini-micro system, 2001,22(9):78–99.
Jai S B, Jose O G F, David I, et al. An architecture for intrusion detection using autonomous agents[A]. COAST Technical Report [C]. Santa Monica, 1998: 128–137.
Brenda M A, Paul R, Intrusion detection technology: Today and Tomorrow[A]. 12th Annual First Conference[C]. Chicago, 2000:177–196.
Stephen N. Network intrusion detection an analyst’s handbook[M]. Beijing: Peoples Posts & Telecommunications Publishing House, 2000:207–219.
Author information
Authors and Affiliations
Additional information
Foundation item: Hi-tech Research and Development Program of China(No. 863-306-ZT05-05-6)
Biography of the first author: ZHU Shu-ren, associate professor, born in June 1964, majoring in computer network security.
Rights and permissions
About this article
Cite this article
Zhu, Sr., Li, Wq. Design and implementation of self-protection agent for network-based intrusion detection system. J Cent. South Univ. Technol. 10, 69–73 (2003). https://doi.org/10.1007/s11771-003-0073-z
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11771-003-0073-z
Key words
- intrusion detection system (IDS)
- network-based intrusion detection system (NIDS)
- self-protection agent
- IP filter