Abstract
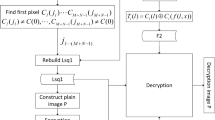
Under Kerckhoff principle, this paper discusses the security property of an image encryption scheme with a pseudorandom permutation. Some findings on the security problems of the algorithm are reported in the following: (1) If each row or column of the plain-image matrix is the same, the receiver cannot decrypt correctly. (2) Each plain-text word is correlated with single cipher-text word, but independent of other cipher-text word, which cannot meet the principles of algorithm design-diffusion and confusion. (3) If the cycle numbers β are relatively small, statistics attack can be used to reveal some visual information of any other plain-images encrypted with the same secret key. Considering the above problems, we propose an improved algorithm and then analyze its performance. Theoretical analysis and simulation results show that the improved algorithm can obtain better cryptographic properties, such as statistical characteristics, difference characteristics, and so on.
Similar content being viewed by others
References
J. H. Park. Inner-product encryption under standard assumptions. Designs, Codes and Cryptography, 58 (2011)3, 235–257.
E. Rueda, M. Tebaldi, and R. Torroba. Three-dimensional key in a modified joint transform correlator encryption scheme. Optics Communications, 284(2011) 19, 4321–4326.
S. K. Au Yeung, S. Y. Zhu, and B. Zeng. Partial video encryption based on alternating transforms. IEEE Transactions on Signal Processing Letters, 16(2009) 10, 893–896.
B. Libert and D. Vergnaud. Unidirectional chosenciphertext secure proxy re-encryption. IEEE Transactions on Information Theory, 57(2011)3, 1786–1802.
H. M. Sun, M. E. Wu, and M. J. Hinek. Trading decryption for speeding encryption in rebalanced-RSA. Journal of Systems and Software, 82(2009)9, 1503–1512.
D. Socek, S. Magliveras, and D. Culibrk. Digital video encryption algorithms based on correlation-preserving permutations. EURASIP Journal on Information Security, 2007(2007)1, 52965.
D. G. Yang, X. F. Liao, and Y. Wang. A novel block cryptosystem based on iterating map with output-feedback. Chaos, Solitons & Fractals, 41(2009)1, 505–510.
S. Peter, D. Westhoff, and C. Castelluccia. A survey on the encryption of converge cast traffic with in-network processing. IEEE Transactions on Dependable and Secure Computing, 7(2010)1, 20–34.
M. Amin, O. S. Faragallah, and A. A. Abd EL-Latif. A chaotic block cipher algorithm for image cryptosystems. Communications in Nonlinear Science and Numerical Simulation, 15(2010)11, 3484–3497.
J. Y. Chen, J. W. Zhou, and K. W. Wong. A modified chaos-based joint compression and encryption scheme. IEEE Transactions on Circuits and Systems II: Express Briefs, 58(2011)2, 110–114.
T. Xiang, X.F. Liao, and G.P. Tang. A novel block cryptosystem based on iterating a chaotic map. Physics Letters A, 349(2006)2, 109–115.
N. K. Pareek, V. Patidar, and K. K. Sud. Cryptography using multiple one-dimensional chaotic maps. Communications in Nonlinear Science and Numerical Simulation, 10(2005)8, 715–723.
N. K. Pareek, V. Patidar, and K. K. Sud. Image encryption using chaotic logistic map. Image and Vision Computing, 24(2006)9, 926–934.
C. Q. Li, S. J. Li, and G. Alvarez. Cryptanalysis of a chaotic block cipher with external key and its improved version. Chaos, Solitons & Fractals, 37(2008)1, 299–307.
J. A. Buchmann. Introduction to Cryptography. New York, Springer-Verlag, 2001, 35–273.
A. N. Pisarchik and M. Zanin. Image encryption with chaotically coupled chaotic maps. Physica D: Nonlinear Phenomena, 237(2008)20, 2638–2648.
F. J. Dyson and H. Falk. Period of a discrete cat mapping. The American Mathematical Monthly, 99 (1992)7, 603–614.
J. Fridrich. Symmetric ciphers based on two dimensionl chaotic maps. International Journal of Bifurcation and Chaos, 8(1998)6, 1259–1284.
T. G. Gao and Z. Q. Chen. A new image encryption algorithm based on hyper-chaos. Physics Letters A, 372(2008)4, 394–400.
R. Rhouma and S. Belghith. Cryptanalysis of a new image encryption algorithm based on hyper-chaos. Physics Letters A, 372(2008)38, 5973–5978.
J. W. Yoon and H. S. Kim. An image encryption scheme with a pseudorandom permutation based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation, 15(2010)12, 3998–4006.
C. S. Ding, F. W. Fu, and T. Klove. Constructions of permutation arrays. IEEE Transactions on Information Theory, 48(2002)4, 977–980.
C. E. Shannon. Communication theory of secrecy system. Bell System Technical Journal, 28(1949)4, 656–715.
Author information
Authors and Affiliations
Corresponding author
Additional information
Supported by the National Natural Science Foundation of China (No. 60874091), the Six Projects Sponsoring Talent Summits of Jiangsu Province (No. SJ209006), the Foundation for Doctoral Program of High Education of China (No. 20103223110003), the Natural Science Foundation of Jiangsu Province (No. 08KJD510022), and the Postgraduate Scientific Innovation Project for Universities of Jiangsu Province (No. CXZZ11-0401).
Communication author: Wang Jing, born in 1982, female, Ph.D..
About this article
Cite this article
Wang, J., Jiang, G. & Lin, B. Cryptanalysis of an image encryption scheme with a pseudorandom permutation and its improved version. J. Electron.(China) 29, 82–93 (2012). https://doi.org/10.1007/s11767-012-0800-4
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11767-012-0800-4