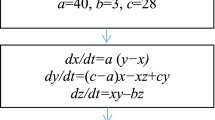Abstract
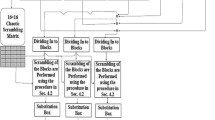
This letter presents a new type of chaotic encryption system based on combined chaotic mapping pseudo-random number generator, Hash table, and elliptic curve. In this program, the elliptic curve algorithm is used for the key distribution. After the linear transformation, the original chaotic sequence generated by drive system will be combined to chaotic mapping, converted to an encryption key sequence and constructed as Hash table for message authentication. The communication experiment used in the letter proves that the combination of combined chaotic encryption and conventional encryption is safe, feasible, and easy to implement by software.
Similar content being viewed by others
References
Li Nong and Li Jianfen. Generalized projective synchronization of chaotic system based on a single driving variable and it’s application in secure communication. Acta Physica Sinica, 57(2008)10, 6093–6097 (in Chinese). 李农, 李建芬. 基于单驱动变量的混沌广义投影同步及 在保密通信中的应用. 物理学报, 57(2008)10, 6093–6097.
Hu Jinfeng and Guo Jingbo. Breaking a chaotic direct sequence spreading spectrum secure communication system. Acta Physica Sinica, 57(2008)3, 1477–1484 (in Chinese). 胡进峰, 郭静波. 一种破译混沌直接序列扩频保密通信 的方法. 物理学报, 57(2008)3, 1477–1484.
Kwok-Wo Wong, Sun-Wah Ho, and Ching-Ki Yung. A chaotic cryptography scheme for generating short ciphertext. Physics Letters A, 42(2003)9, 193–197.
Kwok-Wo Wong. A combined chaotic cryptographic and hashing scheme. Physics Letters A, 42(2003)10, 93–102.
Yang Yang and Jin Chenhui. Known-plaintext attack on chaotic pseudo-random sequence generator. Computer Engineering, 33(2007)4, 146–148 (in Chinese). 杨阳, 金晨辉. 对一个混沌伪随机序列发生器的已知明 文攻击. 计算机工程, 33(2007)4, 146–148.
Sun Xiaohui, Lin Qiuhua, and Hao Yuwen. Pseudorandom number generator based on combined chaotic map. Chinese Journal of Scientific Instrument, 27 (2006)6, 805–807 (in Chinese). 孙晓辉, 林秋华, 郝育闻. 基于组合混沌映射的伪随机 数发生器. 仪器仪表学报, 27(2006)6, 805–807.
Sun Xiaohui and Lin Qiuhua. Improved pseudorandom number generator based on chaotic map with infinite collapses. Journal of Data Acquisition & Processing, 21(2006)7, 6–10 (in Chinese). 孙晓辉, 林秋华. 改进的无限折叠混沌映射伪随机数发 生器. 数据采集与处理, 21(2006)7, 6–10.
M. S. Baptista. Cryptography with chaos. Physics Letters A, 240(1998)6, 50–54.
Mi Bo, Liao Xiaofeng, and Chen Yong. Chaotic encryption system with the elliptic curve algorithm to implement the distribution of Key. Computer Engineering and Applications, 21(2006)3, 141–143 (in Chinese). 米波, 廖晓峰, 陈勇. 基于椭圆曲线进行密钥分配的混 沌加密系统. 计算机工程与应用, 21(2006)3, 141–143.
C. Bonanno and G. Menconi. Computational information for the logistic map at the chaos threshold. Discrete and Continuous Dynamical Systems Series B, 2(2002)3, 415–431.
R. M. Avanzi. Aspects of hyper-elliptic curves over large prime fields in software implementations. Proceedings of International Association for Cryptology Research. New York, Spring-Verlag, 2004, 148–162.
M. Abe, M. Ohkubo, and K. Suzuki. 1 out of n signature from a variety of keys. Proceedings of Advances in Cryptology-ASIACRYPT’02. New York, Spring-Verlag, 2002, 415–423.
W. Lee and J. Lee. Design and implementation of secure e-mail system using elliptic curve cryptosystem. Future Generation Computer Systems, 20(2004)2, 315–326.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communication author: Gao Chao, born in 1958, male, Ph.D., Professor.
About this article
Cite this article
Gao, C., Liang, D. & Zhou, S. A novel research of confidential communication based on the elliptic curve and the combined chaotic mapping. J. Electron.(China) 26, 706–710 (2009). https://doi.org/10.1007/s11767-009-0069-4
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11767-009-0069-4