Abstract
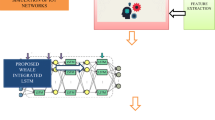
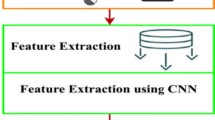
Internet of things (IoT) provides a new application, which helps the existing networks communicate with smart technologies. Things are now becoming increasingly connected to the Internet, and lots of new gadgets are being created at a faster rate. Since these interconnected smart objects are capable of interacting with one another in undefended surroundings, the entire communication ecology needs solutions related to security at various levels. Unlike the existing networks, IoT technology has its own set of features, including various network protocol requirements and a variety of resource constraints. To launch different attacks, the attacker takes many security vulnerabilities in the IoT system. The growth in cyber-attacks has rendered it important to address the consequences implied in the IoT. This paper intends to introduce a novel attack detection model. Originally, the input data are preprocessed, from which the most relevant features are extracted that include raw features, statistical features, and higher-order statistical features. The extracted features are subjected to the classification process. More importantly, the extracted raw features are directly given to the long short-term memory (LSTM), and the extracted statistical and higher-order statistical features are subjected to the deep reinforcement learning (DRL) for the classification process. Then, the average of both LSTM and DRL provides the detected output in an effective manner. To improve the performance of detection results, the weight of LSTM is optimized by the self-improved battle royale optimization (SIBRO) algorithm. At the end, the performance of the presented scheme is compared to the existing approaches in terms of different metrics like “F-measure, specificity, NPV, accuracy, FNR, sensitivity, precision, FPR, and MCC,” respectively.








Similar content being viewed by others
Abbreviations
- AI:
-
Artificial intelligence
- AEs:
-
Autoencoders
- ANN:
-
Artificial neural network
- A1DE and A2DE:
-
Averaged one-dependence and two-dependence
- BI-LSTM:
-
Bidirectional long short-term memory
- BRO:
-
Battle royale optimization
- C-DAD:
-
Counter-based DDos attack detection
- CNN:
-
Convolutional neural network
- DCONST:
-
Distributed consensus-based trust model
- DL:
-
Deep learning
- DoS:
-
Denial of service
- DR:
-
Detection rate
- DRL:
-
Deep reinforcement learning
- DQN:
-
Deep Q-network
- DT:
-
Decision tree
- DTL:
-
Deep transfer learning
- FNR:
-
False negative rate
- FPR:
-
False positive rate
- GOA:
-
Grasshopper optimization algorithm
- HD:
-
Hard detection
- HIDS:
-
Host-based IDS
- IDS:
-
Intrusion detection system
- IoT:
-
Internet of things
- LEDEM:
-
Learning-driven detection and mitigation
- LR:
-
Logistic regression
- LSTM:
-
Long short-term memory
- MCC:
-
Matthews correlation coefficient
- MFO:
-
Moth flame optimization
- ML:
-
Machine learning
- ML-F:
-
Metaheuristic lion optimization algorithm and firefly optimization algorithm
- MOPSO:
-
Multi-objective particle swarm optimization
- NIDS:
-
Network-based IDS
- NPV:
-
Net predictive value
- PDE:
-
Perceptron detection with enhancement
- PDF:
-
Probability density function
- RF:
-
Random forest
- SDN:
-
Software-defined network
- SLnO:
-
Sea lion optimization
- SVM:
-
Support vector machine
References
Kaliyar P, Jaballah WB, Lal C (2020) LiDL: localization with early detection of sybil and wormhole attacks in IoT networks. Comput Secur 94:101849
Liu L, Ma Z, Meng W (2019) Detection of multiple-mix-attack malicious nodes using perceptron-based trust in IoT networks. Future Gener Comput Syst 101:865–879
Rathore S, Park JH (2018) Semi-supervised learning based distributed attack detection framework for IoT. Appl Soft Comput 72:79–89
Rahman MA, Asyhari AT, Zolkipli MF (2020) Scalable machine learning-based intrusion detection system for IoT-enabled smart cities. Sustain Cities Soc 61:102324. https://doi.org/10.1016/j.scs.2020.102324
Kore A, Patil S (2020) IC-MADS: IoT enabled cross layer man-in-middle attack detection system for smart healthcare application. Wireless Pers Commun 113:727–746. https://doi.org/10.1007/s11277-020-07250-0
Nweke HF, Teh YW, Mujtaba G et al (2019) Multi-sensor fusion based on multiple classifier systems for human activity identification. Hum Cent Comput Inf Sci 9:34. https://doi.org/10.1186/s13673-019-0194-5
Wang N, Li W, Alipour-Fanid A, Dabaghchian M, Zeng K (2020) Compressed-sensing-based pilot contamination attack detection for NOMA-IoT communications. IEEE Internet Things J 7(8):7764–7772. https://doi.org/10.1109/JIOT.2020.2991956
Al-Hamadi H, Chen I-R, Wang D-C, Almashan M (2020) Attack and defense strategies for intrusion detection in autonomous distributed IoT systems. IEEE Access 8:168994–169009. https://doi.org/10.1109/ACCESS.2020.3023616
Roy RG, Ghoshal D (2020) Search and rescue optimization algorithm - second order sliding mode control: AUV error tracking. J Comput Mech Power Syst Control 3:10–20
Anand S (2020) Intrusion detection system for wireless mesh networks via improved whale optimization. J Netw Commun Syst 3:9–16
Rajeyyagari S (2020) Automatic speaker diarization using deep LSTM in audio lecturing of e-Khool platform. J Netw Commun Syst 3:17–25
Chakkaravarthy SS, Sangeetha D, Cruz MV, Vaidehi V, Raman B (2020) Design of intrusion detection honeypot using social leopard algorithm to detect IoT ransomware attacks. IEEE Access 8:169944–169956. https://doi.org/10.1109/ACCESS.2020.3023764
Kponyo JJ, Agyemang JO, Boateng JO (2020) Lightweight and host-based denial of service (DoS) detection and defense mechanism for resource-constrained IoT devices. Internet Things 12:100319
Mirsky Y, Golomb T, Elovici Y (2020) Lightweight collaborative anomaly detection for the IoT using blockchain. J Parallel Distrib Comput 145:75–97
Roldán J, Boubeta-Puig J, Ortiz G (2020) Integrating complex event processing and machine learning: an intelligent architecture for detecting IoT security attacks. Expert Syst Appl 149:113251
Almiani M, AbuGhazleh A, Razaque A (2020) Deep recurrent neural network for IoT intrusion detection system. Simul Model Pract Theory 101:102031
Zhou M, Han L, Lu H et al (2020) Intrusion detection system for IoT heterogeneous perceptual network. Mobile Netw Appl. https://doi.org/10.1007/s11036-019-01483-5
Kumar P, Gupta GP, Tripathi R (2020) A distributed ensemble design based intrusion detection system using fog computing to protect the internet of things networks. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-020-02696-3
Shirsat P (2020) Developing deep neural network for learner performance prediction in EKhool online learning platform. Multimedia Res 3:24–31
Cristin R, Raj VC, Marimuthu R (2019) Face image forgery detection by weight optimized neural network model. Multimedia Res 2:19–27
Shaik JB, Ganesh V (2020) Deep neural network and social ski-driver optimization algorithm for power system restoration with VSC - HVDC technology. J Comput Mech Power Syst Control 3:1–9
Babu MJ, Reddy AR (2020) SH-IDS: specification heuristics based intrusion detection system for IoT networks. Wireless Pers Commun 112:2023–2045. https://doi.org/10.1007/s11277-020-07137-0
Elrawy M, Awad A, Hamed H (2018) Intrusion detection systems for IoT-based smart environments: a survey. J Cloud Comp. https://doi.org/10.1186/s13677-018-0123-6
Samy A, Yu H, Zhang H (2020) Fog-based attack detection framework for internet of things using deep learning. IEEE Access 8:74571–74585. https://doi.org/10.1109/ACCESS.2020.2988854
Hasan M, Islam MM, Hashem MM (2019) Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Int Things 7:100059
Ravi N, Shalinie SM (2020) Learning-driven detection and mitigation of ddos attack in iot via sdn-cloud architecture. IEEE Int Things J 7(4):3559–3570. https://doi.org/10.1109/JIOT.2020.2973176
Bhayo J, Hameed S, Shah SA (2020) An efficient counter-based DDoS attack detection framework leveraging software defined ioT (SD-IoT). IEEE Access 8:221612–221631. https://doi.org/10.1109/ACCESS.2020.3043082
Khan AY, Latif R, Latif S, Tahir S, Batool G, Saba T (2020) Malicious insider attack detection in IoTs using data analytics. IEEE Access 8:11743–11753. https://doi.org/10.1109/ACCESS.2019.2959047
Vu L, Nguyen QU, Nguyen DN, Hoang DT, Dutkiewicz E (2020) Deep transfer learning for IoT attack detection. IEEE Access 8:107335–107344. https://doi.org/10.1109/ACCESS.2020.3000476
Ma Z, Liu L, Meng W (2020) Towards multiple-mix-attack detection via consensus-based trust management in IoT networks. Comput Secur 96:101898
Baig ZA, Sanguanpong S, So-In C (2020) Averaged dependence estimators for DoS attack detection in IoT networks. Future Gener Comput Sys 102:198–209
Zarpelão BB, Miani RS, Kawakani CT, de Alvarenga SC (2017) A survey of intrusion detection in Internet of Things. J Netw Comput Appl 84:25–37
Kasongo SM (2021) An advanced intrusion detection system for IIoT based on GA and tree based algorithms. IEEE Access 9:113199–113212
Liu Z (2011) A method of SVM with normalization in intrusion detection. Procedia Environ Sci 11:256–262
Moustafa N, Slay J (2016) The evaluation of network anomaly detection systems: statistical analysis of the UNSW-NB15 data set and the comparison with the KDD99 data set. Inform Secur J A Global Perspect 25(1–3):18–31. https://doi.org/10.1080/19393555.2015.1125974
Martinez C, Perrin G, Ramasso E, Rombaut M (2018) A deep reinforcement learning approach for early classification of time series. 2018 26th Eur Signal Process Conf (EUSIPCO), pp 2030–2034. https://doi.org/10.23919/eusipco.2018.8553544
Zhou X, Lin J, Zhang Z, Shao Z, Liu H (2019) Improved itracker combined with bidirectional long short-term memory for 3D gaze estimation using appearance cues. Neuro Comput 390:217–225
Rahkar Farshi T (2021) Battle royale optimization algorithm. Neural Comput Appl 33(4):1139–1157. https://doi.org/10.1007/s00521-020-05004-4
Rajakumar BR (2013) Impact of static and adaptive mutation techniques on genetic algorithm. Int J Hybrid Intelligent Sys 10(1):11–22. https://doi.org/10.3233/HIS-120161
Rajakumar BR (2013) Static and adaptive mutation techniques for genetic algorithm: a systematic comparative analysis. Int J Comput Sci Eng 8(2):180–193. https://doi.org/10.1504/IJCSE.2013.053087
Swamy SM, Rajakumar BR, Valarmathi IR (2013) Design of hybrid wind and photovoltaic power system using opposition-based genetic algorithm with cauchy mutation. IET Chennai fourth international conference on sustainable energy and intelligent systems (Seiscon 2013), chennai, India, Dec 2013, Doi: https://doi.org/10.1049/ic.2013.0361
George A, Rajakumar BR (2013) APOGA: an adaptive population pool size based genetic algorithm. AASRI Procedia - 2013 AASRI conference on intelligent systems and control (ISC 2013). Am Appl Sci Res Inst 4:288–296. https://doi.org/10.1016/j.aasri.2013.10.043
Rajakumar BR, George A (2012) A new adaptive mutation technique for genetic algorithm. In: proceedings of IEEE international conference on computational intelligence and computing research (ICCIC), pp. 1–7, Dec 18–20, Coimbatore, India, Doi: https://doi.org/10.1109/ICCIC.2012.6510293
LeCun Y, Kavukvuoglu K, Farabet C (2010) Convolutional networks and applications in vision. In Circuits and Systems, International Symposium on, 253–256
Avci E (2009) A new intelligent diagnosis system for the heart valve diseases by using genetic-SVM classifier. Expert Syst Appl 36:10618–10626
Mirjalili S (2015) Moth-flame optimization algorithm: a Novel nature-inspired heuristic paradigm. Knowledge Based Syst 89:228–249
Saremi S, Mirjalili S, Lewis A (2017) Grasshopper optimisation algorithm: theory and application. Adv Eng Softw 105:30–47
Masadeh R, Mahafzah B, Sharieh A (2019) Sea Lion Optimization Algorithm. Int J Adv Comput Sci Appl 10:388–395
Krishna ES, Thangavelu A (2021) Attack detection in IoT devices using hybrid metaheuristic lion optimization algorithm and firefly optimization algorithm. Int J Syst Assurance Eng Manag 1-14. https://doi.org/10.1007/s13198-021-01150-7
The UNSW-NB15 Dataset. https://research.unsw.edu.au/projects/unsw-nb15-dataset
Habib M, Aljarah I, Faris H, Mirjalili S (2020) Multi-objective particle swarm optimization for botnet detection in internet of things, In: Evolutionary machine learning techniques, Springer publisher, Singapore, pp. 203–229
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Rekha, H., Siddappa, M. Hybrid deep learning model for attack detection in internet of things. SOCA 16, 293–312 (2022). https://doi.org/10.1007/s11761-022-00342-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11761-022-00342-8