Abstract
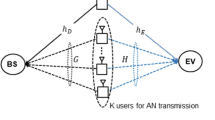
The security issue is critically important for wireless communications, especially for multi-hop communications. In this paper, we propose a cooperative secrecy beamforming scheme for a multi-hop MIMO communication network, in which there is a single-antenna source, multiple multi-antenna relays and a singleantenna destination. Moreover, two types of eavesdroppers exist in the network, one of which has known channel state information (CSI), while the other not. To achieve security communications, in our work null-space beamforming and artificial noise beamforming are jointly optimized to improve the secrecy rate of the multi-hop network. In nature, the joint optimization is nonconvex and challenging. Exploiting its structure, the considered optimization problem is decoupled into a series of subproblems that can be efficiently solved based on convex optimization theory. Finally, some numerical experiment results are provided to assess the performance of the proposed secrecy beamforming design.
创新点
物理层安全在无线网络通信中占据重要地位,尤其是针对窃听可能性较大的多跳网络。基于此我们提议了一个协作的多跳MIMO通信网络下的安全波束赋性方案。假定网络中存在一个单天线的发射端,多个多天线的中继以及一个单天线的接收端, 同时还有两个不同类型的窃听者, 其中一类窃听者的信道信息已知, 而另一类窃听者信道信息未知。为了实现多跳 MIMO 网络的安全通信,我们采用迫零波束赋性算法和人工噪声发送方案来分别尽可能的降低被这两类窃听者窃听的信息量,从而达到提升多跳网络的安全容量的目标。通常来说,对多个基站进行联合波束赋形设计有一定的困难和挑战,因为优化问题常常是非凸的NP-hard 问题。 因此, 我们提议了一个基于凸优化理论的迭代波束赋形优化算法,通过将原始的非凸优化问题分解为一系列具有凸性质的子问题来迭代的设计每个基站的最优波束矩阵。仿真结果表明我们所提议的算法可以有效的提升系统的安全容量。
Similar content being viewed by others
References
Xing C W, Ma S D, Wu Y C. Robust joint design of linear relay precoder and destination equalizer for dual-hop amplify-and-forward MIMO relay systems. IEEE Trans Signal Process, 2010, 58: 2273–2283
Rong Y, Hua Y. Optimality of diagonalization of multi-hop MIMO relays. IEEE Trans Wirel Commun, 2009, 8: 6068–6077
Xing C W, Xia M, Gao F, et al. Robust transceiver with Tomlinson-Harashima precoding for amplify-and-forward MIMO relaying systems. IEEE J Sele Area Commun, 2012, 30: 1370–1382
Telatar I E. Capacity of multi-antenna gaussian channels. Eur Trans Telecommun, 1999, 10: 585–595
Zhu F, Gao F, Yao M, et al. Joint information and jamming beamforming for physical layer security with full duplex base station. IEEE Trans Signal Process, 2014, 62: 6391–6401
Li Z, Trappe W, Yates R. Secret communication via multi-antenna transmission. In: Proceedings of 41st Conf Inf Sci Syst, Baltimore, 2007. 905–910
Ni J Q, Fei Z S, Xing C W, et al. Secrecy balancing over two-user MISO interference channels with rician fading. Int J Antenn Propag, 2013, 2013: 546260
Lindblom J, Karipidis E. Closed-form parameterization of the pareto boundary for the two-user MISO interference channel. In: Proceedings of IEEE Int Conf Acoustics, Speech, and Signal Processing, Prague, 2011. 3372–3375
Chen L, Wong K K, Chen H. Optimizing transmitter-receiver collaborative-relay beamforming with perfect CSI. IEEE Commun Lett, 2011, 15: 314–316
Wang C, Liu J, Dong Z. Multi-hop collaborative relay beamforming. In: Proceedings of IEEE Vehicular Technology Conference, Las Vegas, 2013. 1–5
Shannon C E. Communication theory of secrecy systems. Bell Syst Tech J, 1949, 28: 656–715
Wyner A D. The wire-tap channel. Bell Sys Tech J, 1975, 54: 1355–1387
Dai B, Ma Z. Achievable rate-equivocation regions for relay broadcast channels with confidential messages. In: Proceedings of ISITA, Melbourne, 2014. 393–397
Leung-Yan-Cheong S, Hellman M E. The Gaussian wire-tap channel. IEEE Trans Inf Theory, 1978, 24: 451–456
Jorswieck A E, Mochaourab R. Secrecy rate region of MISO interference channel: pareto boundary and non-cooperative games. In: Proceedings of international ITG workshop on smart Antennas, Berlin, 2009. 1–8
Fei Z S, Ni J Q, Zhao D, et al. Ergodic secrecy rate of two-user MISO interference channels with statistical CSI. Sci China Inf Sci, 2014, 57: 102302
Mu P C, Wang H M, Yin Q Y. Improving the secrecy rate of wireless SIMO systems via two-step transmission. In: Proceedings of Globecom Workshops, Atlanta, 2013. 1280–1285
Wang Y W, Yu F R, Tang H, et al. A mean field game theoretic approach for security enhancements in mobile ad hoc networks. IEEE Trans Wirel Commun, 2014, 13: 1616–1627
Luan T, Gao F, Zhang X. Joint resource scheduling for relay-assisted broadband cognitive radio networks. IEEE Trans Wirel Commun, 2012, 11: 3090–3100
Wang H M, Yin Q Y. Improving the physical-layer security of wireless two-way relaying via analog network coding. In: Proceedings of Global Telecommunications Conference, Houston, 2011. 5–9
Wang H M, Luo M, Yin Q Y. Hybrid cooperative beamforming and jamming for physical-layer security of two-way relay networks. IEEE Trans Inf Foren Secur, 2013, 8: 2007–2020
Khisti A, Wornell G. Secure transmission with multiple antennas II: the MIMOME wiretap channel. IEEE Trans Inf Theory, 2010, 56: 5515–5532
Tekin E, Yener A. The general gaussian multiple access and two-way wire-tap channels: achievable rates and cooperative jamming. IEEE Trans Inf Theory, 2008, 54: 2735–2751
Zhang Z, Long K, Wang J, et al. On swarm intelligence inspired self-organized networking: its bionic mechanisms, designing principles and optimization approaches. IEEE Commun Surv Tut, 2014, 16: 513–537
Zhang Z, Long K, Wang J. Self-organization paradigms and optimization approaches for cognitive radio technologies: a survey. IEEE Wirel Commun, 2013, 20: 36–42
Vaikundam G, Sudha G F. Distributed beamforming for randomly distributed sensors using bisection method and dynamic programming technique. In: Proceedings of IEEE Int Conf CONECCT, Bangalore, 2013. 1–6
Michael G, Stephen B. CVX Users’ Guide for CVX version 1.21, 1996
Ekrem E, Ulukus S. Secure broadcasting using multiple antennas. J Commun Netw, 2010, 12: 411–432
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Gong, S., Xing, C., Fei, Z. et al. Cooperative beamforming design for physical-layer security of multi-hop MIMO communications. Sci. China Inf. Sci. 59, 062304 (2016). https://doi.org/10.1007/s11432-015-5401-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11432-015-5401-z