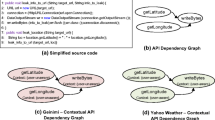
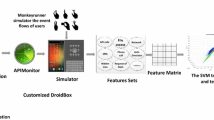
Abstract
Malware remains a threat to our cyberspace and increasingly digitalized society. Current malware hunting techniques employ a variety of features, such as OpCodes, ByteCodes, and API calls, to distinguish malware from goodware. However, existing malware hunting approaches generally focus on a single particular view, such as using dynamic information or opcodes only. While single-view malware hunting systems may provide lean and optimized basis for detecting a specific type of malware, their performance can be significantly limited when dealing with other types of malware; thus, making it trivial for an advanced attacker to develop malware that simply obfuscates features monitored by a single-view malware detection system. To address these limitations, we propose a multi-view learning method that uses multiple views including OpCodes, ByteCodes, header information, permission, attacker’s intent and API call to hunt malicious programs. Our system automatically assigns weights to different views to optimize detection in different environment. Using experiments conducted on various Windows, Android and Internet of Things (IoT) platforms, we demonstrate that our method offers high accuracy with a low false positive rate on these case study platforms. Moreover, we also investigate the robustness of detection against weak views (features with low power of discrimination). The proposed method is the first malware threat hunting method that can be applied to different platforms, at the time of this research, and it is considerably difficult for attackers to evade detection (since it requires attackers to obfuscate multiple different views).
















Similar content being viewed by others
Notes
References
Arp, D., Spreitzenbarth, M., Hubner, M., Gascon, H., Rieck, K., Siemens, C.: Drebin: effective and explainable detection of android malware in your pocket. In: Ndss, vol. 14, pp 23–26 (2014)
Azmoodeh, A., Dehghantanha, A., Choo, K.K.R.: Robust malware detection for internet of (battlefield) things devices using deep eigenspace learning. IEEE Trans. Sustain. Comput. (2018)
Azmoodeh, A., Dehghantanha, A., Conti, M., Choo, K.K.R.: Detecting crypto-ransomware in iot networks based on energy consumption footprint. J. Ambient. Intell. Humaniz. Comput., 1–12 (2017)
Bai, J., Wang, J.: Improving malware detection using multi-view ensemble learning. Secur. Commun. Netw. 9(17), 4227–4241 (2016)
Beel, J., Gipp, B., Langer, S., Breitinger, C.: Research-paper recommender systems: a literature survey. Int. J. Digital Libraries 17(4), 305–338 (2015). https://doi.org/10.1007/s00799-015-0156-0
Bishop, C.M., et al.: Neural Networks for Pattern Recognition. Oxford University Press, London (1995)
Chakraborty, T., Pierazzi, F., Subrahmanian, V.: Ec2: ensemble clustering and classification for predicting android malware families. IEEE Trans. Dependable Secure Comput. (1), 1–1 (2017)
Cui, H., Zhou, Y., Wang, C., Li, Q., Ren, K.: Towards privacy-preserving malware detection systems for android. In: 2018 IEEE 24th International Conference on Parallel and Distributed Systems (ICPADS), pp 545–552 (2018)
Darabian, H., Dehghantanha, A., Hashemi, S., Homayoun, S., Choo, K.K.R.: An opcode-based technique for polymorphic internet of things malware detection. Concurrency and Computation: Practice and Experience, e5173 (2019)
Farrokhmanesh, M., Hamzeh, A.: Music classification as a new approach for malware detection. Journal of Computer Virology and Hacking Techniques, 1–20 (2018)
Garcia, J., Hammad, M., Pedrood, B., Bagheri-Khaligh, A., Malek, S.: Obfuscation-Resilient, Efficient, and Accurate Detection and Family Identification of Android Malware. Department of Computer Science, George Mason University, Tech. Rep (2015)
Guo, J., Zhu, W.: Partial multi-view outlier detection based on collective learning. In: Thirty-Second AAAI Conference on Artificial Intelligence (2018)
Guo, S., Yuan, Q., Lin, F., Wang, F., Ban, T.: A malware detection algorithm based on multi-view fusion. In: International Conference on Neural Information Processing, pp 259–266. Springer (2010)
HaddadPajouh, H., Dehghantanha, A., Khayami, R., Choo, K.K.R.: A deep recurrent neural network based approach for internet of things malware threat hunting. Futur. Gener. Comput. Syst. 85, 88–96 (2018)
Hearst, M.A., Dumais, S.T., Osuna, E., Platt, J., Scholkopf, B.: Support vector machines. IEEE Int. Sys. Appl. 13(4), 18–28 (1998)
Hopkins, M., Dehghantanha, A.: Exploit kits: the production line of the cybercrime economy?. In: 2015 Second International Conference on Information Security and Cyber Forensics (Infosec), pp 23–27. IEEE (2015)
Hu, Q., Zhu, P., Yang, Y., Yu, D.: Large-margin nearest neighbor classifiers via sample weight learning. Neurocomputing 74(4), 656–660 (2011)
Idrees, F., Rajarajan, M., Conti, M., Chen, T.M., Rahulamathavan, Y.: Pindroid: a novel android malware detection system using ensemble learning methods. Comput. Secur. 68, 36–46 (2017)
Kohavi, R., et al.: A study of cross-validation and bootstrap for accuracy estimation and model selection. In: Ijcai, vol. 14, pp 1137–1145. Montreal, Canada (1995)
Maiorca, D., Biggio, B., Giacinto, G.: Towards adversarial malware detection: lessons learned from pdf-based attacks. ACM Computing Surveys (CSUR) 52(4), 78 (2019)
Narayanan, A., Chandramohan, M., Chen, L., Liu, Y.: A multi-view context-aware approach to android malware detection and malicious code localization. Empir. Softw. Eng. 23(3), 1222–1274 (2018)
Narayanan, A., Soh, C., Chen, L., Liu, Y., Wang, L.: Apk2vec: semi-supervised multi-view representation learning for profiling android applications. In: 2018 IEEE International Conference on Data Mining (ICDM), pp 357–366 (2018)
Nari, S., Ghorbani, A.A.: Automated malware classification based on network behavior. In: 2013 International Conference on Computing, Networking and Communications (ICNC), pp 642–647. IEEE (2013)
Nguyen-Vu, L., Ahn, J., Jung, S.: Android fragmentation in malware detection. Comput. Secur. 87, 101573 (2019)
O’Kane, P., Sezer, S., Carlin, D.: Evolution of ransomware. IET Netw. 7 (5), 321–327 (2018)
Prayudi, Y., Riadi, I., et al.: Implementation of malware analysis using static and dynamic analysis method. Int. J. Comput. Appl. 117(6) (2015)
Raff, E., Sylvester, J., Nicholas, C.: Learning the pe header, malware detection with minimal domain knowledge. In: Proceedings of the 10th ACM Workshop on Artificial Intelligence and Security, pp 121–132. ACM (2017)
Rokach, L.: Ensemble-based classifiers. Artif. Intell. Rev. 33(1-2), 1–39 (2010)
Ronen, R., Radu, M., Feuerstein, C., Yom-Tov, E., Ahmadi, M.: Microsoft malware classification challenge. arXiv:1802.10135 (2018)
Sahs, J., Khan, L.: A machine learning approach to android malware detection. In: 2012 European Intelligence and Security Informatics Conference, pp 141–147. IEEE (2012)
Salehi, Z., Sami, A., Ghiasi, M.: Maar: robust features to detect malicious activity based on api calls, their arguments and return values. Eng. Appl. Artif. Intel. 59, 93–102 (2017)
Sami, A., Yadegari, B., Rahimi, H., Peiravian, N., Hashemi, S., Hamze, A.: Malware detection based on mining api calls. In: Proceedings of the 2010 ACM Symposium on Applied Computing, pp 1020–1025. ACM (2010)
Sarma, BP, Li, N, Gates, C, Potharaju, R, Nita-Rotaru, C, Molloy, I: Android permissions: a perspective combining risks and benefits Proceedings of the 17th ACM symposium on Access Control Models and Technologies, pp 13–22, ACM (2012)
Santos, I., Devesa, J., Brezo, F., Nieves, J., Bringas, P.G.: Opem: a static-dynamic approach for machine-learning-based malware detection. In: International Joint Conference CISIS’12-ICEUTE 12-SOCO 12 Special Sessions, pp 271–280. Springer (2013)
Shalaginov, A., Banin, S., Dehghantanha, A., Franke, K.: Machine learning aided static malware analysis: a survey and tutorial. Cyber Threat Intelligence, 7–45 (2018)
Sheen, S., Anitha, R., Sirisha, P.: Malware detection by pruning of parallel ensembles using harmony search. Pattern Recogn. Lett. 34(14), 1679–1686 (2013)
Shijo, P., Salim, A.: Integrated static and dynamic analysis for malware detection. Procedia Comput. Sci. 46, 804–811 (2015)
Sikorski, M., Honig, A.: Pratical Malware Analysis O’Reilly (2012)
Singh, A., Dutta, D., Saha, A.: Migan: malware image synthesis using gans. In: Proceedings of the AAAI Conference on Artificial Intelligence, vol. 33, pp 10033–10034 (2019)
Skolka, P., Staicu, C.A., Pradel, M.: Anything to hide? Studying minified and obfuscated code in the web. In: The World Wide Web Conference, pp 1735–1746. ACM (2019)
Steinwart, I., Christmann, A.: Support Vector Machines. Springer, Berlin (2008)
Sun, S.: A survey of multi-view machine learning. Neural Comput. Applic. 23 (7-8), 2031–2038 (2013)
Taheri, M., Azad, H., Ziarati, K., Sanaye, R.: A quadratic margin-based model for weighting fuzzy classification rules inspired by support vector machines. Iranian J. Fuzzy Sys. 10(4), 41–55 (2013)
Wang, Q., Guo, W., Zhang, K., Ororbia, II, Xing, A.G., Liu, X., Giles, C.L.: Adversary resistant deep neural networks with an application to malware detection. In: Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp 1145–1153. ACM (2017)
Xu, C., Tao, D., Xu, C.: A survey on multi-view learning. arXiv:1304.5634 (2013)
Xu, Z., Sun, S.: An algorithm on multi-view adaboost. In: International Conference on Neural Information Processing, pp 355–362. Springer (2010)
Yakura, H., Shinozaki, S., Nishimura, R., Oyama, Y., Sakuma, J.: Neural malware analysis with attention mechanism. Comput. Secur. 87, 101592 (2019)
Ye, Y., Hou, S., Chen, L., Lei, J., Wan, W., Wang, J., Xiong, Q., Shao, F.: Out-of-sample node representation learning for heterogeneous graph in real-time android malware detection. In: 28th International Joint Conference on Artificial Intelligence (IJCAI), 2019 (2019)
Ye, Y., Li, T., Adjeroh, D., Iyengar, S.S.: A survey on malware detection using data mining techniques. ACM Computing Surveys (CSUR) 50(3), 41 (2017)
You, I., Yim, K.: Malware obfuscation techniques: a brief survey. In: 2010 International Conference on Broadband, Wireless Computing, Communication and Applications (BWCCA), pp 297–300. IEEE (2010)
Zhao, J., Xie, X., Xu, X., Sun, S.: Multi-view learning overview: recent progress and new challenges. Information Fusion 38, 43–54 (2017)
Zhou, D., He, J., Candan, K.S., Davulcu, H.: Muvir: multi-view rare category detection. In: Twenty-Fourth International Joint Conference on Artificial Intelligence (2015)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article belongs to the Topical Collection: Special Issue on Smart Computing and Cyber Technology for Cyberization
Guest Editors: Xiaokang Zhou, Flavia C. Delicato, Kevin Wang, and Runhe Huang
Rights and permissions
About this article
Cite this article
Darabian, H., Dehghantanha, A., Hashemi, S. et al. A multiview learning method for malware threat hunting: windows, IoT and android as case studies. World Wide Web 23, 1241–1260 (2020). https://doi.org/10.1007/s11280-019-00755-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11280-019-00755-0