Abstract
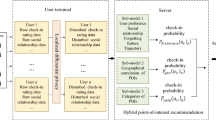
Point-of-interest (POI) recommendation has attracted much interest recently because of its significant business potential. Data used in POI recommendation (e.g., user-location check-in matrix) are much more sparse than that used in traditional item (e.g., book and movie) recommendation, which leads to more serious cold start problem. Social POI recommendation has proved to be an effective solution, but most existing works assume that recommenders have access to all required data. This is very rare in practice because these data are generally owned by different entities who are not willing to share their data with others due to privacy and legal concerns. In this paper, we first propose PLAS, a protocol which enables effective POI recommendation without disclosing the sensitive data of every party getting involved in the recommendation. We formally show PLAS is secure in the semi-honest adversary model. To improve its performance. We then adopt the technique of cloaking area by which expensive distance computation over encrypted data is replaced by cheap operation over plaintext. In addition, we utilize the sparsity of check-ins to selectively publish data, thus reducing encryption cost and avoiding unnecessary computation over ciphertext. Experiments on two real datasets show that our protocol is feasible and can scale to large POI recommendation problems in practice.










Similar content being viewed by others
References
Bagci, H., Karagoz, P.: Context-aware friend recommendation for location based social networks using random walk: In: Proceedings of the 25th International Conference Companion on World Wide Web, pp. 531–536. ACM (2016)
Bamba, B., Liu, L., Pesti, P., Wang, T.: Supporting anonymous location queries in mobile environments with privacygrid. In: Proceedings of the 17th International Conference on World Wide Web, pp. 237–246. ACM (2008)
Bettini, C., Wang, X., Jajodia, S.: Protecting privacy against location-based personal identification. In: Proceedings of the 31st Workshop on Secure Data Management, pp. 185–199. Springer (2005)
Chen, L., Gao, Y., Xing, Z., Jensen, C.S., Chen, G.: I2RS: A distributed geo-textual image retrieval and recommendation system. Proc. VLDB Endow. 8(12), 1884–1887 (2015)
Chen, L., Gao, Y., Chen, G., Zhang, H.: Metric all-k-nearest-neighbor search. IEEE Trans. Knowl. Data Eng. 28(1), 98–112 (2016)
Cormode, G., Procopiuc, C., Srivastava, D., Shen, E., Yu, T.: Differentially private spatial decompositions. In: Proceedings of the 28th international conference on data engineering, pp. 20–31. IEEE (2012)
Erkin, Z., Veugen, T., Toft, T., Lagendijk, R.L.: Generating private recommendations efficiently using homomorphic encryption and data packing. IEEE Trans. Inf. Forens. Secur. 7(3), 1053–1066 (2012)
Gao, H., Tang, J., Liu, H.: Addressing the cold-start problem in location recommendation using geo-social correlations. Data Min. Knowl. Disc. 29(2), 299–323 (2015)
Gao, L., Guo, Z., Zhang, H., Xing, X., Shen, H.T.: Video captioning with attention-based lstm and semantic consistency. IEEE Trans. Multimed. 19(9), 2045–2055 (2017)
Gao, Y., Zheng, B., Chen, G., Lee, W.-C., Lee, K.C.K., Li, Q.: Visible reverse k-nearest neighbor query processing in spatial databases. IEEE Trans. Knowl. Data Eng. 21(9), 1314–1327 (2009)
Gedik, B, Liu, L: Location privacy in mobile systems A personalized anonymization model. In: Proceedings of 25th IEEE International conference on distributed computing systems, pp. 620–629 IEEE (2005)
Ghinita, G., Kalnis, P., Khoshgozaran, A., Shahabi, C., Tan, K.-L.: Private queries in location based services: anonymizers are not necessary. In: Proceedings of the 2008 ACM SIGMOD International Conference on Management of Data, pp. 121–132. ACM (2008)
Goldreich, O., Ron, D.: On proximity oblivious testing. In: Proceedings of the 41st Annual ACM, Symposium on Theory of Computing, pp. 141–150 (2009)
Hosseini, S., Li, L.T.: Point-of-interest recommendation using temporal orientations of users and locations. In: Proceedings of the 21nd international conference on database systems for advanced applications, pp. 330–347. Springer (2016)
Huang, J., Qi, J., Yabo, X., Chen, J.: A privacy-enhancing model for location-based personalized recommendations. Distrib. Parallel Datab. 33(2), 253–276 (2015)
Jorgensen, Z., Ting, Y.: A privacy-preserving framework for personalized, social recommendations. In: Proceedings of the 17th International Conference on Extending Database Technology, pp. 571–582 (2014)
Li, H., Ge, Y., Hong, R., Zhu, H.: Point-of-interest recommendations Learning potential check-ins from friends. In: Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp. 975–984. ACM (2016)
Liu, B., Hengartner, U.: Privacy-preserving social recommendations in geosocial networks. In: Proceedings of the Eleventh Annual International Conference on Privacy, Security and Trust, pp. 69–76. IEEE (2013)
Liu, Y., Wei, W., Sun, A., Miao, C.: Exploiting geographical neighborhood characteristics for location recommendation. In: Proceedings of the 23rd ACM International Conference on Conference on Information and Knowledge Management, pp. 739–748. ACM (2014)
Liu, S., Liu, A., Liu, G., Li, Z., Xu, J., Zhao, P., Zhao, L.: A secure and efficient framework for privacy preserving social recommendation.: In: Proceedings of the 17th Asia-Pacific Web Conference, pp. 781–792. Springer (2015)
Liu, A., Zhengy, K., Liz, L., Liu, G., Zhao, L., Zhou, X.: Efficient secure similarity computation on encrypted trajectory data. In: Proceedings of the 31st IEEE international conference on data engineering, pp. 66–77. IEEE (2015)
Liu, X., Li, Z., Deng, C., Tao, D.: Distributed adaptive binary quantization for fast nearest neighbor search. IEEE Trans. Image Process. 26(11), 5324–5336 (2017)
Liu, A., Li, Z.-X., Liu, G.-F., Zheng, K., Zhang, M., Li, Q., Zhang, X.: Privacy-preserving task assignment in spatial crowdsourcing. J. Comput. Sci. Technol. 32(5), 905–918 (2017)
Liu, A., Wang, W., Shang, S., Li, Q., Zhang, X.: Efficient task assignment in spatial crowdsourcing with worker and task privacy protection. GeoInformatica, 1–28 (2017)
Liu, A., Wang, W., Li., Z, Liu, G., Li, Q., Zhou, X., Zhang, X.: A privacy-preserving framework for trust-oriented point-of-interest recommendation. IEEE Access 6, 393–404 (2018)
McSherry, F., Mironov, I.: Differentially private recommender systems: building privacy into the netflix prize contenders. In: Proceedings of the 15th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp. 627–636. ACM (2009)
Miao, X., Gao, Y., Chen, G., Cui, H., Guo, C., Pan, W.: SI2P: A restaurant recommendation system using preference queries over incomplete information. Proc. VLDB Endow. 9(13), 1509–1512 (2016)
Mokbel, M.F., Chow, C.-Y., Aref, Wa.G.: The new casper: Query processing for location services without compromising privacy. In: Proceedings of the 32nd International Conference on Very Large Data Bases, pp. 763–774. VLDB Endowment (2006)
Paillier, P.: Public-key cryptosystems based on composite degree residuosity classes. In: Proceedings of the 18th International Conference on the Theory and Application of Cryptographic Techniques, pp. 223–238. Springer (1999)
Rao, Y., Xie, H., Li, J., Jin, F., Lee Wang, F., Li, Q.: Social emotion classification of short text via topic-level maximum entropy model. Inf Manag 53(8), 978–986 (2016)
Rao, Y., Li, Q., Qingyuan, W., Xie, H., Lee Wang, F., Wang, T.: A multi-relational term scheme for first story detection. Neurocomputing 254, 42–52 (2017)
Samanthula, B.K., Rao, F.-Y., Bertino, E., Yi, X.: Privacy-preserving protocols for shortest path discovery over outsourced encrypted graph data. In: Proceedings of the 16th International Conference on Information Reuse and Integration, pp. 427–434. IEEE (2015)
Song, J., Shen, H.T., Wang, J., Zi, H., Sebe, N., Wang, J.: A distance-computation-free search scheme for binary code databases. IEEE Trans. Multimed. 18(3), 484–495 (2016)
Song, J., Gao, L., Li, L., Zhu, X., Sebe, N.: Quantization-based hashing: A general framework for scalable image and video retrieval. Pattern Recogn. 75, 175–187 (2018)
Song, J., Zhang, H., Xiangpeng L., Lianli, G., Wang, M., Hong, R.: Self-supervised video hashing with hierarchical binary auto-encoder. IEEE Transactions on Image Processing (2018)
Wang, X., Gao, L., Wang, P., Sun, X., Liu, X.: Two-stream 3-d convnet fusion for action recognition in videos with arbitrary size and length. IEEE Trans. Multimed. 20(3), 634–644 (2018)
Wei, L., Hou, J., Yan, Y., Zhang, M., Du, X., Moscibroda, T.: MSQL: Efficient similarity search in metric spaces using SQL. VLDB J 26(6), 829–854 (2017)
Xie, H, Li, X, Wang, T, Li, Cn, Ke, L, Lee Wang, F, Yi, C, Li, Q, Min, H: Personalized search for social media via dominating verbal context. Neurocomputing 172, 27–37 (2016)
Ye, M., Yin, P., Lee, W.-C., Lee, D.-L.: Exploiting geographical influence for collaborative point-of-interest recommendation. In: Proceedings of the 34th International ACM SIGIR Conference on Research and Development in Information Retrieval, pp. 325–334. ACM (2011)
Ying, H., Chen, L., Xiong, Y., Pgrank, J.W.: Personalized geographical ranking for point-of-interest recommendation. In: Proceedings of the 25th International Conference Companion on World Wide Web, pp. 137–138. ACM (2016)
Yuan, Q, Cong, G, Sun, A: Graph-based point-of-interest recommendation with geographical and temporal influences. In: Proceedings of the 23rd ACM International Conference on Conference on Information and Knowledge Management, pp. 659–668. ACM (2014)
Zhang, J.-D., Chow, C.-Y.: Point-of-interest recommendations in location-based social networks. Sigspatial Special 7(3), 26–33 (2016)
Zhu, X., Li, X., Zhang, S., Chunhua, J., Xindong, W.: Robust joint graph sparse coding for unsupervised spectral feature selection. IEEE Trans. Neural Netw. Learn. Syst. 28(6), 1263–1275 (2017)
Acknowledgements
Research reported in this publication was partially supported Natural Science Foundation of China (Grant Nos. 61572336, 61572335, 61402313)
Author information
Authors and Affiliations
Corresponding author
Additional information
This article belongs to the Topical Collection: Special Issue on Deep vs. Shallow: Learning for Emerging Web-scale Data Computing and Applications
Guest Editors: Jingkuan Song, Shuqiang Jiang, Elisa Ricci, and Zi Huang
Rights and permissions
About this article
Cite this article
Wang, W., Liu, A., Li, Z. et al. Protecting multi-party privacy in location-aware social point-of-interest recommendation. World Wide Web 22, 863–883 (2019). https://doi.org/10.1007/s11280-018-0550-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11280-018-0550-9