Abstract
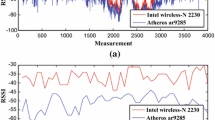
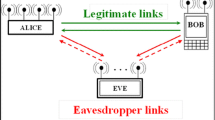
There are some problems that the bit error rate is high but generation rate is low in existing physical layer secret key generation schemes, so we propose a highly consistent and high-speed secret key generation scheme in this paper. This scheme not only can achieve high consistency and high generation rate, but also can ensure randomness of secret key. First, the scheme conducts channel pre-detection to calculate weighted vectors to smooth the noise. Then, a modified level crossing algorithm is proposed to improve key consistency greatly. Furthermore, we put forward cyclic interleaving quantization method that can linearly improve key generation rate and enhance randomness of secret key. Simulation results show that the scheme can achieve zero bit disagreement, and key generation rate can reach at least 495% when SNR is 20 dB.












Similar content being viewed by others
Data Availability
The data that support the findings of this study are available on request from the corresponding author, [J.M.L], upon reasonable request.
References
Shannon, C. E. (1949). Communication theory of secrecy systems. Bell System Technical Journal, 28(4), 656–715.
Hershey, J. E., Hassan, A. A., & Yarlagadda, R. (1995). Unconventional cryptographic keying variable management. IEEE Transactions on Communications, 43(1), 3–6.
Mathur, S., Trappe, W., Mandayam, N., Ye, C., & Reznik, A. (2008). Radio-telepathy: extracting a secret key from an unauthenticated wireless channel. In Proceedings of the 14th ACM international conference on Mobile computing and networking, pp. 128–139. ACM, 2008.
Jana, S., Premnath, SN., Clark, M., Kasera, S.K., Patwari, N., & Krishnamurthy, S.V. (2009). On the effectiveness of secret key extraction from wireless signal strength in real environments. In Proceedings of the 15th annual international conference on Mobile computing and networking, pp. 321–332. ACM, 2009.
Patwari, N., Croft, J., Jana, S., & Kasera, S. K. (2009). High- rate uncorrelated bit extraction for shared secret key generation from channel measurements. IEEE Transactions on Mobile Computing, 9(1), 17–30.
Croft, J., Patwari, N., & Kasera, S.K. (2010). Robust uncorrelated bit extraction methodologies for wireless sensors. In Proceedings of the 9th ACM/IEEE International Conference on Information Processing in Sensor Networks, pp. 70–81. ACM, 2010.
Shen, Z., Liu, J., & Han, Q. (2019). A local pilot auxiliary key generation scheme for secure underwater acoustic communication. Information Sciences, 473, 1–12.
Xiaoyan, Hu., Jin, L., Huang, K., Sun, X., Zhou, Y., & Jinghua, Qu. (2021). Intelligent reflecting surface-assisted secret key generation with discrete phase shifts in static environment. IEEE Wireless Communications Letters, 10(9), 1867–1870.
Liu, J., Shen, Z., Ren, Z., Liu, J., & Gong, F. (2021). A non-time-limited channel sounding protocol for key generation. Wireless Personal Communications, 120, 787–807.
Tang, J., Wen, H., Song, H.-H., Jiao, L., & Zeng, K. (2022). Sharing secrets via wireless broadcasting: A new efficient physical layer group secret key generation for multiple iot devices. IEEE Internet of Things Journal, 9(16), 15228–15239.
Taufiq Sumadi, M., Yuliana, M., & Sudarsono, A. (2020). Performance improvement based on modified lossless quantization (mlq) for secret key generation extracted from received signal strength. In 2020 International Electronics Symposium (IES), pp. 190–194, 2020.
Wirawan, S., & Yuliana, M. (2020). Performance evaluation of secret key generation system for static and dynamic condition. In 2020 IEEE International Conference on Communication, Networks and Satel- lite (Comnetsat), pp. 423–428, 2020.
Han, Q., Liu, J., Shen, Z., Liu, J., & Gong, F. (2020). Vector partitioning quantization utilizing k-means clustering for physical layer secret key generation. Information Sciences, 512, 137–160.
Azimi-Sadjadi, B., Kiayias, A., Mercado, A., & Yener, B. (2007). Robust key generation from signal envelopes in wireless net- works. In Proceedings of the 14th ACM conference on Computer and communications security, pp. 401–410. ACM, 2007.
Liu, H., Yang, J., Wang, Y., & Chen, Y. (2012). Collaborative secret key extraction leveraging received signal strength in mobile wireless networks. In 2012 Proceedings IEEE INFOCOM, pp. 927–935. IEEE, 2012.
Li, X., Liu, J., Yao, Q., & Ma, J. (2017). Efficient and consistent key extraction based on received signal strength for vehicular ad hoc networks. IEEE Access, 5, 5281–5291.
Zhu, X., Fengyuan, X., Novak, E., Tan, C. C., Li, Q., & Chen, G. (2016). Using wireless link dynamics to extract a secret key in vehicular scenarios. IEEE Transactions on Mobile Computing, 16(7), 2065–2078.
Hardoon, D. R., Szedmak, S., & ShaweTaylor, J. (2004). Canonical correlation analysis: An overview with application to learning methods. Neural computation, 16(12), 2639–2664.
Huang, Yi., Zhou, S., Shi, Z., & Lai, L. (2016). Channel frequency response-based secret key generation in underwater acoustic systems. IEEE Transactions on Wireless Communications, 15(9), 5875–5888.
Acknowledgements
Not applicable.
Funding
This work was supported by NaturalScience Basic Research Program of Shaanxi (Program No.2021JM-134).
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Material preparation, data collection and analysis were performed by JZ, JL and RD. The first draft of the manuscript was written by JZ and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Ethical approval and consent to participate
Not applicable.
Consent for publication
Written informed consent for publication was obtained from all participants.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhao, J., Liu, J. & Dai, R. A Highly Consistent and High-speed Physical Layer Key Generation Scheme. Wireless Pers Commun 133, 1105–1122 (2023). https://doi.org/10.1007/s11277-023-10806-5
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10806-5