Abstract
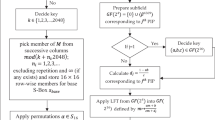
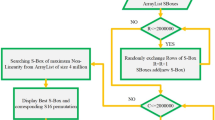
The substitution box (S-box) is the only nonlinear component of any block cipher. It hides the relationship between the key and the cipher text. Several methods are available in the literature for creating S-boxes of different sizes. However, the need to design \(4\; \times \;4\) S-boxes for lightweight encryption is in demand. The suggested method first generates the initial S-boxes from the elliptic curve points, and then the S-boxes are evolved with the help of algebraic group structures. Algebraic group structures have the potential to improve their cryptographic strength. The cryptographic properties of the suggested S-boxes, such as nonlinearity, algebraic degree, branch number, and bijectivity, are analyzed. We also present a comparative analysis of the suggested S-boxes with different standard S-boxes. The offered S-boxes are utilized in an image steganography scheme. First, the secret image is encrypted through the combination of the substitution operation and the bitwise XOR of the key. The enciphered image is hidden in the cover image using the least significant bit of steganographic scheme. Experimental results show that the suggested algorithm has a high security level and better stego-image quality.







Similar content being viewed by others
Data Availability
The authors confirm that the data supporting the findings of this study are available within the article.
References
Azam, N. A., Hayat, U., & Ullah, I. (2019). Efficient construction of a substitution box based on a Mordell elliptic curve over a finite field. Frontiers of Information Technology & Electronic Engineering, 20(10), 1378–1389.
Azam, N. A., Hayat, U., & Ullah, I. (2018). An injective S-box design scheme over an ordered isomorphic elliptic curve and its characterization. Security and Communication Networks, 2018, 1–9.
Adams, C., & Tavares, S. (1990). The structured design of cryptographically good S-boxes. Journal of cryptology, 3(1), 27–41.
Bhardwaj, R., & Sharma, V. (2016). Image steganography based on complemented message and inverted bit LSB substitution. Procedia Computer Science, 93, 832–838.
Bogdanov, A., Knudsen, L. R., Leander, G., Paar, C., Poschmann, A., Robshaw, M. J., & Vikkelsoe, C. (2007). PRESENT: An ultra-lightweight block cipher. In International workshop on cryptographic hardware and embedded systems (pp. 450–466). Springer, Berlin, Heidelberg.
Dawson, M. H., & Tavares, S. E. (1991). An expanded set of S-box design criteria based on information theory and its relation to differential-like attacks. In Workshop on the theory and application of of cryptographic techniques (pp. 352–367). Springer, Berlin, Heidelberg.
Dimitrov, M. M. (2020). On the design of chaos-based S-boxes. IEEE Access, 8, 117173–117181.
El-Latif, A. A. A., Abd-El-Atty, B., Belazi, A., & Iliyasu, A. M. (2021). Efficient chaos-based substitution-box and its application to image encryption. Electronics, 10(12), 1392.
Farah, T., Rhouma, R., & Belghith, S. (2017). A novel method for designing S-box based on chaotic map and teaching–learning-based optimization. Nonlinear Dynamics, 88(2), 1059–1074.
Hussain, I., Anees, A., & Al-Maadeed, T. A. (2023). A novel encryption algorithm using multiple semifield S-boxes based on permutation of symmetric group. Computational and Applied Mathematics, 42(2), 80.
Hayat, U., Azam, N. A., & Asif, M. (2018). A method of generating 8 × 8 substitution boxes based on elliptic curves. Wireless Personal Communications, 101(1), 439–451.
Han, Y. Y., He, Y. R., Liu, P. H., Zhang, D., Wang, Z. Q., & He, W. C. (2020). Construction and application of ZUC dynamic S-box based on chaotic system. Computer Research Development, 10, 2147–2157.
Ibrahim, S., & Abbas, A. M. (2021). Efficient key-dependent dynamic S-boxes based on permutated elliptic curves. Information Sciences, 558, 246–264.
Jamal, S. S., Shah, T., Farwa, S., & Khan, M. U. (2019). A new technique of frequency domain watermarking based on a local ring. Wireless Networks, 25(4), 1491–1503.
Jiang, Z., & Ding, Q. (2021). Construction of an S-box based on chaotic and bent functions. Symmetry, 13(4), 671.
Khan, H., Jamal, S. S., Hazzazi, M. M., Khan, M., & Hussain, I. (2023). New image encryption scheme based on Arnold map and cuckoo search optimization algorithm. Multimedia Tools and Applications, 82(5), 7419–7441.
Kim, K., Park, S., & Lee, S. (1993). Reconstruction of s2DES S-boxes and their immunity to differential cryptanalysis. In Joint workshop on information security and cryptology (pp. 59–72).
Kim, K., Park, S., & Lee, D. (1995). Securing DES S-boxes against three robust cryptanalysis. In Proceedings of the workshop on selected areas in cryptography (SAC'95).
Kumar, M., Soni, A., Shekhawat, A. R. S., & Rawat, A. (2022). Enhanced digital image and text data security using hybrid model of LSB steganography and AES cryptography technique. In 2022 2nd International conference on artificial intelligence and smart energy (ICAIS) (pp. 1453–1457). IEEE.
Khan, M., & Asghar, Z. (2018). A novel construction of substitution box for image encryption applications with Gingerbreadman chaotic map and S 8 permutation. Neural Computing and Applications, 29, 993–999.
Khan, M., & Shah, T. (2015). An efficient chaotic image encryption scheme. Neural Computing and Applications, 26, 1137–1148.
Leander, G., & Poschmann, A. (2007). On the classification of 4 bit S-boxes. In International workshop on the arithmetic of finite fields (pp. 159–176). Springer, Berlin, Heidelberg.
Lambić, D. (2018). S-box design method based on improved one-dimensional discrete chaotic map. Journal of Information and Telecommunication, 2(2), 181–191.
Lu, Q., Zhu, C., & Wang, G. (2019). A novel S-box design algorithm based on a new compound chaotic system. Entropy, 21(10), 1004.
Malik, M. S. M., Ali, M. A., Khan, M. A., Ehatisham-Ul-Haq, M., Shah, S. N. M., Rehman, M., & Ahmad, W. (2020). Generation of highly nonlinear and dynamic AES substitution-boxes (S-boxes) using chaos-based rotational matrices. IEEE Access, 8, 35682–35695.
Özkaynak, F. (2020). On the effect of chaotic system in performance characteristics of chaos based s-box designs. Physica A: Statistical Mechanics and its Applications, 550, 124072.
Shannon, C. E. (1949). Communication theory of secrecy systems. The Bell System Technical Journal, 28(4), 656–715.
Sarkar, S., & Syed, H. (2018). Bounds on differential and linear branch number of permutations. In Australasian conference on information security and privacy (pp. 207–224). Springer, Cham.
Saarinen, M. J. O. (2011). Cryptographic analysis of all 4 × 4-bit S-boxes. In International workshop on selected areas in cryptography (pp. 118–133). Springer, Berlin, Heidelberg.
Susanto, A., Mulyono, I. U. W., Fajar, M. R., & Febrian, G. A. R. (2019). A combination of hill cipher and LSB for image security. Scientific Journal of Informatics, 6(1), 2.
Wang, R. Z., & Chen, Y. S. (2006). High-payload image steganography using two-way block matching. IEEE Signal Processing Letters, 13(3), 161–164.
Wang, Y., Zhang, Z., Zhang, L. Y., Feng, J., Gao, J., & Lei, P. (2020). A genetic algorithm for constructing bijective substitution boxes with high nonlinearity. Information Sciences, 523, 152–166.
Wang, Y., Wong, K. W., Li, C., & Li, Y. (2012). A novel method to design S-box based on chaotic map and genetic algorithm. Physics Letters A, 376(6–7), 827–833.
Zhu, C., Wang, G., & Sun, K. (2018). Cryptanalysis and improvement on an image encryption algorithm design using a novel chaos based S-box. Symmetry, 10(9), 399.
Zamli, K. Z. (2021). Optimizing S-box generation based on the adaptive agent heroes and cowards algorithm. Expert Systems with Applications, 182, 115305.
Funding
The authors declare that no funds, grants, or other support were received during the preparation of this manuscript.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Authors have no relevant financial or non-financial interests to disclose. There is no competing interest between the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Arshad, S. Construction of 4 × 4 Substitution Box Using Elliptic Curves and Algebraic Group Structures. Wireless Pers Commun 131, 1913–1927 (2023). https://doi.org/10.1007/s11277-023-10526-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10526-w