Abstract
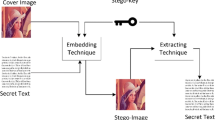
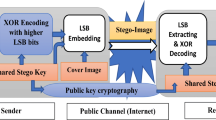
Generally, irreversible and reversible image steganography use the concept of encryption to produce a higher level of security. In this case, the payload is encrypted before embedding in the medium cover. However, it has more complexity if the size of the payload is high. Therefore, such a technique is required, which would be less complex and more secure than any of the existing encryption algorithms, even if the size of the payload is large. This paper possesses such an approach with the concept of payload Scattering. In the proposed approach payload is distributed into three components with the help of the primary cover image. The decomposed components are then embedded into RGB secondary cover image. The proposed approach eliminates the need for encryption and reduces the system’s complexity in payload design. It has been observed with the result that the distortion in the decomposed components SMap, EFactor and NError, has been significant enough to hide the payload. It has a deficient computation time compared with existing encryption algorithms. Therefore, the proposed method based on an embedded processing framework can be considered as the best alternative to the encryption algorithm to conceal the payload with low computation time as well as independence in the size of the payload.





Source: http://sipi.usc.edu/services/Miscellaneous (standard image dataset)







Similar content being viewed by others
Data Availability
Data sharing does not apply to this article as no datasets were generated or analyzed during the current study.
References
Hsieh, K. S., & Wang, C. M. (2022). Constructive image steganography using example-based weighted color transfer. Journal of Information Security and Applications, 65, 103126.
Liu, L., Meng, L., Wang, X., & Peng, Y. (2022). An image steganography scheme based on ResNet. Multimedia Tools and Applications, 81(27), 39803–39820.
Dey, D., Pattanayak, S., & Samanta, S. (2022). Chaotic based image steganography using polygonal method. In Nonlinear dynamics and applications (pp. 575–586). Springer.
Gupta, A., Shukla, H., & Gupta, M. (2022). A secure image steganography using X86 assembly LSB. NEU Journal for Artificial Intelligence and Internet of Things, 1(1), 38–47.
Durdu, A. (2022). A new reversible low-distortion steganography method that hides images into RGB images with low loss. Multimedia Tools and Applications, 81(1), 953–973.
Christiana Abikoye, O., Oluwaseun Ogundokun, R., Misra, S., & Agrawal, A. (2022). Analytical study on LSB-based image steganography approach. In Computational intelligence in machine learning (pp. 451–457). Springer.
Geetha, S., Punithavathi, P., Infanteena, A. M., & Sindhu, S. S. S. (2018). A literature review on image encryption techniques. International Journal of Information Security and Privacy, 12(3), 42–83.
Antonijevic, M., Jovanovic, D., Lazarevic, S., Mladenovic, D., Bukumira, M., & Bacanin, N. (2022). Target recognition approach using image local features in rehabilitation robots. Journal of Electronic Imaging, 31(6), 061810.
Peter, G., Sherine, A., Teekaraman, Y., Kuppusamy, R., & Radhakrishnan, A. (2022). Histogram shifting-based quick response steganography method for secure communication. Wireless Communications and Mobile Computing. https://doi.org/10.1155/2022/1505133
Wu, F., Zhou, X., Chen, Z., & Yang, B. (2021). A reversible data hiding scheme for encrypted images with pixel difference encoding. Knowledge-Based Systems, 234, 107583.
Qobbi, Y., Jarjar, A., Essaid, M., & Benazzi, A. (2022). New image encryption scheme based on dynamic substitution and hill cipher. In WITS 2020 (pp. 797–808). Springer.
Wang, Z. H., Lee, C. F., & Chang, C. Y. (2013). Histogram-shifting-imitated reversible data hiding. Journal of Systems and Software, 86(2), 315–323.
Kaur, S., Singh, S., Kaur, M., & Lee, H. N. (2022). A systematic review of computational image steganography approaches. Archives of Computational Methods in Engineering, 29, 4775–4797.
Miss, N. A., & Shaikh, R. (2016). A keyless approach for RDH in encrypted images using visual cryptography. Procedia Computer Science, 78, 125–131.
Harshini, K., Naresh, B., Sahitya, K., Satya Vara Prasad, B. B. V., & Dasu, B. T. (2022). Enhanced security with crystography using AES and LSB. In Confidential computing (pp. 177–185). Springer.
Abood, M. H. (2017). An efficient image cryptography using hash-LSB steganography with RC4 and pixel shuffling encryption algorithms. In 2017 annual conference on new trends in information & communications technology applications (NTICT) (pp. 86–90). IEEE.
Singh, R. K., & Shaw, D. K. (2018). A hybrid concept of cryptography and dual watermarking (LSB_DCT) for data security. International Journal of Information Security and Privacy, 12(1), 1–12.
Maazouz, M., Toubal, A., Bengherbia, B., Houhou, O., & Batel, N. (2022). FPGA implementation of a chaos-based image encryption algorithm. Journal of King Saud University-Computer and Information Sciences, 34, 9926.
Chakraborty, S., Jalal, A. S., & Bhatnagar, C. (2013). An efficient bit plane X-OR algorithm for irreversible image steganography. International Journal of Trust Management in Computing and Communications, 1(2), 140–155.
Sharma, N., & Batra, U. (2021). An enhanced Huffman-PSO based image optimization algorithm for image steganography. Genetic Programming and Evolvable Machines, 22(2), 189–205.
Dhawan, S., & Gupta, R. (2021). Analysis of various data security techniques of steganography: A survey. Information Security Journal: A Global Perspective, 30(2), 63–87.
Funding
We did not receive any funding from a private or government body for this research work.
Author information
Authors and Affiliations
Contributions
All authors have an equal contribution.
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they do not have any conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rathor, S., Agrawal, S.C., Bhadoria, R.S. et al. Secure and Embedded Processing Framework for Payload Scattering in Image Steganography with Low Computation Time. Wireless Pers Commun 130, 2679–2695 (2023). https://doi.org/10.1007/s11277-023-10398-0
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10398-0