Abstract
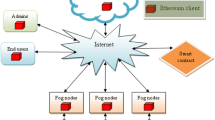
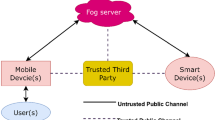
Fog computing network plays a significant role in enhancing the communication between the end users and the cloud server accompanying high security. The quality of service of the systems could be greatly enhanced by these fog computing technologies that provide high computation capability, storage and enhanced network connectivity. The transmission of data through this technology is highly vulnerable to various threatening especially medical data are highly vulnerable due to their sensitivity. In this research, a trust based fog computing authentication model is enabled for assuring the security of the data transmission. The proposed model is executed in five different phases that includes setup phase, user registration phase, Fog node registration phase, login phase and authentication phase and each phase performs a specific function to improve the security. In each phase the data are transmitted in the encrypted form that is performed using the Advanced Encryption Standard algorithm that ensured the security of the data and this algorithm could be enabled to both public and private sectors. In every phase the data are authenticated and the users are validated for the proceeding of authentication and this authorized access enhances the security level of the systems. The efficiency of the proposed trust based fog computing authentication model is proved by measuring the parameters detection rate, computation time, storage capability, vulnerability rate and privacy ratio that attained the improvement of 5% in detection rate, 42% in computational time, 31.51% memory usage, 82.41% vulnerability rate and 27.53% privacy ratio that shows the superiority of the proposed method.











Similar content being viewed by others
Data Availability
No new data were generated or analyzed in support of this research.
Code Availability
We can share the code after getting the acceptances.
References
Zhao, J., Zeng, P., & Choo, K. K. R. (2021). An efficient access control scheme with outsourcing and attribute revocation for fog-enabled E-health. IEEE Access, 9, 13789–13799.
Wu, T.-Y., Lee, Z., Obaidat, M. S., Kumari, S., Kumar, S., & Chen, C.-M. (2020). An authenticated key exchange protocol for multi-server architecture in 5G networks. IEEE Access, 8, 28096–28108.
Nabeeh, N. A., Abdel-Basset, M., El-Ghareeb, H. A., & Aboelfetouh, A. (2019). Neutrosophic multi-criteria decision making approach for IoT-based enterprises. IEEE Access, 7, 59559–59574.
Yu, R., Xue, G., Kilari, V. T., & Zhang, X. (2018). The fog of things paradigm: Road toward on-demand Internet of Things. IEEE Communications Magazine, 56(9), 48–54.
Oteafy, S. M. A., & Hassanein, H. S. (2018). IoT in the fog: A roadmap for data-centric IoT development. IEEE Communications Magazine, 56(3), 157–163.
Li, L., Wang, Z., & Li, N. (2020). Efficient attribute-based encryption outsourcing scheme with user and attribute revocation for fog-enabled IoT. IEEE Access, 8, 176738–176749.
Tange, K., Donno, M. D., Fafoutis, X., & Dragoni, N. (2020). A systematic survey of industrial internet of things security: Requirements and fog computing opportunities. IEEE Communications Surveys and Tutorials, 22(4), 2489–2520.
Tu, S., Waqas, M., Huang, F., Abbas, G., & Abbas, Z. H. (2021). A revocable and outsourced multi-authority attribute-based encryption scheme in fog computing. Computer Networks, 195, 108196.
Puliafito, C., Mingozzi, E., & Anastasi, G. (2017). Fog computing for the internet of mobile things: Issues and challenges. In Smart computing (SMARTCOMP), 2017 IEEE international conference (pp. 1–6).
Atlam, H., Walters, R., & Wills, G. (2018). Fog computing and the Internet of Things: A review. Big Data and Cognitive Computing, 2(2), 10.
Sha, K., Wei, W., Yang, T. A., Wang, Z., & Shi, W. (2018). On security challenges and open issues in internet of things. Future Generation Computer Systems, 83, 326–337.
Roman, R., et al. (2018). Mobile edge computing, fog: A survey and analysis of security threats and challenges. Future Generation Computer Systems, 78, 680–698.
Li, Y., Dong, Z., Sha, K., Jiang, C., Wan, J., & Wang, Y. (2019). Tmo: Time domain outsourcing attribute-based encryption scheme for data acquisition in edge computing. IEEE Access, 7, 40240–40257.
Bonomi, F., Milito, R., Zhu, J., & Addepalli, S. (2012). Fog computing and its role in the internet of things. In Proceedings of the first edition of the MCC workshop on Mobile cloud computing (pp. 13–16).
Roca, D., Milito, R., Nemirovsky, M., & Valero, M. (2018). Tackling IoT ultra large scale systems: Fog computing in support of hierarchical emergent behaviors. In Fog computing in the internet of things (pp. 33–48). Springer.
Fan, K., Xu, H., Gao, L., Li, H., & Yang, Y. (2019). Efficient and privacy preserving access control scheme for fog-enabled IoT. Future Generation Computer Systems, 99, 134–142.
Zhou, Z., Dong, M., Ota, K., Wang, G., & Yang, L. T. (2016). Energy-efficient resource allocation for D2D communications underlaying cloud-ran-based LTE-A networks. IEEE Internet of Things Journal, 3(3), 428–438.
Li, D., Liu, J., Wu, Q., & Guan, Z. (2019). Efficient CCA2 secure flexible and publicly-verifiable fine-grained access control in fog computing. IEEE Access, 7, 11688–11697.
Ming, Y., He, B., & Wang, C. (2021). Efficient revocable multi-authority attribute-based encryption for cloud storage. IEEE Access, 9, 42593–42603.
Huang, K. (2021). Secure efficient revocable large universe multi-authority attribute-based encryption for cloud-aided IoT. IEEE Access, 9, 53576–53588.
Hei, Y., Liu, J., Feng, H., Li, D., Liu, Y., & Wu, Q. (2021). Making MA-ABE fully accountable: A blockchain-based approach for secure digital right management. Computer Networks, 191, 108029.
Ling, J., Chen, J., Chen, J., & Gan, W. (2021). Multiauthority attribute-based encryption with traceable and dynamic policy updating. Security and Communication Networks, 2021.
Funding
This research did not receive any specific funding.
Author information
Authors and Affiliations
Contributions
All authors have made substantial contributions to conception and design, revising the manuscript, and the final approval of the version to be published. Also, all authors agreed to be accountable for all aspects of the work in ensuring that questions related to the accuracy or integrity of any part of the work are appropriately investigated and resolved.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Satheesh, K.K.S.V.A., Sree, T.K. Enhancing Security Using Secure Authentication Model in Fog Computing Model. Wireless Pers Commun 130, 909–933 (2023). https://doi.org/10.1007/s11277-023-10313-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10313-7