Abstract
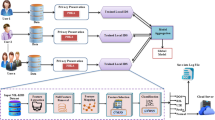
In recent years, the rapid growth of information technology organizations causes ability to meet their demands such as scalability, mobility and flexibility. The security and privacy is a major issue of those organizations that’s why they move the data to the cloud. Meanwhile, the security in cloud has become an important issue in the growing demand of cloud computing, Due to the nature characteristics of cloud, those confidential data are vulnerable to attacks/malicious or intruders. Several Intrusion Detection System (IDS) have been proposed for cloud environment to enhance the security problem but they are not possible to solve those issues with better accuracy, due to the recent real-time intruders. However, those IDSs are possible to solve and resist limited and known attacks. In this paper, we propose Optimal Cluster based Intrusion Detection System for defence against attacks in web and cloud computing environments (OC-IDS). We use hybrid optimization algorithm i.e. Multi-verse is combined with Chaotic Atom search optimization (MCA) algorithm for pre-processing which removes the unwanted/repeated data in dataset. We introduce a Chaotic Manta-ray Foraging Optimization (CMFO) based clustering technique which segment the data in different groups. Then, we develop hybrid machine learning technique i.e. Modified Teacher Learning based Deep Neural Network (MTL-DNN) which categorize the attack in cloud environment as a novelty of this study. Finally, the proposed OC-IDS technique can evaluate through standard open source datasets are KDD cup’99 and MSL-KDD, the performance of proposed and existing techniques are compared with different metrics such as accuracy, precision, recall and F-measure. Our proposed OC IDS MTL-DNN attains 95.01% accuracy in KDD cup’99 dataset.





Similar content being viewed by others
Data Availability
The already existing algorithms data used to support the findings of this study have not been made available.
References
Fenanir, S., Semchedine, F., & Baadache, A. (2019). A machine learning-based lightweight intrusion detection system for the internet of things. Rev. d’Intelligence Artif., 33(3), 203–211.
Chiba, Z., Abghour, N., Moussaid, K., & Rida, M. (2019). Intelligent approach to build a Deep Neural Network based IDS for cloud environment using combination of machine learning algorithms. Computers Security., 86, 291–317.
Chowdhury, R., Sen, S., Roy, A., & Saha, B. (2022). An optimal feature based network intrusion detection system using bagging ensemble method for real-time traffic analysis. Multimedia Tools and Applications. 1–23.
Khraisat, A., Gondal, I., Vamplew, P., & Kamruzzaman, J. (2019). Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity, 2(1), 1–22.
Avritzer, A., Ferme, V., Janes, A., Russo, B., van Hoorn, A., Schulz, H., Menasché, D., & Rufino, V. (2020). Scalability assessment of microservice architecture deployment configurations: A domain-based approach leveraging operational profiles and load tests. Journal of Systems and Software., 165, 110564.
Deng, L., Li, D., Yao, X., & Wang, H. (2019). Retracted article: Mobile network intrusion detection for IoT system based on transfer learning algorithm. Cluster Computing, 22(4), 9889–9904.
Tabrizchi, H., & Kuchaki, R. M. (2020). A survey on security challenges in cloud computing: Issues, threats, and solutions. The Journal of Supercomputing., 76(12), 9493–9532.
El Sibai, R., Gemayel, N., Bou Abdo, J., & Demerjian, J. (2020). A survey on access control mechanisms for cloud computing. Transactions on Emerging Telecommunications Technologies., 31(2), 3720.
Rashid, A., & Chaturvedi, A. (2019). Virtualization and its role in cloud computing environment. International Journal of Computer Sciences and Engineering, 7(4), 1131–1136.
Kumari, P., & Kaur, P. (2021). A survey of fault tolerance in cloud computing. Journal of King Saud University-Computer and Information Sciences, 33(10), 1159–1176.
Sun, L., Jiang, X., Ren, H., & Guo, Yi. (2020). Edge-cloud computing and artificial intelligence in internet of medical things: Architecture, technology and application. IEEE Access, 8, 101079–101092.
Zhou, Y., Ling Liu, Lu., Wang, N. H., Cui, X., Jie, Wu., Peng, Y., Qi, Y., & Xing, C. (2020). Service-aware 6G: An intelligent and open network based on the convergence of communication, computing and caching. Digital Communications and Networks, 6(3), 253–260.
Pourghaffari, A., Barari, M., & Sedighian, K. S. (2019). An efficient method for allocating resources in a cloud computing environment with a load balancing approach. Concurrency and Computation: Practice and Experience., 31(17), e5285.
Tarahomi, M., Izadi, M., & Ghobaei-Arani, M. (2021). An efficient power-aware VM allocation mechanism in cloud data centers: A micro genetic-based approach. Cluster Computing, 24(2), 919–934.
Dhaya, R., Kanthavel, R., & Venusamy, K. (2021). Dynamic secure and automated infrastructure for private cloud data center. Annals of Operations Research, 1–21.
Kumar, M., & Singh, A. K. (2020). Distributed intrusion detection system using blockchain and cloud computing infrastructure. In 2020 4th international conference on trends in electronics and informatics (ICOEI)(48184) (pp. 248–252). IEEE.
Abusitta, A., Bellaiche, M., Dagenais, M., & Halabi, T. (2019). A deep learning approach for proactive multi-cloud cooperative intrusion detection system. Future Generation Computer Systems, 98, 308–318.
Moualla, S., Khorzom, K., & Jafar, A. (2021). Improving the performance of machine learning-based network intrusion detection systems on the UNSW-NB15 dataset. Computational Intelligence and Neuroscience. 2021.
Attaran, M., & Woods, J. (2019). Cloud computing technology: Improving small business performance using the Internet. Journal of Small Business & Entrepreneurship, 31(6), 495–519.
Chen, M., Wang, N., Zhou, H., & Chen, Y. (2018). FCM technique for efficient intrusion detection system for wireless networks in cloud environment. Computers & Electrical Engineering, 71, 978–987.
Dey, S., Ye, Q., & Sampalli, S. (2019). A machine learning based intrusion detection scheme for data fusion in mobile clouds involving heterogeneous client networks. Information Fusion, 49, 205–215.
Aldwyan, Y., & Sinnott, R. O. (2019). Latency-aware failover strategies for containerized web applications in distributed clouds. Future Generation Computer Systems, 101, 1081–1095.
Yaghoubi, M., & Maroosi, A. (2020). Simulation and modeling of an improved multi-verse optimization algorithm for QoS-aware web service composition with service level agreements in the cloud environments. Simulation Modelling Practice and Theory, 103, 102090.
Sanaj, M. S., & Prathap, P. J. (2020). An efficient approach to the map-reduce framework and genetic algorithm based whale optimization algorithm for task scheduling in cloud computing environment. Materials Today: Proceedings.
Sharma, A. K., Upreti, K., & Vargis, B. (2020). Experimental performance analysis of load balancing of tasks using honey bee inspired algorithm for resource allocation in cloud environment. Materials Today: Proceedings.
Wangfi, S., Wang, W., & Tan, Y. (2020). Internet cross-border service model based on 5G environment and cloud computing data platform. Microprocessors and Microsystems, p. 103520.
Shamshirband, S., Fathi, M., Chronopoulos, A. T., Montieri, A., Palumbo, F., & Pescapè, A. (2020). Computational intelligence intrusion detection techniques in mobile cloud computing environments: Review, taxonomy, and open research issues. Journal of Information Security and Applications, 55, 102582.
Ibrahim, G. J., Rashid, T. A., & Akinsolu, M. O. (2020). An energy efficient service composition mechanism using a hybrid meta-heuristic algorithm in a mobile cloud environment. Journal of Parallel and Distributed Computing, 143, 77–87.
Samriya, J. K., & Kumar, N. (2020). A novel intrusion detection system using hybrid clustering-optimization approach in cloud computing. Materials Today: Proceedings.
SaiSindhuTheja, R., & Shyam, G. K. (2021). An efficient metaheuristic algorithm based feature selection and recurrent neural network for DoS attack detection in cloud computing environment. Applied Soft Computing, 100, 106997.
Jaber, A. N., & Rehman, S. U. (2020). FCM–SVM based intrusion detection system for cloud computing environment. Cluster Computing., 23(4), 3221–3231.
Mayuranathan, M., Murugan, M., & Dhanakoti, V. (2021). Best features based intrusion detection system by RBM model for detecting DDoS in cloud environment. Journal of Ambient Intelligence and Humanized Computing, 12(3), 3609–3619.
Velliangiri, S., & Premalatha, J. (2019). Intrusion detection of distributed denial of service attack in cloud. Cluster Computing, 22(5), 10615–10623.
Aldallal, A., & Alisa, F. (2021). Effective intrusion detection system to secure data in cloud using machine learning. Symmetry, 13(12), 2306.
Wen, L. (2021). Cloud computing intrusion detection technology based on BP-NN. Wireless Personal Communications, 1–18.
Thilagam, T., & Aruna, R. (2021). Intrusion detection for network based cloud computing by custom RC-NN and optimization. ICT Express, 7(4), 512–520.
Srilatha, D., & Shyam, G. K. (2021). Cloud-based intrusion detection using kernel fuzzy clustering and optimal type-2 fuzzy neural network. Cluster Computing, 24(3), 2657–2672.
Sandosh, S., Govindasamy, V., & Akila, G. (2020). Enhanced intrusion detection system via agent clustering and classification based on outlier detection. Peer-to-Peer Networking and Applications, 13(3), 1038–1045.
Funding
There is no funding from any Research or Funding Agency.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that we have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Maheswari, K.G., Siva, C. & Priya, G.N. An Optimal Cluster Based Intrusion Detection System for Defence Against Attack in Web and Cloud Computing Environments. Wireless Pers Commun 128, 2011–2037 (2023). https://doi.org/10.1007/s11277-022-10030-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-10030-7