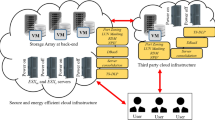
Abstract
Cloud computing allows accessing data from anywhere; Cloud databases play an important role in storing requests for access management. These requests require authorization management which has become a crucial area in access control. The request-response paradigm plays an important role in the PEP–PDP architecture. Many applications are available in literature based on the centralized PEP–PDP architecture. In this architecture, performance degrades with the increase in requests. Failure of PDP increases while handling requests from multiple PEPs. The proposed work extends the existing centralized PEP–PDP architecture to distributed architecture with PEP side caching to achieve scalability. In the proposed architecture, all PEPs employ side caching to improve efficiency. Various simulations and validation checks are performed to validate the architecture. Simulation results show proposed architecture is significantly efficient in handling large requests in contrast to existing single PEP-PDP and multiple PEP-single PEP architectures.












Similar content being viewed by others
Data Availability
All data generated or analysed during this study are included in this published article.
Code Availability
The code developed during the current study are available from the corresponding author on reasonable request.
References
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey on security issues and solutions at different layers of Cloud computing. The Journal of Supercomputing, 63(2), 561–592.
Hsu, C. H., Ma, J., & Obaidat, M. S. (2014). Dynamic intelligence towards merging cloud and communication services. Information Systems Frontiers, 16(1), 1–5.
Flahive, A., Taniar, D., & Rahayu, W. (2013). Ontology as a Service (OaaS): A case for sub-ontology merging on the cloud. The Journal of Supercomputing, 65(1), 185–216.
Petrov, C. (2021). 25+ Impressive big data statistics for 2021. https://techjury.net/blog/big-data- statistics/#gref
Petters, J. E. F. F. (2020, September 28). Data privacy guide: definitions, explanations and legislation. https://Www.Varonis.Com/Blog/Data-Privacy/.
Al-Gburi, A., Al-Hasnawi, A., & Lilien, L. (2018). Differentiating security from privacy in internet of things: a survey of selected threats and controls. In Computer and network security essentials, (pp. 153–172). Springer, Cham.
Sharma, S., Singh, S., Singh, A., & Kaur, R. (2016). Virtualization in cloud computing. International Journal of Scientific Research in Science, Engineering and Technology, 2, 181–186.
Devi, V. A. & Nayyar, A. (2021). Evaluation of geotagging twitter data using sentiment analysis during COVID-19. In Proceedings of the second international conference on information management and machine intelligence, (pp. 601–608). Springer, Singapore.
Daradoumis, T., Bassi, R., Xhafa, F., & Caballé, S. (2013). A review on massive e-learning (MOOC) design, delivery and assessment. In 2013 eighth international conference on P2P, parallel, grid, cloud and internet computing (pp. 208–213). IEEE.
Mehmi, S., Verma, H. K., & Sangal, A. L. (2014). Smart grid cloud for Indian power sector. In International conference on recent advances and innovations in engineering (ICRAIE-2014) (pp. 1–6). IEEE.
Bhatia, R. (2020). Interoperability solutions for blockchain. In 2020 International conference on smart technologies in computing, electrical and electronics (ICSTCEE) (pp. 381–385). IEEE.
Singh, M. & Singh, S. (2014). Review of implicit security mechanisms for cloud computing. International Journal of Computer Applications, 106(17).
Verma, A. & Kaushal, S. (2011). Cloud computing security issues and challenges: a survey. In International conference on advances in computing and communications (pp. 445–454). Springer, Berlin, Heidelberg.
Shikare, D. & Shetty, S. D. (2014). Supercloud–need, issues and challenges. International Journal of Engineering Research, 3(5).
Sharma, R., Kumar, S., & Trivedi, M. C. (2013). Mobile cloud computing: Bridging the gap between cloud and mobile devices. In 2013 5th international conference and computational intelligence and communication networks (pp. 553–555). IEEE.
Mackenzie, R. J. (2021). 4 ways that the cloud is changing research. https://Www.Technologynetworks.Com/Informatics/Lists/4-Ways-That-the-Cloud-Is-Changing-Research-315952.
Gurucul Solutions Pvt Ltd. (n.d.). 2020 insider threat survey report. https://Gurucul.Com/2020-Insider-Threat-Survey-Report. Retrieved June 5, 2021, from https://gurucul.com/2020-insider-threat-survey-report.
Tabrizchi, H., & Rafsanjani, M. K. (2020). A survey on security challenges in cloud computing: Issues, threats, and solutions. The Journal of Supercomputing, 76(12), 9493–9532.
Liu, L., De Vel, O., Han, Q. L., Zhang, J., & Xiang, Y. (2018). Detecting and preventing cyber insider threats: A survey. IEEE Communications Surveys & Tutorials, 20(2), 1397–1417.
Ramachandran, M., & Chang, V. (2016). Towards performance evaluation of cloud service providers for cloud data security. International Journal of Information Management, 36(4), 618–625.
Barrowclough, J. P., & Asif, R. (2018). Securing cloud hypervisors: A survey of the threats, vulnerabilities, and countermeasures. Security and Communication Networks, 2018, 1–20.
Sandhu, R. S., & Samarati, P. (1994). Access control: Principle and practice. IEEE Communications Magazine, 32(9), 40–48.
Kizza, J., & Kizza, F. M. (2008). Access control, authentication, and authorization (pp. 180–208). IGI Global.
Sail, S. & Bouden, H. (2018). A multi-factor authentication scheme to strength data-storage access. In International conference on big data, cloud and applications (pp. 67–77). Springer, Cham.
Anakath, A. S., Rajakumar, S., & Ambika, S. (2019). Privacy preserving multi factor authentication using trust management. Cluster Computing, 22(5), 10817–10823.
Chen, H. C. J., Violetta, M. A., & Yang, C. Y. (2013). Contract RBAC in cloud computing. The Journal of Supercomputing, 66(2), 1111–1131.
Xu, J., Yu, Y., Meng, Q., Wu, Q., & Zhou, F. (2020). Role-based access control model for cloud storage using identity-based cryptosystem. Mobile Networks and Applications, 1–18.
Morisset, C., Willemse, T. A., & Zannone, N. (2019). A framework for the extended evaluation of ABAC policies. Cybersecurity, 2(1), 1–21.
Rana, S., & Mishra, D. (2020). Efficient and secure attribute based access control architecture for smart healthcare. Journal of Medical Systems, 44(5), 1–11.
Ahmadi, S., Nassiri, M., & Rezvani, M. (2020). XACBench: A XACML policy benchmark. Soft Computing, 24(21), 16081–16096.
Rezvani, M., Rajaratnam, D., Ignjatovic, A., Pagnucco, M., & Jha, S. (2019). Analyzing XACML policies using answer set programming. International Journal of Information Security, 18(4), 465–479.
de Carvalho, R. M., Del Prete, C., Martin, Y. S., Araujo Rivero, R. M., Önen, M., Schiavo, F. P., Rumín, Á. C., Mouratidis, H., Yelmo, J. C., & Koukovini, M. N. (2020). Protecting citizens’ personal data and privacy: joint effort from GDPR EU cluster research projects. SN Computer Science, 1(4), 1–16.
Bertin, E., Hussein, D., Sengul, C., & Frey, V. (2019). Access control in the Internet of Things: A survey of existing approaches and open research questions. Annals of Telecommunications, 74(7), 375–388.
Bruno, E., Gallier, R., & Gabillon, A. (2019). Enforcing access controls in IoT networks. In International conference on future data and security engineering (pp. 429–445). Springer, Cham.
Yaseen, Q., Jararweh, Y., Panda, B., & Althebyan, Q. (2017). An insider threat aware access control for cloud relational databases. Cluster Computing, 20(3), 2669–2685.
Yaseen, Q. & Panda, B. (2010). Predicting and preventing insider threat in relational database systems. In IFIP international workshop on information security theory and practices (pp. 368–383). Springer, Berlin, Heidelberg.
Yaseen, Q., & Panda, B. (2012). Insider threat mitigation: Preventing unauthorized knowledge acquisition. International Journal of Information Security, 11(4), 269–280.
Lazouski, A., Martinelli, F., Mori, P., & Saracino, A. (2017). Stateful data usage control for android mobile devices. International Journal of Information Security, 16(4), 345–369.
Da Silva, C. E., Diniz, T., Cacho, N., & de Lemos, R. (2018). Self-adaptive authorization in OpenStack cloud platform. Journal of Internet Services and Applications, 9(1), 1–17.
Elgedawy, I., Khurshid, S., Masood, R., & Shibli, M. A. (2018). CRESCENT+: A self-protecting framework for reliable composite web service delivery. Iran Journal of Computer Science, 1(2), 65–87.
Nyrkov, A., Romanova, Y., Ianiushkin, K., & Li, I. (2018). Data processing model in hierarchical multi-agent system based on decentralized attribute-based encryption. In Energy management of municipal transportation facilities and transport (pp. 429–438). Springer, Cham.
Son, H. X., Nguyen, M. H., & Vo, H. K. (2019). Toward an privacy protection based on access control model in hybrid cloud for healthcare systems. In International joint conference: 12th international conference on computational intelligence in security for information systems (CISIS 2019) and 10th international conference on European transnational education (ICEUTE 2019) (pp. 77–86). Springer, Cham.
Cao, Y., Huang, Z., Yu, Y., Ke, C., & Wang, Z. (2020). A topology and risk-aware access control framework for cyber-physical space. Frontiers of Computer Science, 14(4), 1–16.
Ryan, D., De Leon, M. P., Grant, N., Butler, B., Vogel, S., Mirz, M., & Lyons, P. (2019). Deriving policies from connection codes to ensure ongoing voltage stability. Energy Informatics, 2(1), 1–14.
Elmisery, A. M., Rho, S., & Aborizka, M. (2019). A new computing environment for collective privacy protection from constrained healthcare devices to IoT cloud services. Cluster Computing, 22(1), 1611–1638.
Oglaza, A., Laborde, R., Zaraté, P., Benzekri, A., & Barrère, F. (2017). A new approach for managing Android permissions: Learning users’ preferences. EURASIP Journal on Information Security, 2017(1), 1–16.
Krempel, E., Birnstill, P., & Beyerer, J. (2017). A Privacy-Aware Fall Detection System for Hospitals and Nursing Facilities. European Journal for Security Research, 2(2), 83–95.
Amin, S. O., Siddiqui, M. S., & Hong, C. S. (2008). A novel IPv6 traceback architecture using COPS protocol. Annals of Telecommunications-Annales des Télécommunications, 63(3), 207–221.
Liu, Y., Zhang, J., & Zhan, J. (2021). Privacy protection for fog computing and the internet of things data based on blockchain. Cluster Computing, 24(2), 1331–1345.
Vassis, D., Belsis, P., Skourlas, C., & Pantziou, G. (2010). Providing advanced remote medical treatment services through pervasive environments. Personal and Ubiquitous Computing, 14(6), 563–573.
Basile, C., Cappadonia, A., & Lioy, A. (2011). Network-level access control policy analysis and transformation. IEEE/ACM Transactions On Networking, 20(4), 985–998.
Gogoulos, F. I., Antonakopoulou, A., Lioudakis, G. V., Mousas, A. S., Kaklamani, D. I., & Venieris, I. S. (2014). On the design of a privacy aware authorization engine for collaborative environments. Electronic Markets, 24(2), 101–112.
Cuevas, A., Febrero, M., & Fraiman, R. (2004). An anova test for functional data. Computational Statistics & Data Analysis, 47(1), 111–122.
Kim, T. K. (2017). Understanding one-way ANOVA using conceptual figures. Korean Journal of Anesthesiology, 70(1), 22–26.
Górecki, T., & Smaga, Ł. (2015). A comparison of tests for the one-way ANOVA problem for functional data. Computational Statistics, 30(4), 987–1010.
Deng, F., Lu, J., Wang, S. Y., Pan, J., & Zhang, L. Y. (2019). A distributed PDP model based on spectral clustering for improving evaluation performance. World Wide Web, 22(4), 1555–1576.
Salesforce.com. (n.d.). 12 Benefits of Cloud Computing. https://Www.Salesforce.Com/Products/Platform/Best-Practices/Benefits-of-Cloud-Computing/. Retrieved June 5, 2021, from https://www.salesforce.com/products/platform/best-practices/benefits-of-cloud-computing/
Indu, I., Anand, P. R., & Bhaskar, V. (2018). Identity and access management in cloud environment: Mechanisms and challenges. Engineering Science and Technology, an International Journal, 21(4), 574–588.
Funding
This research did not receive any specific grant from funding agencies in the public, commercial, or not-for-profit sectors.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Deep, G., Sidhu, J. & Mohana, R. Distributed PEP–PDP Architecture for Cloud Databases. Wireless Pers Commun 128, 1733–1761 (2023). https://doi.org/10.1007/s11277-022-10017-4
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-10017-4