Abstract
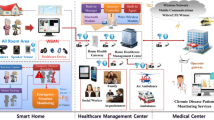
Continuous health status monitoring of the medical user (MU) with cloud-based wireless body area network (WBAN) is a key emerging technology in e-healthcare. Using this technology, WBAN continuously uploads the present physiological parameters to cloud. Cloud analyzes the private health information (PHI) of MU and detects any medical emergency of the MU instantly. Cloud checks the infrastructural parameters including the location information of all MSPs connected to the system and it selects the most appropriate MSP to address the medical emergency. This MSP selection task has to be performed efficiently so that privacy of PHI and location of MU is preserved. In the existing work, a trusted third party, namely, trusted authority (TA) actively participates in the emergency detection as well as in MSP selection process. This involvement of TA may compromise the privacy of MU as well as makes the system suffer from single-point failure problem. Furthermore, the existing work suffers from false positive medical emergency. The aim of the present work is to propose a framework that preserves the privacy of MU, eliminates the role of TA during medical emergency detection and MSP selection process to overcome single-point failure problem, and to ensure that it does not generate false positive emergency alert. The most appropriate MSP selection for an MU is obtained using Euclidean distance between MU and MSP attributes, computed in encrypted domain using homomorphic encryption. The proposed scheme has been scrutinized through an adversary model and simulated using ProVerif tool and found to be secured and privacy-preserving. Results of simulation shows that the time taken by MU in present work during medical emergency detection phase is better in comparison to the existing work. Therefore, the proposed framework can be widely adopted for deployment in smart healthcare.






Similar content being viewed by others
References
Movassaghi, S., Abolhasan, M., Lipman, J., Smith, D., & Jamalipour, A. (2014). Wireless body area networks: A survey. IEEE Communications Surveys Tutorials, 16(3), 1658–1686. https://doi.org/10.1109/SURV.2013.121313.00064.
Latré, B., Bart, B., Moerman, I., Blondia, C., & Demeester, P. (2011). A survey on wireless body area networks. Wireless Networks, 17(1), 1–18. https://doi.org/10.1007/s11276-010-0252-4.
Pattanayak, A., & Dhal, S. (2020). Cloud enabled body area network. In S. K. Biswash & S. K. Addya (Eds.), Cloud network management: An IoT based framework (1st ed., pp. 65–85). London: Chapman and Hall/CRC. https://doi.org/10.1201/9780429288630.
Yu, W., Liu, Z., Chen, C., Yang, B., & Guan, X. (2017). Privacy-preserving design for emergency response scheduling system in medical social networks. Peer-to-Peer Networking and Applications, 10(2), 340–356. https://doi.org/10.1007/s12083-016-0429-4.
Lai, X., Liu, Q., Wei, X., Wang, W., Zhou, G., & Han, G. (2013). A survey of body sensor networks. Sensors, 13(5), 5406–5447. https://doi.org/10.3390/s130505406.
Chen, M., Gonzalez, S., Vasilakos, A., Athanasios, C., Huasong, L., & Victor, C. (2011). Body area networks: A survey. Mobile Networks and Applications, 16(2), 171–193. https://doi.org/10.1007/s11036-010-0260-8.
Maitra, T., & Roy, S. (2017). Research challenges in BAN due to the mixed WSN features: Some perspectives and future directions. IEEE Sensors Journal, 17(17), 5759–5766. https://doi.org/10.1109/JSEN.2017.2725324.
Liang, X., Lu, R., Chen, L., Lin, X., & Shen, X. (2011). PEC: A privacy-preserving emergency call scheme for mobile healthcare social networks. Journal of Communications and Networks, 13(2), 102–112. https://doi.org/10.1109/JCN.2011.6157409.
Zhang, K., Liang, X., Barua, M., Lu, R., & Shen, X. S. (2014). PHDA: A priority based health data aggregation with privacy preservation for cloud assisted WBANs. Information Sciences, 284, 130–141. https://doi.org/10.1016/j.ins.2014.06.011.
Huang, Q., Wang, L., & Yang, Y. (2017). Secure and privacy-preserving data sharing and collaboration in mobile healthcare social networks of smart cities. Security and Communication Networks. https://doi.org/10.1155/2017/6426495.
Sun, J., Fang, Y., & Zhu, X. (2010). Privacy and emergency response in e-healthcare leveraging wireless body sensor networks. IEEE Wireless Communications, 17(1), 66–73. https://doi.org/10.1109/MWC.2010.5416352.
Li, C. T., Lee, C. C., & Weng, C. Y. (2016). A secure cloud-assisted wireless body area network in mobile emergency medical care system. Journal of Medical Systems, 40(5), 1–15. https://doi.org/10.1007/s10916-016-0474-9.
Chiou, S., & Liao, Z. (2018). A real-time, automated and privacy-preserving mobile emergency-medical-service network for informing the closest rescuer to rapidly support mobile-emergency-call victims. IEEE Access, 6, 35787–35800. https://doi.org/10.1109/ACCESS.2018.2847030.
Lin, H., Shao, J., Zhang, C., & Fang, Y. (2013). CAM: Cloud-assisted privacy preserving mobile health monitoring. IEEE Transactions on Information Forensics and Security, 8(6), 985–997. https://doi.org/10.1109/TIFS.2013.2255593.
Shi, E., Bethencourt, J., Chan, T., Song, D., & Perrig, A., (2007). Multi-dimensional range query over encrypted data, In Proceedings of IEEE Symposium on Security and Privacy, (pp. 350–364). https://doi.org/10.1109/SP.2007.29
Hore, B., Mehrotra, S., Canim, M., & Kantarcioglu, M. (2012). Secure multidimensional range queries over outsourced data. The VLDB Journal, 21(3), 333–358. https://doi.org/10.1007/s00778-011-0245-7.
Dutta, R., Barua, R., & Sarkar, P., (2004). Pairing-based cryptographic protocols: A survey, Cryptology ePrint Archive, https://eprint.iacr.org/2004/064.
Dijk, M. V., Gentry, C., Halevi, S., & Vaikuntanathan, V., (2010). Fully homomorphic encryption over the integers. In Proceedings of annual international conference on the theory and applications of cryptographic techniques, (pp. 24–43). https://doi.org/10.1007/978-3-642-13190-5_2
Gentry, C., & Halevi, S., (2011). Implementing Gentry’s Fully-Homomorphic Encryption Scheme, In Proceedings of Annual International Conference on the Theory and Applications of Cryptographic Techniques, (pp 129–148). https://doi.org/10.1007/978-3-642-20465-4_9
Dhote, M. M. P., Dhote, C. A., & Sharma, D. H. (2016). Homomorphic encryption for security of cloud data. In Procedia Computer Science, 79(3), 175–181. https://doi.org/10.1016/j.procs.2016.03.023.
Blanchet, B., (2001). An efficient cryptographic protocol verifier based on prolog rules. In Proceedings of the 14th IEEE computer security foundations workshop, (pp. 82–96).
Blanchet, B., Abadi, M., & Fournet, C. (2008). Automated verification of selected equivalences for security protocols. Journal of Logic and Algebraic Programming, 75(1), 3–51. https://doi.org/10.1016/j.jlap.2007.06.002.
Canetti, R., Goldreich, O., & Halevi, S. (2004). The random oracle methodology, revisited. In Journal of the ACM, 51(4), 557–594. https://doi.org/10.1145/1008731.1008734.
Koblitz, N., & Menezes, A. J. (2015). The random oracle model: A twenty-year retrospective. Designs, Codes and Cryptography, 77(2), 587–610. https://doi.org/10.1007/s10623-015-0094-2.
Dolev, D., & Yao, A. (1983). On the security of public key protocols. IEEE Transactions on Information Theory, 29(2), 198–208. https://doi.org/10.1109/TIT.1983.1056650.
Blanchet, B. (2013). Automatic verification of security protocols in the symbolic model: The verifier proverif. In Foundations of security analysis and design VII, (pp. 54–87). https://doi.org/10.1007/978-3-319-10082-1_3
Viganò, L. (2006). Automated security protocol analysis with the AVISPA tool. Electronic Notes in Theoretical Computer Science, 155, 61–86. https://doi.org/10.1016/j.entcs.2005.11.052.
Meier, S., Schmidt, B., Cremers, C., & Basin, D., (2013). The TAMARIN Prover for the symbolic analysis of security protocols. In Proceedings of international conference on computer aided verification, (pp. 696–701). https://doi.org/10.1007/978-3-642-39799-8_48
Funding
This study was funded by SERB, DST, Govt. of India (Project Grant Number EEQ/2020/000039).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Author Anupam Pattanayak declares that he has no conflict of interest. Author Mou Dutta declares that she has no conflict of interest. Author Subhasish Dhal declares that he has no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Pattanayak, A., Dutta, M. & Dhal, S. Privacy Preserved Medical Service Provider Selection in Cloud-based Wireless Body Area Network. Wireless Pers Commun 128, 1349–1371 (2023). https://doi.org/10.1007/s11277-022-10003-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-10003-w