Abstract
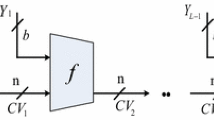
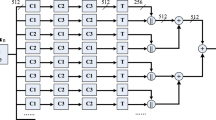
Hash functions serve as a fundamental cryptographic primitives and are used in numerous security fields, such as cloud audit, digital signature, block chain and random number generation. Recent years, cryptographers have long delved into parallel hash functions to design more efficient cryptographic primitives. This paper proposes a multi-iterative parallel hash function. Moreover, inside this parallel structure, a four branch parallel compression structure is proposed to accelerate message diffusion. Simulation results show the proposed hash scheme has great performance on both efficiency and security.












Similar content being viewed by others
Data availability
The data of this study are available from the corresponding author on reasonable request.
Code availability
The code of this study are available from the corresponding author on reasonable request.
References
Boer, B. D., & Bosselaers, A. (1993). Collisions for the compression function of MD5. Eurocrypt, 765, 293–304.
Dobbertin, H. (1996). Cryptanalysis of MD5 compress. Presented at the rump session of Eurocrypt 1996.
Wang, X., Yin, Y., & Yu, H. (2005). Finding collisions in the full SHA-1. Lecture Notes in Computer ScienceIn V. Shoup (Ed.), Advances in cryptology-CRYPTO2005 (Vol. 3621, pp. 17–36). Springer.
Chabaud, F., & Joux, A. (1998). Differential collisions in SHA-0. Crypto, 1462, 56–71.
Chu, C. K., Zhu, W. T., Han, J., Liu, J. K., Xu, J., & Zhou, J. (2013). Security concerns in popular cloud storage services. IEEE Pervasive Computing, 12(4), 50–57.
Merkel, R. C. (1990). One way hash functions and DES. Advances in Cryptology CRYPTO 89, 435, 428–446.
Damgard, I. B. (1990). A design principle for hash functions. Advances in Cryptology CRYPTO 89, 435, 416–427.
Liang, J., & Lai, X. (2005). Improved collision attack on hash function MD5. In: Technical Report.
Sasaki, Y., Naito, Y., Kunihiro, N., & Ohta, K. (2007). Improved collision attacks on MD4 and MD5. IEICE Transactions, 90-A(1), 37–47.
Stevens, M. (2013). New collision attacks on SHA-1 based on optimal joint local-collision analysis. In: Advances in Cryptology-Eurocrypt 2013, Lecture Notes in Computer Science, 7881, 245–261.
Wang, X., Feng, D., Lai, X., & Yu, H. (2004). Collisions for hash functions MD4, MD5, HAVAL-128 and RIPEMD. Cryptology ePrint Archive, Report 2004/199.
Li, W., Gao, Z., & Gu, D. (2017). Security analysis of whirlpool hash function in the cloud of things. KSII Transactions on Internet and Information Systems., 11(1), 536–551.
Mendel, F., Nad, T., & Schlaffer, M. (2013). Improving local collisions: New attacks on reduced SHA-256. Lecture Notes in Computer ScienceIn T. Johansson & P. Nguyen (Eds.), Advances in cryptology-EUROCRYPT2013 (Vol. 7881, pp. 262–278). Springer.
Lee, J., & Hong, D. (2012). Collision resistance of the JH hash function. IEEE Transactions of Information Theory, 58(3), 1992–1995.
Lucks, S. (2005). A failure-friendly design principle for hash functions. Asiacrypt, 3788, 474–494.
Biham, E., & Dunkelman, O. (2007). A framework for iterative hash functions—HAIFA. Cryptology ePrint Archive: Report 2007/278.
Bertoni, G., Daeman, J., & Peeters, M. (2007). Sponge functions. ECRYPT Hash Workshop. http://www.csrc.nist.gov/pki/HashWorkshop/PublicComments/2007May.html
Je, S. T., Azman, S., & Amir, A. (2015). Parallel chaotic hash function based on the shuffle-exchange network. Nonlinear Dynamics, 81, 1067–1079.
Wang, Y., Wong, K. W., & Xiao, D. (2011). Parallel hash function construction based on coupled map lattices. Communications in Nonlinear Science and Numerical Simulation, 16(7), 2810–2821.
Nouri, M., Safarinia, M., & Pourmahdi, P. (2014). The parallel one-way hash function based on Chebyshev-Halley methods with variable parameter. International Journal of Computers Communications & Control, 9(1), 24–36.
Yang, Y., Chen, F., Chen, J., Zhang, Y., & Yung, K. L. (2019). A secure hash function based on feedback iterative structure. Enterprise Information Systems., 13(3), 281–302.
Guesmi, R., Farah, M., & Kachouri, A. (2016). A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dynamics, 83, 1123–1136.
Kanso, A., & Ghebleh, M. (2015). A structure-based chaotic hashing scheme. Nonlinear Dynamics, 81, 27–40.
Ye, G., Zhao, H., & Chai, H. (2016). Chaotic image encryption algorithm using wave-line permutation and block diffusion. Nonlinear Dynamics, 83, 2067–2077.
Salvatore, P., Pedro, R., & Juan, A. M. (2016). Parallel d-pipeline: A Cuckoo hashing implementation for increased throughput. IEEE Transactions on Computers, 65(1), 326–331.
Meysam, A., Shahram, J., & Narjes, N. (2016). A novel keyed parallel hashing scheme based on a new chaotic system. Chaos, Solitions and Fractals, 87, 216–225.
Yang, Y., Chen, F., Sun, Z., Wang, S., & Chen, J. (2019). Secure and efficient parallel hash function construction and its application on cloud audit. Soft Computing, 23(18), 8907–8925.
Gauravaram, P., Millan, W., & Nieto, J. G. (2005). 3C—A provably secure pseudorandom function and message authentication code. A new mode of operation for cryptographic hash function. Annals of the New York Academy of Sciences, 2005(1), 491–494.
Liskov, M. (2006). Constructing an ideal hash function from weak ideal compression functions. In The proceedings of the 13th international conference on selected areas in cryptography. Montreal, Canada. Springer-Verlag, 2006 (pp. 358–375).
Yang, Y., & Chen, F. (2017). Research on the hash function structures and its application. Wireless Personal Communications, 94(4), 2969–2985.
Funding
This work was supported by Shenzhen Polytechnic Youth Innovation Project under Grant 6019310007K0, 6021310008K, Guangdong Rural Science and Technology Commissioner Project under Grant No. KTP20200226, Science and Technology Innovation Projects of Shenzhen under Grant Nos. JCYJ20210324100813034, JCYJ20190809152003992, and the National Natural Science Foundation of China under Grant 62102268.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yang, Y., Zhang, X. A Novel Hash Function Based on Multi-iterative Parallel Structure. Wireless Pers Commun 127, 2979–2996 (2022). https://doi.org/10.1007/s11277-022-09906-5
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09906-5