Abstract
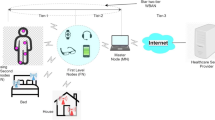
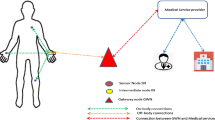
Internet of Things (IoT) is a revolution which has influenced the lifestyle of human. Wireless Body Area Networks (WBAN)s are IoT-based applications which have a crucial role in the current healthcare systems. A WBAN is used to collect some health-related information of patients and transport and monitor them in a healthcare system. This information is crucial in the sense of the patient’s life. Then the privacy of the patient and the security of his/her information are some main challenges in the WBAN. Another challenge in the WBAN is the resources limitation of the sensor nodes. This limitation imposes that a suitable scheme for the WBAN should be a lightweight one. In order to response these challenges, several lightweight Authentication and Key Agreement (AKA) schemes have been presented for WBAN so far. However, approximately none of them could reach their security and cost goals. In 2020, Narwal and Mohapatra proposed a claimed to be secure lightweight AKA protocol for WBAN named SEEMAKA. In this paper, we show that this scheme suffers from attacks including sensor node traceability, disclosure of the secret parameters of the sensor nodes and master nodes, sensor node impersonation, extracting the session key, and Denial of Service attacks. Besides that, we focus to overcome these vulnerabilities and present an improved version of SEEMAKA named ISAKA. ISAKA improves the security level and also the efficiency level of SEEMAKA. More precisely, ISAKA is safe against mentioned attacks and it improves ROM and RAM storage requirements and also computational and communication costs. We prove the security of ISAKA using two formal methods, i.e. BAN logic method and ProVerif tool.




Similar content being viewed by others
Data Availibility
Data sharing is not applicable to this article as no datasets were generated or analyzed during the current study.
References
Agha, D.-e.-S., Khan, F. H., Shams, R., Rizvi, H. H., & Qazi, F. (2018). A secure crypto base authentication and communication suite in wireless body area network (WBAN) for IoT applications. Wireless Personal Communications, 103(4):2877–2890, 2018
Alzahrani, B. A. (2021). Secure and efficient cloud-based IoT authenticated key agreement scheme for e-health wireless sensor networks. Arabian Journal for Science and Engineering, 46(4), 3017–3032.
Alzahrani, B.A., Irshad, A., Albeshri, A., & Alsubhi, K. (2020). A provably secure and lightweight patient-healthcare authentication protocol in wireless body area networks. Wireless Personal Communications, pp. 1–23
Amin, R., & Biswas, G. (2015). An improved RSA based user authentication and session key agreement protocol usable in TMIS. Journal of Medical Systems, 39(8), 79.
Arshad, H., & Rasoolzadegan, A. (2016). Design of a secure authentication and key agreement scheme preserving user privacy usable in telecare medicine information systems. Journal of Medical Systems, 40(11), 237.
Blanchet B. (2012). Proverif: automatic cryptographic protocol verifier user manual for untyped inputs
Burrows, M., Abadi, M., & Needham, R.M. (1871). A logic of authentication. Proceedings of the Royal Society of London. A. Mathematical and Physical Sciences, 426(1871):233–271
Fotouhi, M., Bayat, M., Das, A.K., Far, H.A.N., Pournaghi, S.M., & Doostari, M. (2020). A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT. Computer Networks, pp. 107333
Giri, D., Maitra, T., Amin, R., & Srivastava, P. (2015). An efficient and robust RSA-based remote user authentication for telecare medical information systems. Journal of Medical Systems, 39(1), 145.
Hussain, S. J., Irfan, M., Jhanjhi, N., Hussain, K., & Humayun, M. (2021). Performance enhancement in wireless body area networks with secure communication. Wireless Personal Communications, 116(1), 1–22.
Ibrahim, M. H., Kumari, S., Das, A. K., Wazid, M., & Odelu, V. (2016). Secure anonymous mutual authentication for star two-tier wireless body area networks. Computer Methods and Programs in Biomedicine, 135, 37–50.
I. B. Karthigaiveni M. An efficient two-factor authentication scheme with key agreement for iot based e-health care application using smart card. Journal of Ambient Intelligence and Humanized Computing, 2019
Li, X., Ibrahim, M. H., Kumari, S., & Kumar, R. (2018). Secure and efficient anonymous authentication scheme for three-tier mobile healthcare systems with wearable sensors. Telecommunication Systems, 67(2), 323–348.
Li, X., Ibrahim, M. H., Kumari, S., Sangaiah, A. K., Gupta, V., & Choo, K.-K.R. (2017). Anonymous mutual authentication and key agreement scheme for wearable sensors in wireless body area networks. Computer Networks, 129, 429–443.
Narwal, B. & Mohapatra, A.K. (2020) SEEMAKA: secured energy-efficient mutual authentication and key agreement scheme for wireless body area networks. Wireless Personal Communications, pp. 1–24, 2020
Narwal, B., & Mohapatra, A. K. (2021). Samaka: Secure and anonymous mutual authentication and key agreement scheme for wireless body area networks. Arabian Journal for Science and Engineering, 46(9), 9197–9219.
Nikooghadam, M., & Amintoosi, H. (2020). An improved secure authentication and key agreement scheme for healthcare applications. In 2020 25th International Computer Conference, Computer Society of Iran (CSICC), pp. 1–7. IEEE
Ostad-Sharif, A., Abbasinezhad-Mood, D., & Nikooghadam, M. (2019). An enhanced anonymous and unlinkable user authentication and key agreement protocol for TMIS by utilization of ECC. International Journal of Communication Systems, 32(5), e3913.
Ostad-Sharif, A., Nikooghadam, M., & Abbasinezhad-Mood, D. (2019). Design of a lightweight and anonymous authenticated key agreement protocol for wireless body area networks. International Journal of Communication Systems, 32(12), e3974.
Shaik, M. F., Komanapalli, V. L. N., & Subashini, M. M. (2018). A comparative study of interference and mitigation techniques in wireless body area networks. Wireless Personal Communications, 98(2), 2333–2365.
Soni, M., & Singh, D. K. (2021) Laka: lightweight authentication and key agreement protocol for internet of things based wireless body area network. Wireless Personal Communications, pp. 1–18
Xu, Z., Xu, C., Chen, H., & Yang, F. (2019). A lightweight anonymous mutual authentication and key agreement scheme for WBAN. Concurrency and Computation: Practice and Experience, 31(14), e5295.
Zimmerman, T. G. (1996). Personal area networks: Near-field intrabody communication. IBM systems Journal, 35(3.4):609–617
Funding
This work was supported by Shahid Rajaee Teacher Training University.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that they have no conflict of interest.
Ethical Approval
This manuscript does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Alizadeh, J., Safkhani, M. & Allahdadi, A. ISAKA: Improved Secure Authentication and Key Agreement protocol for WBAN. Wireless Pers Commun 126, 2911–2935 (2022). https://doi.org/10.1007/s11277-022-09844-2
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09844-2