Abstract
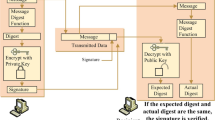
Fuzzy identity based signature (FIBS) possesses error-tolerance property which allows a user with identity ID described as an attribute set \(\omega =\{\omega _i\}_{i=1}^{n}\) to issue a signature that could be verifed with identity \(ID^{'}\) described as an attribute set \(\omega ^{'}=\{\omega _i^{'}\}_{i=1}^{n}\) if and only if \(\omega\) and \(\omega ^{'}\) are within a certain distance. Most FIBS schemes’security proofs are given in the random oracle model (ROM). Although in random oracle model the cryptographic scheme is proved to be secure, in practical applications it may be insecure. In this paper, we construct a concrete FIBS scheme and its security proof is given in the standard model(SM). Finally, we compare the proposed scheme with several other signature schemes in terms of computation, communication and security model and show that the proposed scheme is more efficient and suitable for practical applications.


Similar content being viewed by others
Change history
26 March 2022
The original online version of this article was revised: Modifications have been made to several formulas. Full information regarding the corrections made can be found in the Correction for this article. The original article has been corrected.
24 March 2022
A Correction to this paper has been published: https://doi.org/10.1007/s11277-022-09660-8
References
Shamir, A. (1985). Identity-based cryptosystem and signature scheme. In Advances in Cryptology-Proceedings of CRYPTO’84. LNCS, vol. 0196. Springer-Verlag, Berlin, (pp. 47–53).
Sahai, A., & Waters, B. (2005). Fuzzy identity-based encryption. In Advances in Cryptology-In Eurocrypt 2005. LNCS 3494. Springer-Verlag, (pp. 457–473).
Yang, P., Cao, Z., & Dong, X. (2008). Fuzzy identity based signature. Cryptology ePrint Archive. Report 2008/002.
Wang, C., & Kim, J.H. (2009). Two constructions of fuzzy identity based signature. In 2nd International Conference on Biomedical Engineering and Informatics, 2009. BMEI09. Tianjin, China, (pp. 1–5).
Wang, C., Chen, W., & Liu, Y. (2009). A fuzzy identity based signature scheme. In International Conference on E-Business and Information System Security, 2009. EBISS09. Wuhan, China, (pp. 554–558).
Chen, W., Zhu, L., Li, Cao, X., & Geng, Y. (2009). A Novel Fuzzy Identity-based Signature with Dynamic Threshold. In 3rd International Conference on Network and System Security. IEEE Computer Society, (pp. 192–198).
Zhang, L., Wu, Q., & Hu, Y. (2011). Fuzzy biometric identity-based signature in the standard model. In Applied Mechanics and Materials, vol. 44. Trans Tech Publ: Switzerland, (pp. 3350–3354).
Yang, P., Cao, Z., & Dong, X. (2011). Fuzzy identity based signature with applications to biometric authentication. Computers and Electrical Engineering, 37(2), 532–540.
Wang, C. (2012). A provable secure fuzzy identity based signature scheme. Science China Information Sciences, 55(9), 2139–2148.
Yang, Y., Hu, Y., & Zhang, L. (2013). An efficient biometric identity based signature scheme. KSII Transactions on Internet and Information Systems, 7(8), 2010–2026.
Xiong, H., Chen, Y., Zhu, G., & Qin, Z. (2014). Analysis and improvement of a provable secure fuzzy identity-based signature scheme. Science China Information Sciences, 57(9), 1–5.
Wang, C. (2014). An Efficient Fuzzy Identity-Based Signature Scheme without Bilinear Pairings. In Tenth International Conference on Computational Intelligence and Security. IEEE Computer Society.
Yang, C., Zheng, S., Wang, L., Tian, M., Gu, L., & Yang, Y. (2014). A fuzzy identity-based signature scheme from lattices in the standard model. Mathematical Problems in Engineering, 2014.
Yao, Y., & Li, Z. (2014). A novel fuzzy identity based signature scheme based on the short integer solution problem. Computers and Electrical Engineering, 40(6), 1930–1939.
Islam, S. H., Das, A. K., & Khan, M. K. (2016). Design of a provably secure identity-based digital multi-signature scheme using biometrics and fuzzy extractor. Security and Communication Networks, 9(16), 3229–3238.
Zhang, Y., Hu, Y., Gan, Y., Yin, Y., & Jia, H. (2019). Efficient fuzzy identity-based signature from lattices for identities in a small (or large) universe. Journal of Information Security and Applications, 47, 86–93.
Shan, X., You, L., & HU, G. (2021). Two efficient constructions for biometric-based signature in identity-based setting using bilinear pairings. IEEE Access, 9, 25973–25983.
Wang, L., Lai, J., Xiong, H., et al. (2016). Fuzzy certificateless signature. Security and Communication Networks, 9(16), 3658–3669.
Shamir, A. (1979). How to share a secret. Communications of the ACM, 22(11), 612–613.
He, D., Zeadally, S., Kumar, N., & Wu, W. (2016). Efficient and anonymous mobile user authentication protocol using self-certifed public key cryptography for multi-server architectures. IEEE Transactions on Information Forensics and Security, 11(9), 2052–2064.
Acknowledgements
This research was supported by Guizhou Provincial Science and Technology Foundation (Grant No.QIANKEHEJICHU[2019]1221) and the National Natural Science Foundation of China (Grant No.11261060).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Qu, Y., Zeng, J. Fuzzy Identity-Based Signature in Standard Model. Wireless Pers Commun 125, 87–98 (2022). https://doi.org/10.1007/s11277-022-09542-z
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09542-z