Abstract
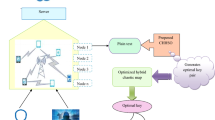
Mobile ad-hoc networks (MANETs) play an important role in the future of the industrial internet-of-things communication, where smart devices will be connected in a completely distributed manner. In the digital properties owing to the digital data properties, there exist difficulties in directly applying the encryption schemes to the one-dimension data. Thus, it is necessary to develop secure lightweight key frame extraction technique for improving privacy in the e-healthcare. This paper plans to develop the robust and reliable security protocol in MANET IoT application. A chaotic cryptography-based privacy preservation model is proposed in this paper for the purpose of improving the security in the MANET IoT. The key generation process in the chaotic map is optimized by generating optimal key pairs through the newly developed SA-SFO algorithm. The key selected from the chaotic map is influenced by selecting the optimal parameters through the proposed Self Adaptive Sail fish Optimization (SA-SFO). Finally, the experimental analysis is conducted, where for the case of character length as 100; the proposed SA-SFO eventually surpassed the existing ones with the cost function 22% as higher than PSO, 20% higher than GWO, 19% higher than WOA, and 21% higher than SFO respectively. The comparative analysis over the conventional models ensures the efficient performance of the proposed model in terms of diverse analysis in MANET and IoT platform.









Similar content being viewed by others
References
Khan, B. U. I., Anwar, F., Olanrewaju, R. F., Pampori, B. R., & Mir, R. N. (2020). A game theory-based strategic approach to ensure reliable data transmission with optimized network operations in futuristic mobile adhoc networks. IEEE Access, 8, 124097–124109.
Govindan, K., & Mohapatra, P. (2012). Trust computations and trust dynamics in mobile adhoc networks: A survey. IEEE Communications Surveys & Tutorials, 14(2), 279–298.
Ping, Y., Futai, Z., Xinghao, J., & Jianhua, L. (2007). Multi-agent cooperative intrusion response in mobile adhoc networks. Journal of Systems Engineering and Electronics, 18(4), 785–794.
Ojetunde, B., Shibata, N., & Gao, J. (2019). Secure payment system utilizing MANET for disaster areas. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 49(12), 2651–2663.
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A vision, architectural elements, and future directions. Future Generation Computer Systems, 29(7), 1645–1660.
Iftikhar, Z., Javed, Y., Zaidi, S. Y. A., Shah, M. A., Khan, I., Mussadiq, Z. S., & Abbasi, K. (2021). Privacy preservation in resource-constrained IoT devices using blockchain—A survey. Electronics, 10, 14.
Shende, K., & Sonavane, S. S. (2020). CrowWhale-ETR: CrowWhale optimization algorithm for energy and trust aware multicast routing in WSN for IoT applications. Wireless Networks, 66, 1–19s.
Alharthi, A., Ni, Q., & Jiang, R. (2021). A privacy-preservation framework based on biometrics blockchain (BBC) to prevent attacks in VANET. IEEE Access, 6, 66.
Al-Turjman, F., Zahmatkesh, H., & Shahroze, R. (2019). An overview of security and privacy in smart cities’ IoT communications. Transactions on Emerging Telecommunications Technologies, 66, e3677.
Atzori, L., Iera, A., & Morabito, G. (2010). The Internet of Things: A survey. Computer Networks, 54(15), 2787–2805.
Guan, Z., Li, J., Wu, L., Zhang, Y., Wu, J., & Du, X. (2017). Achieving efficient and secure data acquisition for cloud-supported Internet of Things in smart grid. IEEE Internet of Things Journal, 4(6), 1934–1944.
Wang, C., Shen, J., Liu, Q., Ren, Y., & Li, T. (2018). A novel security scheme based on instant encrypted transmission for Internet of Things. Security and Communication Networks, 6, 66.
Appavoo, P., Chan, M., Bhojan, A., et al. (2016). Efficient and privacy-preserving access to sensor data for Internet of Things (IoT) based services. IEEE International Conference on Communication Systems and Networks, 66, 1–8.
Henze, M., Hermerschmidt, L., Kerpen, D., et al. (2016). A comprehensive approach to privacy in the cloud-based Internet of Things. Future Generation Computer Systems, 56, 701–718.
González-Manzano, L., de Fuentes, J., Pastrana, S., et al. (2016). PAgIoT-Privacy-preserving aggregation protocol for Internet of Things. Journal of Network and Computer Applications, 71, 59–71.
Lai, C., Li, H., Liang, X., et al. (2014). CPAL: A conditional privacy-preserving authentication with access linkability for roaming service. IEEE Internet of Things Journal, 1(1), 46–57.
Premnath, S., & Haas, Z. (2015). Security and privacy in the internet-of-things under time-and-budget-limited adversary mode. IEEE Wireless Communications Letters, 4(3), 277–280.
Maram, B., Gnanasekar, J. M., Manogaran, G., & Balaanand, M. (2018). Intelligent security algorithm for UNICODE data privacy and security in IOT. Service Oriented Computing and Applications, 6, 66.
George, G., & Thampi, S. M. (2018). A graph-based security framework for securing industrial IoT networks from vulnerability exploitations. IEEE Access, 6, 43586–43601.
Aman, M. N., Basheer, M. H., & Sikdar, B. (2019). Data provenance for IoT with light weight authentication and privacy preservation. IEEE Internet of Things Journal, 6(6), 10441–10457.
Kounoudes, A. D., & Kapitsaki, G. M. (2020). A mapping of IoT user-centric privacy preserving approaches to the GDPR. Internet of Things, 11, 66.
Guan, Z., Zhang, Y., Wu, L., Wu, J., Li, J., Ma, Y., & Hu, J. (2019). APPA: An anonymous and privacy preserving data aggregation scheme for fogenhanced IoT. Journal of Network and Computer Applications, 125, 82–92.
Sun, G., Chang, V., Ramachandran, M., Sun, Z., Li, G., Yu, H., & Liao, D. (2017). Efficient location privacy algorithm for Internet of Things (IoT) services and applications. Journal of Network and Computer Applications, 89, 3–13.
Hamza, R., Yan, Z., Muhammad, K., Bellavista, P., & Titouna, F. (2020). A privacy-preserving cryptosystem for IoT E-healthcare. Information Sciences, 527, 493–510.
Deebak, B. D., Al-Turjman, F., Aloqaily, M., & Alfandi, O. (2019). An authentic-based privacy preservation protocol for smart e-Healthcare systems in IoT. IEEE Access, 7, 135632–135649.
Yu, M., Zhou, M., & Su, W. (2009). A secure routing protocol against byzantine attacks for MANETs in adversarial environments. IEEE Transactions on Vehicular Technology, 58(1), 449–460.
Defrawy, K. E., & Tsudik, G. (2011). Privacy-preserving location-based on-demand routing in MANETs. IEEE Journal on Selected Areas in Communications, 29(10), 1926–1934.
Hurley-Smith, D., Wetherall, J., & Adekunle, A. (2017). SUPERMAN: Security using pre-existing routing for mobile ad hoc networks. IEEE Transactions on Mobile Computing, 16(10), 2927–2940.
Dhurandher, S. K., Obaidat, M. S., Verma, K., Gupta, P., & Dhurandher, P. (2011). FACES: Friend-based ad hoc routing using challenges to establish security in MANETs systems. IEEE Systems Journal, 5(2), 176–188.
Li, T., Chen, W., Tang, Y., & Yan, H. (2018). A homomorphic network coding signature scheme for multiple sources and its application in IoT. Security and Communication Networks, 6, 66.
Challa, S., Wazid, M., Das, A. K., Kumar, N., Reddy, A. G., Yoon, E. J., & Yoo, K. Y. (2017). Secure signature-based authenticated key establishment scheme for future IoT applications. IEEE Access, 5, 3028–3043.
Gomes, G. F., da Cunha, S. S., Jr., & Ancelotti, A. C., Jr. (2019). A sunflower optimization (SFO) algorithm applied to damage identification on laminated composite plates. Engineering with Computers, 35, 619–626.
Shadravan, S., Naji, H. R., & Bardsiri, V. K. (2019). The sailfish optimizer: A novel nature-inspired metaheuristic algorithm for solving constrained engineering optimization problems. Engineering Applications of Artificial Intelligence, 80, 20–34.
Pedersen, M. E. H., & Chipperfield, A. J. (2010). Simplifying particle swarm optimization. Applied Soft Computing, 10(2), 618–628.
Mirjalili, S., Mirjalili, S. M., & Lewis, A. (2014). Grey wolf optimizer. Advances in Engineering Software, 69, 46–61.
Mirjalili, S., & Lewis, A. (2016). The whale optimization algorithm. Advances in Engineering Software, 95, 51–67.
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
Satyanarayana Pamarthi and Narmadha Ramakrishnan designed the model and computational framework. Both carried out the implementation. Satyanarayana Pamarthi performed the calculations and wrote the manuscript with all the inputs. Satyanarayana Pamarthi and Narmadha Ramakrishnan discussed the results and contributed to the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Pamarthi, S., Narmadha, R. Adaptive Key Management-Based Cryptographic Algorithm for Privacy Preservation in Wireless Mobile Adhoc Networks for IoT Applications. Wireless Pers Commun 124, 349–376 (2022). https://doi.org/10.1007/s11277-021-09360-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-09360-9