Abstract
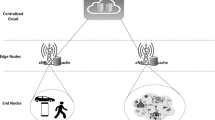
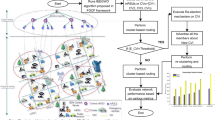
The fifth generation (5G) network technology has made it possible to further exploit the radio spectrum and allow a large number of devices to concurrently have access to the mobile internet. The network has become a viable option for creating such connections and providing Internet of Things (IoT) services in a fast, secure and reliable way. In micro cloud computing, Edge computing refers to a term that describes the edge computing technology. It is expected that the IoT would utilize edge computing to minimize offloading tasks and latency as well as use the computing power in the offloading process. Although edge computing is an old technology, its role in facilitating the real-time transfer of data from devices to the cloud and the real-time processing of data within the devices has only been realized in recent times. In the process of offloading data and computing tasks, the data flow may be interrupted. The 5G technology can provide a better solution to help IoT applications close the gap between edge and the limited device resources, thus making it more reliable. This paper employs the Bald eagle search (BES) algorithm, particle swarm optimization algorithm, and genetic algorithm to simulate the edge computing. The goal is to determine which of the algorithms has the best performance, based on their latency and offloading capacity, in edge computing by comparing their results. On the basis of the execution time, amount of resources utilized in offloading tasks, and total cost of vehicular edge, the three algorithms are compared and validated. According to the simulation results, the best-performing method is the BES algorithm, as it gives the IoT quick access to information.















Similar content being viewed by others
Availability of data and materials
Data and coding will be shared whenever it is required for the review.
References
Satyanarayanan, M. (2017). The emergence of edge computing. Computer, 50(1), 30–39.
Porambage, P., et al. (2018). Survey on multi-access edge computing for internet of things realization. IEEE Communications Surveys and Tutorials, 20(4), 2961–2991.
McGilvary, G.A., Barker, A., & Atkinson, M. (2015). Ad hoc cloud computing. In 2015 IEEE 8th international conference on cloud computing. IEEE.
Balasubramanian, V. & Karmouch, A. (2017). An infrastructure as a service for mobile ad-hoc cloud. In 2017 IEEE 7th annual computing and communication workshop and conference (CCWC). IEEE.
Safavat, S., Sapavath, N. N., & Rawat, D. B. (2020). Recent advances in mobile edge computing and content caching. Digital Communications and Networks, 6(2), 189–194.
Deng, D., et al. (2020). Link selection in buffer-aided cooperative networks for green IoT. IEEE Access, 8, 30763–30771.
Chen, L., et al. (2020). Multi-antenna processing based cache-aided relaying networks for B5G communications. Physical Communicatio.
Cao, B., et al. (2019). Intelligent offloading in multi-access edge computing: A state-of-the-art review and framework. IEEE Communications Magazine, 57(3), 56–62.
Xu, X., et al. (2020). Edge server quantification and placement for offloading social media services in industrial cognitive IoV. In IEEE transactions on industrial informatics.
Wan, S., et al. (2019). Multi-dimensional data indexing and range query processing via Voronoi diagram for internet of things. Future Generation Computer Systems, 91, 382–391.
Ferrer, A. J., Marquès, J. M., & Jorba, J. (2019). Towards the decentralised cloud: Survey on approaches and challenges for mobile, ad hoc, and edge computing. ACM Computing Surveys (CSUR), 51(6), 1–36.
Gai, K., et al. (2019). Permissioned blockchain and edge computing empowered privacy-preserving smart grid networks. IEEE Internet of Things Journal, 6(5), 7992–8004.
Arif, S., et al. (2012). Datacenter at the airport: Reasoning about time-dependent parking lot occupancy. IEEE Transactions on Parallel and Distributed Systems, 23(11), 2067–2080.
Deng, S., et al. (2020). Optimal application deployment in resource constrained distributed edges. IEEE transactions on mobile computing.
Khan, W. Z., et al. (2019). Edge computing: A survey. Future Generation Computer Systems, 97, 219–235.
Shi, F., et al. (2019). Secure probabilistic caching in random multi-user multi-UAV relay networks. Physical Communication, 32, 31–40.
Fan, L., et al. (2018). Outage probability and optimal cache placement for multiple amplify-and-forward relay networks. IEEE Transactions on Vehicular Technology, 67(12), 12373–12378.
Patra, S.S., Goswami, V., & Mund, G. (2020). Performance evaluation of cloud systems by switching the virtual machines power mode between the sleep mode and active mode. In Handbook of research on developments and trends in industrial and materials engineering (pp. 145–168). IGI Global.
Evans, D. (2011). The internet of things: How the next evolution of the internet is changing everything. CISCO white paper, 2011(1), 1–11.
Mao, Y., Zhang, J.., & Letaief, K.B. (2017) Joint task offloading scheduling and transmit power allocation for mobile-edge computing systems. In 2017 IEEE wireless communications and networking conference (WCNC). IEEE.
Xiao, S., et al. (2020). System delay optimization for Mobile Edge Computing. Future Generation Computer Systems, 109, 17–28.
Chen, M., & Hao, Y. (2018). Task offloading for mobile edge computing in software defined ultra-dense network. IEEE Journal on Selected Areas in Communications, 36(3), 587–597.
Ding, Z., Fan, P., & Poor, H. V. (2018). Impact of non-orthogonal multiple access on the offloading of mobile edge computing. IEEE Transactions on Communications, 67(1), 375–390.
Wang, Y., et al. (2019). Cooperative task offloading in three-tier mobile computing networks: An ADMM framework. IEEE Transactions on Vehicular Technology, 68(3), 2763–2776.
Mukherjee, M., Shu, L., & Wang, D. (2018). Survey of fog computing: Fundamental, network applications, and research challenges. IEEE Communications Surveys & Tutorials, 20(3), 1826–1857.
Mao, Y., Zhang, J., & Letaief, K. B. (2016). Dynamic computation offloading for mobile-edge computing with energy harvesting devices. IEEE Journal on Selected Areas in Communications, 34(12), 3590–3605.
Kuang, Z., et al. (2019). Partial offloading scheduling and power allocation for mobile edge computing systems. IEEE Internet of Things Journal, 6(4), 6774–6785.
Huang, B., et al. (2019). Security modeling and efficient computation offloading for service workflow in mobile edge computing. Future Generation Computer Systems, 97, 755–774.
Qin, M., et al. (2018). Power-constrained edge computing with maximum processing capacity for IoT networks. IEEE Internet of Things Journal, 6(3), 4330–4343.
Li, L., Kuang, Z., & Liu, A. (2019). Energy efficient and low delay partial offloading scheduling and power allocation for MEC. In ICC 2019–2019 IEEE international conference on communications (ICC). IEEE.
Masood, M., et al. (2019). An improved particle swarm algorithm for multi-objectives based optimization in MPLS/GMPLS networks. IEEE Access, 7, 137147–137162.
Mseddi, A., et al. (2019). Joint container placement and task provisioning in dynamic fog computing. IEEE Internet of Things Journal, 6(6), 10028–10040.
Xu, X., et al. (2019). Dynamic resource provisioning with fault tolerance for data-intensive meteorological workflows in cloud. IEEE Transactions on Industrial Informatics, 16(9), 6172–6181.
Ndikumana, A., et al. (2019). Joint communication, computation, caching, and control in big data multi-access edge computing. IEEE Transactions on Mobile Computing.
Nguyen, T.-D., Huh, E.-N., & Jo, M. (2018). Decentralized and revised content-centric networking-based service deployment and discovery platform in mobile edge computing for IoT devices. IEEE Internet of Things Journal, 6(3), 4162–4175.
Bastug, E., Bennis, M., & Debbah, M. (2014). Living on the edge: The role of proactive caching in 5G wireless networks. IEEE Communications Magazine, 52(8), 82–89.
Xiao, K., et al. (2020). EdgeABC: An architecture for task offloading and resource allocation in the Internet of Things. Future Generation Computer Systems, 107, 498–508.
Jiacheng, C. et al. (2016). Software defined internet of vehicles: Architecture, challenges and solutions.
Balasubramanian, V., et al. (2020). Low-latency vehicular edge: A vehicular infrastructure model for 5G. Simulation Modelling Practice and Theory. 98.
Dinh, H. T., et al. (2013). A survey of mobile cloud computing: Architecture, applications, and approaches. Wireless communications and mobile computing, 13(18), 1587–1611.
Tao, X., et al. (2017). Performance guaranteed computation offloading for mobile-edge cloud computing. IEEE Wireless Communications Letters, 6(6), 774–777.
Bista, B.B., Wang, J., & Takata, T. (2020). Probabilistic computation offloading for mobile edge computing in dynamic network environment. Internet of Things (p. 100225).
Elgendy, I. A., et al. (2020). Efficient and secure multi-user multi-task computation offloading for mobile-edge computing in mobile IoT networks. IEEE Transactions on Network and Service Management, 17(4), 2410–2422.
Zhang, L., et al. (2021). Efficient cross-correlation algorithm for correction of common phase error employing preamble for orthogonal frequency division multiplexing (OFDM) receivers. Wireless Personal Communications (pp. 1–15).
Qu, Y., et al. (2020). Robust offloading scheduling for mobile edge computing. IEEE Transactions on Mobile Computing.
Vaquero, L. M., & Rodero-Merino, L. (2014). Finding your way in the fog: Towards a comprehensive definition of fog computing. ACM SIGCOMM Computer Communication Review, 44(5), 27–32.
Li, Y., et al. (2017). Leveraging renewable energy in edge clouds for data stream analysis in iot. In 2017 17th IEEE/ACM international symposium on cluster, cloud and grid computing (CCGRID). IEEE.
Xu, D., & Li, Q. (2017). Price-based time and energy allocation in cognitive radio multiple access networks with energy harvesting. Science China Information Sciences, 60(10), 108302.
Lu, N., et al. (2014). Connected vehicles: Solutions and challenges. IEEE internet of things journal, 1(4), 289–299.
Aloqaily, M., et al. (2018). Congestion mitigation in densely crowded environments for augmenting qos in vehicular clouds. In Proceedings of the 8th ACM symposium on design and analysis of intelligent vehicular networks and applications.
Computing, F., (2015). The internet of things: Extend the cloud to where the things are. Cisco White Paper.
Wang, X., et al. (2019). A tensor-based big-data-driven routing recommendation approach for heterogeneous networks. IEEE Network, 33(1), 64–69.
Xu, X., et al. (2019). An edge computing-enabled computation offloading method with privacy preservation for internet of connected vehicles. Future Generation Computer Systems, 96, 89–100.
Liu, Q., et al. (2020). Multi-objective resource allocation in mobile edge computing using PAES for Internet of Things. Wireless networks (pp. 1–13).
Shi, W., et al. (2016). Edge computing: Vision and challenges. IEEE internet of things journal, 3(5), 637–646.
Mach, P., & Becvar, Z. (2017). Mobile edge computing: A survey on architecture and computation offloading. IEEE Communications Surveys & Tutorials, 19(3), 1628–1656.
Tao, Z., et al. (2019). A survey of virtual machine management in edge computing. Proceedings of the IEEE, 107(8), 1482–1499.
Kotb, Y., et al. (2019). Cloud-based multi-agent cooperation for IoT devices using workflow-nets. Journal of Grid Computing, 17(4), 625–650.
Baker, T., Aldawsari, B., & England, D. (2015). Trusted energy-efficient cloud-based services brokerage platform. International Journal of Intelligent Computing Research (IJICR), 6(4), 630–639.
Stergiou, C. L., Psannis, K. E., & Gupta, B. B. (2021). IoT-based Big Data secure management in the Fog over a 6G Wireless Network. IEEE Internet of Things Journal, 8(7), 1.
Tewari, A., & Gupta, B. B. (2017). Cryptanalysis of a novel ultra-lightweight mutual authentication protocol for IoT devices using RFID tags. The Journal of Supercomputing, 73, 1085–1102.
Gupta, B. B., & Quamara, M. (2018). An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurrency and Computation: Practice and Experience., 32, e4946.
Esposito, C., Ficco, M., & Gupta, B. B. (2021). Blockchain-based authentication and authorization for smart city applications. Information Processing and Management, 58.
Li, D., Deng, L., Gupta, B. B., Wang, H., & Choi, C. (2019). A novel CNN based security guaranteed image watermarking generation scenario for smart city applications. Information Sciences, 479, 432–447.
Fantacci, R., & Picano, B. (2020). Federated learning framework for mobile edge computing networks. CAAI Transactions on Intelligence Technology, 5(1), 15–21.
Tewari, A., & Gupta, B. B. (2020). Security, privacy and trust of different layers in Internet-of-Things (IoTs) framework. Future Generation Computer Systems, 108, 909–920.
Acknowledgements
I/We declare that “it is not been submitted anywhere before as well as not been published in other journals”. It contains no matter that is scandalous, obscene, fraud, plagiarism, libellous, or otherwise contrary to law. I/we followed the Journal’s adopted “Publication ethics and malpractice” statement which given in journal’s website in about section and we will be answerable for the correctness (or plagiarism) and authenticity of article.
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
Both the authors are equally contributed their skills and effort to produce this article.
Corresponding author
Ethics declarations
Conflict of interest
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Almashhadani, H.A., Deng, X., Abdul Latif, S.N. et al. An Edge-Computing Based Task-Unloading Technique with Privacy Protection for Internet of Connected Vehicles. Wireless Pers Commun 127, 1787–1808 (2022). https://doi.org/10.1007/s11277-021-08723-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08723-6