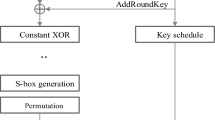
Abstract
The Internet of Things is an emerging area which deals with transfer of the data through the wired or wireless network. The prime thing that needs to be addressed in this is the security of the data that must be transferred within the optimized time limit. In this paper, throughput and time delay are need to be considered for the optimized data transfer and while concentrating on this, there is a possibility of allowing the data to be vulnerable to attacks. Security algorithms currently available may be adequate for the wired system and not as the same for wireless scenario. PRESENT cipher is a one of the popular cryptosystem used in wireless which falls under the light weight cryptography category. Gift cipher is an enhanced version of PRESENT cipher. Which aims that maximizing the throughput. In this, iteration structure used for encryption. This can still be improved and optimized in terms of increased data rate and reduced time delay. In this paper, implements the optimization technique of the existing GIFT cipher and throughput is considered as the performance metrics. Pipeline and sub-stage pipeline techniques are used for enhancing the architecture.








Similar content being viewed by others
References
Adomnicai, A., Najm, Z., & Peyrin, T. (2020). Fixslicing: A new GIFT representation. IACR Cryptol. ePrint Arch., 2020, 412.
Banik, S., Pandey, S. K., Peyrin, T., Sasaki, Y., Sim, S. M., & Todo, Y. (2017). GIFT: A small present towards reaching the limit of lightweight encryption (Full version). Technical Report.
Banik, S., Chakraborti, A., Iwata, T., Minematsu, K., Nandi, M., Peyrin, T., Sasaki, Y,. Sim, S. M., & Todo, Y. (2019). GIFT-COFB. Submission to Round.
Chodowiec, P., & Gaj, K. (2003). Very compact FPGA implementation of the AES algorithm. In International workshop on cryptographic hardware and embedded systems (pp. 319–333). Springer, Berlin, Heidelberg.
Dalmasso, L., Bruguier, F., Benoit, P., & Torres, L. (2019). Evaluation of SPN-based lightweight crypto-ciphers. IEEE Access, 14(7), 10559–10567.
Granado-Criado, J. M., Vega-Rodríguez, M. A., Sánchez-Pérez, J. M., & Gómez-Pulido, J. A. (2010). A new methodology to implement the AES algorithm using partial and dynamic reconfiguration. Integration, 43(1), 72–80.
Hodjat, A., & Verbauwhede, I. (2006). Area-throughput trade-offs for fully pipelined 30 to 70 Gbits/s AES processors. IEEE Transactions on Computers, 55(4), 366–372.
Lara-Nino, C. A., Diaz-Perez, A., & Morales-Sandoval, M. (2018) FPGA-based assessment of midori and gift lightweight block ciphers. In International conference on information and communications security (pp. 745–755). Springer, Cham.
Rani, D. J., & Roslin, S. E. (2016). Light weight cryptographic algorithms for medical internet of things (IoT)—A review. In 2016 Online international conference on green engineering and technologies (IC-GET) (pp. 1–6).
Rahimunnisa, K., Karthigaikumar, P., Rasheed, S., Jayakumar, J., & Suresh Kumar, S. (2014). FPGA implementation of AES algorithm for high throughput using folded parallel architecture. Security and Communication Networks, 7(11), 2225–2236.
Tao, H., Bhuiyan, M. Z., Abdalla, A. N., Hassan, M. M., Zain, J. M., & Hayajneh, T. (2018). Secured data collection with hardware-based ciphers for IoT-based healthcare. IEEE Internet of Things Journal, 6(1), 410–420.
Ismaili, Z. E., & Moussa, A. (2009). Self-partial and dynamic reconfiguration implementation for AES using FPGA. arXiv:0909.2369.
Yoo, S. M., Kotturi, D., Pan, D. W., & Blizzard, J. (2005). An AES crypto chip using a high-speed parallel pipelined architecture. Microprocessors and Microsystems, 29(7), 317–326.
Zhang, J., Li, L., Li, Q., Zhao, J., & Liang, X. (2021). Power analysis attack on a lightweight block cipher gift. In Proceedings of the9th international conference on computer engineering and networks (pp. 565–574). Springer, Singapore.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jamuna Rani, D., Emalda Roslin, S. Optimized Implementation of Gift Cipher. Wireless Pers Commun 119, 2185–2195 (2021). https://doi.org/10.1007/s11277-021-08325-2
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08325-2