Abstract
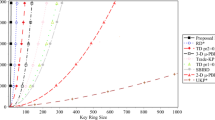
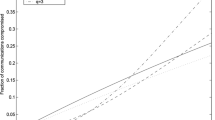
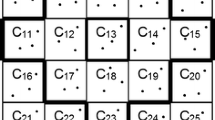
Considering the internet of things (IoT), end nodes such as wireless sensor network, RFID and embedded systems are used in many applications. These end nodes are known as resource-constrained devices in the IoT network. These devices have limitations such as computing and communication power, memory capacity and power. Key pre-distribution schemes (KPSs) have been introduced as a lightweight solution to key distribution in these devices. Key pre-distribution is a special type of key agreement that aims to select keys called session keys in order to establish secure communication between devices. One of these design types is the using of combinatorial designs in key pre-distribution, which is a deterministic scheme in key pre-distribution and has been considered in recent years. In this paper, by introducing a key pre-distribution scheme of this type, we stated that the model introduced in the two benchmarks of KPSs comparability had full connectivity and scalability among the designs introduced in recent years. Also, in recent years, among the combinatorial design-based key pre-distribution schemes, in order to increase resiliency as another criterion for comparing KPSs, attempts were made to include changes in combinatorial designs or they combine them with random key pre-distribution schemes and hybrid schemes were introduced that would significantly reduce the design connectivity. In this paper, using theoretical analysis and maintaining full connectivity, we showed that the strength of the proposed design was better than the similar designs while maintaining higher scalability.



Similar content being viewed by others
References
Madakam, S., Ramaswamy, R., & Tripathi, S. (2015). Internet of things (IoT): A literature review. Journal of Computer and Communications, 3, 164–173.
Kouicem, D. E., Bouabdallah, A., & Lakhlef, H. (2018). Internet of things security: A top-down survey. Computer Networks, 141, 199–221.
Evans, D. (2011). The internet of things how the next evolution of the internet is changing everything. Technical report.
Sicari, A., Rizzardi, D., Miorandi, & Coen-Porisini, A. (2016). Internet of things: Security in the keys. In Q2SWinet MSWiM (pp. 129–133).
Modiri, V., Javadi, H. H. S., & Anzani, M. (2017). A novel scalable key pre-distribution scheme for wireless sensor networks based on residual design. Wireless Personal Communications, 96, 2821–2841.
Eschenauer, L., & Gligor, V. D. (2002). A key management scheme for distributed sensor networks. In Proceedings of the 9th ACM conference on computer and communications security (pp. 41–47). ACM.
Chan, H., & Perrig, A. (2003). Random key predistribution schemes for sensor networks. In Proceedings of the 2003 IEEE symposium on security and privacy (SP 03) (pp. 197–213). IEEE.
Qian, S. (2012). A novel key pre-distribution for wireless sensor networks. Physics Procedia, 25, 2183–2189.
Li, W. S., Tsai, C. W., Chen, M., Hsieh, W. S., & Yang, C. S. (2013). Threshold behavior of multi-path random key pre-distribution for sparse wireless sensor networks. Mathematical and Computer Modeling, 57(11), 2776–2787.
Catakoglu, O., & Levi, A. (2013). Uneven key pre-distribution scheme for multi-phase wireless sensor networks. In E. Gelenbe & R. Lent (Eds.), Information sciences and systems (pp. 359–368). Baltimore: Springer.
Camtepe, S. A., & Yener, B. (2005). Key distribution mechanisms for wireless sensor networks: A survey. Rensselaer Polytechnic Institute, Computer Science Department, Technical Report-TR-05-07.
Blom, R. (1984). An optimal class of symmetric key generation systems. In Advances in cryptology: Proceedings of Eurocrypt 84, lecture notes in computer science (Vol. 209, pp. 335–338). Berlin: Springer.
Blundo, C., Santis, A. D., Herzberg, A., Kutten, S., Vaccaro, U., & Yung, M. (1993). Perfectly-secure key distribution for dynamic conferences. In Advances in cryptology: CRYPTO 92. LNCS (Vol. 740, pp. 471–486).
Wang, N. C., & Chen, H. L. (2013). Improving pairwise key predistribution in wireless sensor networks. In R.-S. Chang, L. C. Jain, & S.-L. Peng (Eds.), Advances in intelligent systems and applications (pp. 521–530). Hualien: Springer.
Camtepe, S. A., & Yener, B. (2004). Combinatorial design of key distribution mechanisms for wireless sensor networks. In P. Samarati, P. Y. A. Ryan, D. Gollmann, & R. Molva (Eds.), ESORICS, volume 3193 of lecture notes in computer science (pp. 293–308). New York: Springer.
Lee, J., & Stinson, D. (2005). A combinatorial approach to key pre-distribution for distributed sensor networks. In IEEE wireless communications and networking conference (WCN’ 05) (pp. 1200–1205). IEEE Communication Society.
Ruj, S., & Roy,B. (2007). Key predistribution using partially balanced designs in wireless sensor networks. In Proceedings of the 5th international conference on parallel and distributed processing and applications, August, Niagara Falls, Canada (pp. 431–445).
Ruj, S., Nayak, A., & Stojmenovic, I. (2013). Pairwise and triple key distribution in wireless sensor networks with applications. IEEE Transactions on Computers, 62(11), 2224–2237.
Bechkit, W., Challal, Y., Bouabdallah, A., & Tarokh, V. (2013). A highly scalable key pre-distribution scheme for wireless sensor networks. IEEE Transactions on Wireless Communications, 12(2), 948–959.
Yuan, Q., Ma, C., Yu, H., & Bian, X. (2018). A key pre-distribution scheme based on \(\mu\)-PBIBD for enhancing resilience in wireless sensor networks. Sensors, 18, 1539.
Du, W., Deng, J., Han, Y. S., Varshney, P. K., Katz, J., & Khalili, A. (2005). A pairwise key predistribution scheme for wireless sensor networks. ACM Transactions on Information and System Security (TISSEC), 8(2), 228–258.
Lee, J., & Stinson, D. R. (2005). Deterministic key predistribution schemes for distributed sensor networks. In Selected areas in cryptography (pp. 294–307). Kingston, ON: Springer.
Camtepe, S. A., & Yener, B. (2007). Combinatorial design of key distribution mechanisms for wireless sensor networks. Journal of ACM/IEEE Transactions on Networking, 15(2), 346–358.
Chakrabarti, D., Maitra, S., & Roy, B. (2006). A key pre-distribution scheme for wireless sensor networks: Merging blocks in combinatorial design. International Journal of Information Security, 5(2), 105–114.
Kavitha, T., & Sridharan, D. (2012). Hybrid design of scalable key distribution for wireless sensor networks. IACSIT International Journal of Engineering and Technology, 2(2), 136–141.
Dargahi, T., Javadi, H. H. S., & Hosseinzadeh, M. (2015). Application-specific hybrid symmetric design of key pre-distribution for wireless sensor networks. Security and Communication Networks, 8(8), 1561–1574.
Zhang, J., & Varadharajan, V. (2010). Wireless sensor network key management survey and taxonomy. Journal of Network and Computer Applications, 33, 63–75.
Paterson, M. B., & Stinson, D. R. (2014). A unified approach to combinatorial key predistribution schemes for sensor networks. Designs, Codes and Cryptography, 71, 433–457.
Xia, G., Huang, Z., & Wang, Z. (2008). Key pre-distribution scheme for wireless sensor networks based on the symmetric balanced incomplete block design. Journal of Computer Research and Development, 45, 154–164.
Lee, J., & Stinson, D. R. (2008). On the construction of practical key predistributoin schemes for distributed sensor networks. Journal of ACM Transactions on Information and System Security, 11(2), 1–35.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Morshed Aski, A., Haj Seyyed Javadi, H. & Shirdel, G.H. A Full Connectable and High Scalable Key Pre-distribution Scheme Based on Combinatorial Designs for Resource-Constrained Devices in IoT Network. Wireless Pers Commun 114, 2079–2103 (2020). https://doi.org/10.1007/s11277-020-07466-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07466-0