Abstract
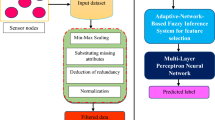
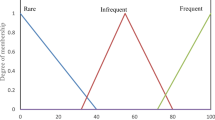
Malicious attacks like denial-of-service massively affect the network activities of wireless sensor network. These attacks exploit network layer vulnerabilities and affect all the layers of the network. Anomaly based intrusion detection system (AIDS) are designed for monitoring such unpredictable attacks but it generates high false positive. In the proposed study we design robust and efficient AIDS which use fuzzy and neural network (NN) based tools. The proposed system can be implemented in each node as it is lightweight and does not consume much overhead. Also it can independently monitor the local nodes behaviour and identify whether a node is trust, distrust or enemy. The use of a trained NN filters the false alarms generated due to fuzzy logic applied in the first step thus enhancing the system accuracy. We evaluate the system’s performance in NS2.35 and result shows a 100% true positive with 0% false positive.





Similar content being viewed by others
References
Lakshmi, H. N., Anand, S., & Sinha, S. (2019). Flooding attack in wireless sensor network-analysis and prevention. International Journal of Engineering and Advanced Technology, 8(5), 1792–1796.
Prasad, K. M., Reddy, A. R. M., & Rao, K. V. (2014). DoS and DDoS attacks: Defense, detection and traceback mechanisms—A survey. Global Journal Computer Science & Technology, 14(7), 1–19.
Zargar, S. T., Jyoti, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed denial of service (DDoS) flooding attacks. IEEE Communication Survey & Tutorials, 15(4), 2046–2069.
Sonar, K., & Upadhyay, H. (2014). Asurvey: DDoS attack on internet of things. International Journal of Engineering Research and Development, 10(11), 58–63.
Deng, J., Han, R., & Mishra, S. (2005). Defending against path-based DoS attacks in wireless sensor networks. In Proceedings of the 3rd ACM workshop on security of ad hoc and sensor networks. ACM.
Paul, A., & Sinha, S. (2017). Performance analysis of received signal power-based sybil detection in MANET using spline curve. International Journal of Mobile Network Design and Innovation, 7(3/4), 222–232.
Deng, J., Han, R., & Mishra, S. (2006). Limiting DoS attacks during multi hop data delivery in wireless sensor networks. International Journal of Security and Networks, 1(3/4), 167–178.
Newsome, J., Shi, E., Song, D., & Perrig, A. (2004). The sybil attack in sensor networks: analysis and defenses. In Proceedings of the 3rd international symposium on information processing in sensor networks, IPSN’04 (New York, NY, USA). ACM.
Sun, B., et al. (2007). Intrusion detection techniques in mobile ad hoc and wireless sensor networks. IEEE Wireless Communication, 14(5), 56–63.
Walters, J. P., Liang, Z., Shi, W., & Chaudhary, V. (2006). Wireless sensor network security: A survey. In Y. Xiao (Ed.), Security in distributed, grid, and pervasive computing (Chapter 17). Boca Raton: Auerbach Publications, CRC Press.
Kizza, J. M. (2017). System intrusion detection and prevention: Guide to computer network security. Computer Communications and Networks. Berlin: Springer.
Kumar, S., & Dutta, K. (2016). Intrusion detection in mobile ad hoc networks: Techniques, systems, and future challenges. Security and Communication Network. https://doi.org/10.1002/sec.1484.
Abduvaliyev, A., Pathan, A. S. K., Jianying, Z., Roman, R., & Wai-Choong, W. (2013). On the vital areas of intrusion detection systems in wireless sensor networks. IEEE Communications Surveys & Tutorials, 15(3), 1223–1237.
Butun, I., Morgera, S. D., & Sankar, R. (2014). A survey of intrusion detection systems in wireless sensor networks. IEEE Communications Surveys & Tutorials, 16(1), 266–282.
Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A., & Rajarajan, M. (2013). A survey of intrusion detection techniques in Cloud. Journal of Network and Computer Applications, 36(1), 42–57.
Gupta, A., Pandey, O., Shukla, M., Dadhich, A., Mathur, S., & Ingle, A. (2013). Computational intelligence based intrusion detection systems for wireless communication and pervasive computing networks. In Computational intelligence and computing research (ICCIC), IEEE international conference (pp. 1–7).
Pongle, P., & Chavan, G. (2015). Real time intrusion and wormhole attack detection in Internet of Things. International Journal of Computer Application, 121(9), 1–9.
Pastrana, S., Mitrokotsa, A., Orfila, A., & Peris-Lopez, P. (2012). Evaluation of classification algorithms for intrusion detection in MANETs. Knowledge-Based Systems, 36, 217–225.
Zarpelão, B. B., Miani, R. S., Kawakani, C. T., & de Alvarenga, S. C. (2017). A survey of intrusion detection in internet of things. Journal of Network and Computer Applications. https://doi.org/10.1016/j.jnca.2017.02.009.
Mehmood, A., Mukherjee, M., & Ahmed, S. A. (2018). NBC-MAIDS: Naïve Bayesian classification technique in multi-agent system-enriched IDS for securing IoT against DDoS attacks. The Journal of Supercomputing, 74(10), 5156.
Ioannou, C., Vassiliou, V., & Sergiou, C. (2017). An intrusion detection system for wireless sensor networks. In 24th international conference on telecommunications (ICT) (pp. 3–5).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sinha, S., Paul, A. Neuro-Fuzzy Based Intrusion Detection System for Wireless Sensor Network. Wireless Pers Commun 114, 835–851 (2020). https://doi.org/10.1007/s11277-020-07395-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07395-y