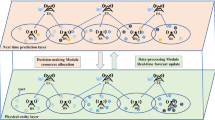
Abstract
Edge computing paradigm extends the cloud service to the edge of networks and reduces service latency to edge users. Meanwhile, the characteristics of edge computing, such as mobility and heterogeneity, arise new privacy security challenges. Current research on privacy security relies on information security techniques like encryption and anonymization. In this paper, we present an application of mean field game theory for privacy leakage with large scale edge devices in edge computing because the edge devices are resource constrained. The contributions are threefold: first, we construct an individual cost function with a mean field term and discuss the evolution of the state if the number of devices is large enough. Subsequently, we elaborate the Nash equilibrium of the mean field game models which are coupled through the Hamiltonian–Jacobi–Bellman (HJB) backward and Fokker–Planck–Kolmogorov (FPK) forward equations. In addition, an approximate method is introduced to analyze the stable solution of the state. Finally, numerical examples are provided to illustrate the stability of the state and the presented strategy.





Similar content being viewed by others
References
Shi, W., Cao, J., Zhang, Q., et al. (2016). Edge computing: Vision and challenges[J]. IEEE Internet of Things Journal,3(5), 637–646.
ECC. (2016). White paper of edge computing consortium. ECC, Beijing, China, White Paper.
Roman, R., Lopez, J., & Mambo, M. (2016). Mobile edge computing, Fog et al.: A survey and analysis of security threats and challenges[J]. Future Generation Computer Systems,78, 680–698.
Polla, M. L., Martinelli, F., & Sgandurra, D. (2013). A survey on security for mobile devices[J]. IEEE Communications Surveys & Tutorials,15(1), 446–471.
Zhang, J., Chen, B., Zhao, Y., et al. (2018). Data security and privacy-preserving in edge computing paradigm: Survey and open issues[J]. IEEE Access,6, 18209–18237.
Zhang, K., Yang, K., Liang, X., et al. (2015). Security and privacy for mobile healthcare networks: From a quality of protection perspective[J]. IEEE Wireless Communications,22(4), 104–112.
Aazam, M., Huh & E.N. (2015). E-HAMC: Leveraging fog computing for emergency alert service[C]. In IEEE international conference on pervasive computing and communication workshops (pp. 518–523). IEEE.
Cao, Y., Chen, S., Hou, P., et al. (2015). FAST: A fog computing assisted distributed analytics system to monitor fall for stroke mitigation[C]. In IEEE international conference on networking, architecture and storage (pp. 2–11). IEEE Computer Society.
Abbas, N., Zhang, Y., Taherkordi, A., et al. (2018). Mobile edge computing: A survey[J]. IEEE Internet of Things Journal,5(1), 450–465.
Zhang, H., Wang, Y., Du, X., et al. (2018). Preserving location privacy in mobile edge computing[J]. arXiv preprint arXiv:1804.01636.
Zhang, Y., Chen, X., Li, J., et al. (2017). Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing[J]. Information Sciences,379, 42–61.
Jia, W., Zhu, H., Cao, Z., et al. (2011). SDSM: A secure data service mechanism in mobile cloud computing[C]. In 2011 IEEE conference on computer communications workshops (INFOCOM WKSHPS) (pp. 1060–1065). IEEE.
Mukherjee, M., Matam, R., Shu, L., et al. (2017). Security and privacy in fog computing: challenges[J]. IEEE Access,PP(99), 1.
Lu, R., Heung, K., Lashkari, A. H., et al. (2017). A lightweight privacy-preserving data aggregation scheme for fog computing-enhanced IoT[J]. IEEE Access,5, 3302–3312.
Huang, Q., Yang, Y., & Wang, L. (2017). Secure data access control with ciphertext update and computation outsourcing in fog computing for internet of things[J]. IEEE Access,5, 12941–12950.
Mao, Y., You, C., Zhang, J., et al. (2017). Mobile edge computing: Survey and research outlook[J]. arXiv preprint arXiv:1701.01090.
Shokri, R., Theodorakopoulos, G., & Troncoso, C. (2017). Privacy games along location traces: A game-theoretic framework for optimizing location privacy[J]. ACM Transactions on Privacy and Security (TOPS),19(4), 11.
Du, J., Jiang, C., Chen, K. C., et al. (2018). Community-structured evolutionary game for privacy protection in social networks[J]. IEEE Transactions on Information Forensics and Security,13(3), 574–589.
Huang, M., Malhame, R. P., & Caines, P. E. (2006). Large population stochastic dynamic games: Closed-loop McKean–Vlasov systems and the Nash certainty equivalence principle[J]. Communications in Information and Systems,6(3), 221–252.
Huang, M., Caines, P. E., & Malhame, R. P. (2007). Large-population cost-coupled LQG problems with nonuniform agents: Individual-mass behavior and decentralized, ε-Nash equilibria[J]. IEEE Transactions on Automatic Control,52(9), 1560–1571.
Lasry, J. M., & Lions, P. L. (2007). Mean field games[J]. Japanese Journal of Mathematics,2(1), 229–260.
Bensoussan, A., Chau, M. H., & Yam, S. C. (2016). Mean field games with a dominating player[M]. New York: Springer.
Onwubolu, G. (2009). Mean field games and applications to economics[J]. Lecture Notes in Mathematics,7(2), 205–266.
Djehiche, B., Tcheukam, A., Tembine, H. (2016). Mean-field-type games in engineering[J]. arXiv preprint arXiv:1605.03281
Mériaux, F., Varma, V., Lasaulce, S. (2012). Mean field energy games in wireless networks[C]. In 2012 conference record of the forty sixth asilomar conference on signals, systems and computers (ASILOMAR), (pp. 671–675). IEEE.
Bauso, D., Tembine, H., & Basar, T. (2016). Opinion dynamics in social networks through mean-field games[J]. SIAM Journal on Control and Optimization,54(6), 3225–3257.
Bauso, D., Tembine, H., & Başar, T. (2016). Robust mean field games[J]. Dynamic Games and Applications,6(3), 277–303.
Tembine, H., Zhu, Q., & Başar, T. (2014). Risk-sensitive mean-field games[J]. IEEE Transactions on Automatic Control,59(4), 835–850.
Bensoussan, A., Frehse, J., & Yam, P. (2013). Mean field games and mean field type control theory[M]. New York: Springer.
Wang, Y., Yu, F. R., Tang, H., et al. (2014). A mean field game theoretic approach for security enhancements in mobile ad hoc networks[J]. IEEE Transactions on Wireless Communications,13(3), 1616–1627.
Miao, L., & Li, S. (2017). Cyber security based on mean field game model of the defender: Attacker strategies[J]. International Journal of Distributed Sensor Networks,13(10), 1550147717737908.
Acknowledgements
We gratefully acknowledge the anonymous reviewers who read the drafts and made many helpful suggestions. This work is supported by the National Science Foundation Project of P. R. China (Nos. 61501026 and 1603116), the Foundation of Science and Technology on Information Assurance Laboratory (No. KJ-17-101).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Miao, L., Wang, L., Li, S. et al. Mean Field Games Theoretic for Mobile Privacy Security Enhancement in Edge Computing. Wireless Pers Commun 111, 2045–2063 (2020). https://doi.org/10.1007/s11277-019-06971-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06971-1