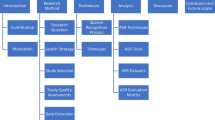
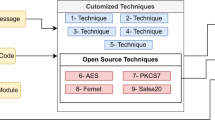
Abstract
Global system for mobile communication (GSM) is widely used digital mobile service around the world. Although GSM was designed as a secure wireless system, it is now vulnerable to different targeted attacks. There is a need to address security domains especially the confidentiality of communication. This paper presents a novel framework for end to end secure voice communication over the GSM networks using encryption algorithm AES-256. A special Modem and speech coding technique are designed to enable the transmission of encrypted speech using GSM voice channel. To the best of our knowledge, this is first solution that uses single codebook for transmission of secure voice. An efficient low bit-rate (1.9 kbps) speech coder is also designed for use with the proposed modulation scheme for optimal results. Different speech characteristics such as pitch, energy and line spectral frequencies are extracted and preserved before compression and encryption of speech. Previously, the best achieved data rate was 1.6 kbps with three codebooks, whilst the proposed approach achieves 2 kbps with 0% bit error rate. The empirical results show that the methodology can be used for real time applications to transmit encrypted voice using GSM network.




















Similar content being viewed by others
References
Xu, Z., (2017). Data transmission method based on single carrier over GSM voice channel. Revista de la Facultad de Ingeniera, 32(9), 23–29.
Giuseppe, C., Giancarlo, D. M., & Ferraro, P. U. (2013). Security issues and attacks on the GSM standard: a review. Journal of Universal Computer Science, 19(16), 2437–2452.
Chouhan, A., & Singh, S. (2015). Real time secure end to end communication over GSM network. International Conference on Energy Systems and Applications.
Biancucci, G., Claudi, A., & Dragoni, A.F., (2013) Secure data and voice transmission over GSM voice channel: Applications for secure communications. 4th International Conference on Intelligent Systems Modelling & Simulation, pp. 230–233.
Katugampala, N., Al-Naimi, K.T., Villete, S., Kondoz, A.M. (2005). Real time end to end secure voice communication over GSM voice channel. 13th European Signal Processing Conference.
Katugampala, N., Villeile, S., & Kondoz, A.M. (2003). Secure voice over GSM and other low bit rate systems. IET.
LaDue, C. K., Sapozhnykov Vitaliy, V., & Fienberg, K. S. (2008). A data modem for GSM voice channel. IEEE Transactions on Vehicular Technology, 57(4), 2205–2218.
Kondoz, A. (1994). Digital speech: Coding for low bit rate communication systems. New York: John Wiley.
Yucun, Yang, Suili, Feng, Wu, Ye, & Xinsheng, Ji (2008). A transmission scheme for encrypted speech over GSM network. International Symposium on Computer Science and Computational Technology, pp. 805–808.
Abro, F.I., Rauf, F., Batool, M., Chowdhry, B. S., & Aslam, S. (2018) An efficient speech coding technique for secure mobile communications. In 8th IEEE Information Technology, Electronics and Mobile Communication Conference (IEMCON).
Qi, H.F., Yang, X.H. et al, (2008). Novel end-to-end voice encryption method in GSM system. IEEE International Conference on Networking, Sensing and Control.
Rekha, A. B., Umadevi, B., Solanke, Y., & Kolli, S. R. (2005). End to end security for GSM users. IEEE International Conference on Personal Wireless Communications.
Biancucci, G., Claudi, A., & Dragoni, A. F. (2013). Secure data and voice transmission over GSM voice channel: Applications for secure communications. 4th International IEEE Conference on Intelligent Systems Modelling & Simulation (ISMS), pp. 230–233.
Islam, S., Ajmal, F., Ali, S., Zahid, J., & Rashdi, A. (2009). Secure end-to-end communication over GSM and PSTN networks. IEEE International Conference on Electro/Information Technology, pp. 323–326.
Duta, C.-L., Gheorghe, L., & Tapus, N. (2017). Real-time DSP implementations of voice encryption algorithms. ICISSP, pp. 439–446.
Lo, C.-C., & Chen, Y.-J. (1999). Secure communication mechanisms for GSM networks. IEEE Transactions on Consumer Electronics, 45(4), 1074–1080.
Daemen, J., & Rijmen, V. (2013). The design of Rijndael: AES-the advanced encryption standard. Berlin: Springer Science & Business Media.
Singh, G., (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for information security. Computer Applications, 67(19).
Hankerson, D., Menezes, A. J., & Vanstone, S. (2006). Guide to elliptic curve cryptography. Berlin: Springer Science & Business Media.
Akif, O. M., & Berna, O. (2015). Data transmission via GSM voice channel for end to end security. IEEE 5th International Conference on Consumer Electronics-Berlin (ICCE-Berlin), pp. 378–382.
Kim, M. Y., Ha, N. K., & Kim, S. R. (1996). Linked split-vector quantizer of LPC parameters. Proceedings of the IEEE ICASSP, 2, 741–744.
Chin-Chen, C., & Yu-Chen, H. (1998). A fast LBG codebook training algorithm for vector quantization. IEEE Transactions on Consumer Electronics, 44(4), 1201–1208.
Kumar, P. A., & Anup, S. (2011). An efficient codebook initialization approach for LBG algorithm, arXiv preprint arXiv:1109.0090, pp. 54–58.
Lee, L. M., & Wang, H. (1996). An extended Levinson-Durbin algorithm for the analysis of noisy autoregressive process. EEE Signal Processing Letters, 3(1), 13–5.
Akif, O. M., Berna, O., & Gokay, S. (2011). Secure voice communication via GSM network. 7th International Conference on Electrical and Electronics Engineering (ELECO), pp. 282–288.
Mahsa, R., Abolghasem, S., & Pejman, M. (2008). Data mapping onto speech-like signal to transmission over the GSM voice channel. 40th IEEE Symposium on System Theory, pp. 54–58.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Rights and permissions
About this article
Cite this article
Abro, F.I., Rauf, F., Mobeen-ur-Rehman et al. Towards Security of GSM Voice Communication. Wireless Pers Commun 108, 1933–1955 (2019). https://doi.org/10.1007/s11277-019-06502-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06502-y