Abstract
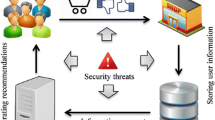
Recently keen interests shown in studying the goal behind a user’s Web query, so that this goal can be used to improve the quality of a search engine’s results in turn improves the popularity of web pages. Advertisement fees can be decided based on this factor. Personalization is now becoming common term for improving E-commerce services and attract more users. Today’s recommender system provides suggestion for specific items but drawback that service provider can increase the ratings of specific product and unnecessarily popularity increases. Traditional data protection mechanisms focus on access control and secure transmission, which provide security only against malicious third parties, but not the service provider. This leads to misguiding the users while purchasing some products, so privacy is violated. Many different approaches including web usage mining have been applied to the basic problem of developing accurate and efficient recommendation systems. Online business transactions and the success of E-commerce depend greatly on the effective design of a product recommender mechanism. Our proposal is founded on homomorphic encryption, which is used to obscure the private rating information of the customers from the service provider. While the user’s privacy is respected by the service provider, by generating recommendations using encrypted customer ratings, the service provider’s commercially valuable item–item similarities are protected against curious entities, in turn. Agent based Web mining has advantages of both Web mining and Agent: it can mine data efficiently and intelligently, so it is becoming more and more important in modern E-business.




Similar content being viewed by others
References
AHamo, Y. & Aljawaherry, M. A. (2012). Constructing a collaborative multi-agents system tool for realtime system requirements. International Journal of Computer Science (IJCSI), 9(4), 134–140.
Cho, Y., & Kim, J. (2004). Application of Web usage mining and product taxonomy to collaborative recommendations in ecommerce. Expert Systems with Applications, 26(2), 233–246.
Cho, Y., Kim, J., & Kim, S. (2002). A personalized recommender system based on web usage mining and decision tree induction. Expert Systems with Applications, 23(3), 329–342.
Cooley, R., Mobasher, B., & Srivastava, J. (1999). Data preparation for mining world wide web browsing patterns. Knowledge and Information Systems, 1, 5–32.
Devi, B., Devi, Y., Rani, B., & Rao, R. (2012). Design and implementation of web usage mining intelligent system in the field of e-commerce. In International conference on communication technology and system design procedia engineering (Vol. 30, pp. 20–27).
Domenech, J. M., & Lorenzo, J. (2007). A tool for web usage mining. In 8th international conference on intelligent data engineering and automated learning, 2007.
Erkin, Z., Beye, M., Veugen, T., & Lagendijk, R. L. (2010). Privacy enhanced recommender system. In Thirty-first symposium on information theory in the Benelux (pp. 35–42), Rotterdam.
Evfimievski, A., & Grandison, T. (2009). Privacy-preserving data mining. San Jose: IBM Almaden Research Center.
Foner, L. (1999). Political artifacts and personal privacy: The yenta multi-agent distributed matchmaking system. PhD thesis, MIT.
Fürnkranz, J. (2005). Web mining. In O. Maimon & L. Rokach (Eds.), The data mining and knowledge discovery handbook (pp. 899–920). Berlin: Springer.
Gahi, Y., Guennoun, M., & El-Khatib, K. (2011). A secure database system using homomorphic encryption schemes. In The third international conference on advances in databases, knowledge, and data applications (DBKDA) (pp. 54–58).
Huang, Y. M., Kuo, Y. H., Chen, J. N., & Jeng, Y. L. (2006). NP-miner: A real-time recommendation algorithm by using web usage mining. Knowledge-Based Systems, 19(4), 272–286.
Jennings, N. R. (2000). On agent-based software engineering. Artificial Intelligence, 117(2), 277–296.
Jiao, J., You, X., & Kumar, A. (2006). An agent-based framework for collaborative negotiation in the global manufacturing supply chain network. Robotics and Computer-Integrated Manufacturing, 22(3), 239–255.
Khosravi, M., & Tarokh, M. J. (2010). Dynamic mining of users interest navigation patterns using naive bayesian method. In Intelligent computer communication and processing (ICCP). IEEE (pp. 119–122).
Kolari, P., & Joshi, A. (2004). Web mining: Research and practice. Computing in Science & Engineering, 6(4), 49–53.
Lindell, Y., & Pinkas, B. (2000). Privacy preserving data mining. In Lecture notes in computer science. Proceedings of advances in cryptology: Crypto’ 2000 (Vol. 1880, pp. 20–24). Springer, Berlin.
Link, H., Saia, J., Lane, T., & LaViolette, R. A. (2005). The impact of social networks on multi-agent recommender systems. In Proceedings of the workshop on cooperative multi-agent learning (ECML/PKDD’05).
Marivate, V. N., Ssali, G., & Marwala, T. (2008). An intelligent multi-agent recommender system for human capacity building (pp. 909–915).
Paydar, S., & Kahani, M. (2011). An agent-based framework for automated testing of web-based systems. Journal of Software Engineering and Applications, 4, 86–94.
Qingning, H., Hong, Z., & Greenwood, S. (2003). A multi-agent software engineering environment for testing web-based applications (pp. 210–215).
Varnagar, C. R., Madhak, N. N., Kodinariya, T. M. & Rathod, J. N. (2013). Web usage mining: A review on process, methods and techniques. In International conference on information communication and embedded systems (ICICES) (pp. 40–46). IEEE.
Yao, A. C. (1982). Protocols for secure computations. IEEE Foundations of Computer Science. In SFCS ‘08. 23rd annual symposium (pp. 160–164). doi:10.1109/SFCS.1982.38.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sobitha Ahila, S., Shunmuganathan, K.L. Role of Agent Technology in Web Usage Mining: Homomorphic Encryption Based Recommendation for E-commerce Applications. Wireless Pers Commun 87, 499–512 (2016). https://doi.org/10.1007/s11277-015-3082-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-3082-y