Abstract
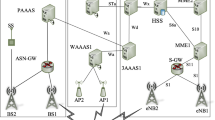
Integrated WiMAX and WiFi networks is of great potential for the future due to the wider coverage of WiMAX and the high data transport capacity of WiFi. However, seamless and secure handover (HO) is one of the most challenging issues in the WiMAX and WiFi heterogeneous networks. In this paper, we present a fast and secure HO authentication scheme based on credential ticket for WiMAX and WiFi heterogeneous networks. In the proposed scheme, Mobile Station (MS) shows its corresponding credential ticket generated by the previously visited Base Station (BS)/Access Point (AP) to the target BS/AP whenever an HO occurs, and then the MS and target BS/AP can complete the mutual authentication and derive their shared session key without interacting with the Authentication, Authorization, and Accounting server, which significantly reduces the HO authentication delay. Moreover, our scheme fulfills the essential security requirements in HO authentication semantics and the formal verification by the AVISPA tool shows that the proposed scheme is secure against various malicious attacks. In addition, the theoretical analysis and simulation indicate that our scheme outperforms the existing HO authentication schemes in terms of communication and computation cost.











Similar content being viewed by others
References
Johann, M., Carlos, T., Cano, J., et al. (2011). An overview of vertical handover techniques: Algorithms, protocols and tools. Computer Communications, 34(8), 985–997.
IEEE 802.11 Work Group. (2009, October). IEEE standard 802.11n-2009: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 5: Enhancements for Higher Throughput. IEEE Technical Report.
Pareit, D., Lannoo, B., Moerman, I., et al. (2012). The history of WiMAX: A complete survey of the evolution in certification and standardization for IEEE 802.16 and WiMAX. IEEE Communications Surveys and Tutorials, 14(4), 1183–1211.
Chen, Y., Hsia, J., & Liao, Y. (2009). Advanced seamless vertical handoff architecture for WiMAX and WiFi heterogeneous networks with QoS guarantees. Computer Communications, 32(2), 281–293.
Pontes, A., dos Passos, Silva D., Jailton, J., et al. (2008). Handover management in integrated WLAN and mobile WiMAX networks. IEEE Wireless Communications, 15(5), 86–95.
Aboba, B., Blunk, L., Vollbrecht, J. et al. (2004, June). Extensible authentication protocol (EAP), IETF RFC 3748.
Politis, C., Chew, K., Akhtar, N., et al. (2004). Hybrid multilayer mobility management with AAA context transfer capabilities for all-IP networks. IEEE Wireless Communications, 11(4), 76–88.
Hsu, S., & Lin, Y. (2009). A key caching mechanism for reducing WiMAX authentication cost in handoff. IEEE Transactions on Vehicular Technology, 58(8), 4507–4513.
Fu, A., Zhang, Y., Zhu, Z., et al. (2012). An efficient handover authentication scheme with privacy preservation for IEEE 802.16m network. Computers and Security, 31(6), 741–749.
Nakhjiri, M. (2007). Use of EAP-AKA, IETF HOKEY and AAA mechanisms to provide access and handover security and 3G–802.16M interworking. In Proceedings of PIMRC’07 (pp. 1–5). September 2007.
Narayanan, V., & Dondeti, L. (2008). EAP extensions for EAP re-authentication protocol (ERP). IETF RFC 5296, August 2008.
Huang, C. M., & Li, J. W. (2009). A cluster-chain-based context transfer mechanism for fast basic service set transition in the centralized wireless LAN architecture. Wireless Communications and Mobile Computing, 9(10), 1387–1401.
Fu, A., Zhang, G., Zhang, Y., et al. (2013). GHAP: An efficient group-based handover authentication mechanism for IEEE 802.16m networks. Wireless Personal Communications, 70(4), 1793–1810.
Ohba, Y., Das, S., & Dutta, A. (2007). Kerberized handover keying: a media-independent handover key management architecture. In Proceedings of MobiArch’07 (pp. 1–7), August 2007.
Fu, A., Zhang, Y., Zhu, Z., et al. (2010). A fast handover authentication mechanism based on ticket for IEEE 802.16m. IEEE Communications Letters, 14(12), 1134–1136.
Kim, Y., Ren, W., Jo, J. et al. (2007). SFRIC: a secure Fast roaming scheme in wireless LAN using ID-based cryptography. In Proceedings of ICC’07 (pp. 1570–1575).
Choi, J., & Jung, S. (2010). A handover authentication using credentials based on chameleon hashing. IEEE Communications Letters, 14(1), 54–56.
He, D., Chen, C., Chan, S., et al. (2012). Secure and efficient handover authentication based on bilinear pairing functions. IEEE Transactions on Wireless Communications, 11(1), 48–53.
Dutta, A., Famolari, D., Das, S., et al. (2008). Media-independent pre-authentication supporting secure interdomain handover optimization. IEEE Wireless Communications, 15(2), 55–64.
Marin-Lopez, R., Pereniguez, F., Bernal, F., et al. (2010). Secure three-party key distribution protocol for fast network access in EAP-based wireless networks. Computer Networks, 54(15), 2651–2673.
Shidhani, A., & Leung, V. (2011). Fast and secure reauthentications for 3GPP subscribers during WiMAX-WLAN handovers. IEEE Transactions on Dependable and Secure, 8(5), 699–713.
Huang, K., Chi, K., Wang, J. et al. (2012). A fast authentication scheme for WiMAX-WLAN vertical handover. Wireless Personal Communications, September 2012. doi:10.1007/s11277-012-0828-7.
Yoon, E., Khan, M. K., & Yoo, K. (2010). Cryptanalysis of a handover authentication scheme using credentials based on chameleon hashing. IEICE Transactions on Information and Systems, E93–D(12), 3400–3402.
WiMAX Forum. (2010). Wi-Fi-WiMAX Interworking. WMF-T37-010-R016v01, November 2010.
WiMAX Forum. (2009). Network architecture-detailed protocols and procedures. WMF-T33-001-R015v01. November 2009.
IEEE 802.16 Work Group. (2011). IEEE standard 802.16m-2011: Air interface for broadband wireless access systems—Amendment 3: Advanced Air Interface. IEEE, technical report, May 2011.
AVISPA v1.1. http://www.avispa-project.org/.
Acknowledgments
This work is supported by National Science Foundation of China (No. 61202352, No. 61272420, No. 61202448 and No. 61272481), National Science Foundation for Post-doctoral Scientists of China (No. 2013T60543 and No. 2012M521088), Specialized Research Fund for the Doctoral Program of Higher Education of China (No. 20123219120030), Natural Science Foundation of Jiangsu Province, China (No. BK20141404 and No. BK2011022) and the Zijin Intelligent Program of NUST, China (2013_ZJ_0209).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Fu, A., Zhang, G., Zhu, Z. et al. Fast and Secure Handover Authentication Scheme Based on Ticket for WiMAX and WiFi Heterogeneous Networks. Wireless Pers Commun 79, 1277–1299 (2014). https://doi.org/10.1007/s11277-014-1930-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-014-1930-9