Abstract
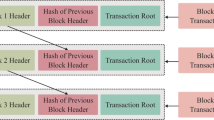
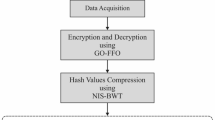
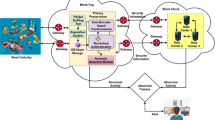
Internet of Things (IoT) devices are an essential part of several aspects of daily life for people. They are utilized in a variety of contexts, including industrial monitoring, environmental sensing, and so on. But, secure communication is the major challenge in the IoT environment. Therefore, a decentralized Blockchain-based Key Management protocol using Levy Flight-Equilibrium Optimization and Self-Attention-based Improved Faster Region-based Convolutional Neural Network (BlkKM) method is proposed to determine stable security in tamper-resistant hardware machine that can protect sensitive secret data in the healthcare field i.e., stored cryptographic keys. The keys are categorized as Key Encryption Keys (KEKs) and Data Encryption Keys (DEKs). The number of the keys is decreased by using Levy Flight- Equilibrium Optimization (LF-EO) as organizing nodes with logical sets. Also, Self-Attention-based Improved Faster Region-based Convolutional Neural Network (SA-based IFRCNN) is used for reordering a set of logical nodes to minimize the number of sets after a node exits the network. Additionally, the system makes use of smart contracts for access control as well as proxy encryption to data encryption. The proposed method is compared with existing techniques to validate the security enhancement performance. The evaluation is performed based on throughput, end-to-end delay, storage overheads, and energy consumption. The experimentation results revealed that the proposed method improved the throughput to 220.52bps and diminished the utilization of energy. A greater degree of memory usage is also decreased by using this technique.











Similar content being viewed by others
Availability of data and materials
The data that support the findings of this study are available from the corresponding author upon reasonable request.
References
Ma, M., Shi, G., & Li, F. (2019). Privacy-oriented blockchain-based distributed key management architecture for hierarchical access control in the IoT scenario. IEEE Access, 7, 34045–34059.
Senthil Pandi, S., Senthilselvi, A., Kumaragurubaran, T., Dhanasekaran, S. (2024). Self-attention-based generative adversarial network optimized with color harmony algorithm for brain tumor classification. Electromagnetic Biology and Medicine, 1–15. https://doi.org/10.1080/15368378.2024.2312363
Senthil Pandi, S., Senthilselvi, A., Maragatharajan, M., Manju, I. (2022). An optimal self adaptive deep neural network and spine-kernelled chirplet transform for image registration. Summary Concurrency and Computation: Practice and Experience, 34(27). https://doi.org/10.1002/cpe.7297
Kalpana, B., Reshmy, A.K., Senthil Pandi, S., Dhanasekaran, S. (2023). OESV-KRF: Optimal ensemble support vector kernel random forest based early detection and classification of skin diseases. Biomedical Signal Processing and Control, 85, 104779. https://doi.org/10.1016/j.bspc.2023.104779
Kandi, M. A., Lakhlef, H., Bouabdallah, A., & Challal, Y. (2020). A versatile key management protocol for secure group and device-to-device communication in the internet of things. Journal of Network and Computer Applications, 150, 102480.
Kim, Y., Nam, J., Park, T., Scott-Hayward, S., & Shin, S. (2019). SODA: A software-defined security framework for IoT environments. Computer Networks, 163, 106889.
Lakhlef, H., & Bouabdallah, A. (2021). Efficient and lightweight group rekeying protocol for communicating things. Computers & Electrical Engineering, 91, 107021.
Festijo, E., Jung, Y., & Peradilla, M. (2019). Software-defined security controller-based group management and end-to-end security management. Journal of Ambient Intelligence and Humanized Computing, 10(9), 3365–3382.
Mughal, M. A., Shi, P., Ullah, A., Mahmood, K., Abid, M., & Luo, X. (2019). Logical tree-based secure rekeying management for smart devices groups in IoT-enabled WSN. IEEE Access, 7, 76699–76711.
Ding, S., Cao, J., Li, C., Fan, K., & Li, H. (2019). A novel attribute-based access control scheme using blockchain for IoT. IEEE Access, 7, 38431–38441.
Bertin, E., Hussein, D., Sengul, C., & Frey, V. (2019). Access control in the Internet of Things: A survey of existing approaches and open research questions. Annals of Telecommunications, 74(7), 375–388.
Atlam, H. F., & Wills, G. B. (2019). An efficient security risk estimation technique for Risk-based access control model for IoT. Internet of Things, 6, 100052.
Alshahrani, M., & Traore, I. (2019). Secure mutual authentication and automated access control for IoT smart home using cumulative keyed-hash chain. Journal of Information Security and Applications, 45, 156–175.
Miao, Y., Liu, X., Deng, R. H., Wu, H., Li, H., Li, J., & Wu, D. (2018). Hybrid keyword-field search with efficient key management for the industrial internet of things. IEEE Transactions on Industrial Informatics, 15(6), 3206–3217.
Wazid, M., Das, A. K., Shetty, S., Rodrigues, J. P. C., & Park, Y. (2019). LDAKM-EIoT: Lightweight device authentication and key management mechanism for edge-based IoT deployment. Sensors, 19(24), 5539.
Dammak, M., Senouci, S. M., Messous, M. A., Elhdhili, M. H., & Gransart, C. (2020). Decentralized lightweight group key management for dynamic access control in IoT environments. IEEE Transactions on Network and Service Management, 17(3), 1742–1757.
Zhaofeng, M., Lingyun, W., Xiaochang, W., Zhen, W., & Weizhe, Z. (2019). Blockchain-enabled decentralized trust management and secure usage control of IoT big data. IEEE Internet of Things Journal, 7(5), 4000–4015.
Zhaofeng, M., Jialin, M., Jihui, W., & Zhiguang, S. (2020). Blockchain-based decentralized authentication modeling scheme in edge and IoT environment. IEEE Internet of Things Journal, 8(4), 2116–2123.
Li, J., Zhou, Z., Wu, J., Li, J., Mumtaz, S., Lin, X., Gacanin, H., & Alotaibi, S. (2019). Decentralized on-demand energy supply for blockchain in the internet of things: A microgrids approach. IEEE transactions on computational social systems, 6(6), 1395–1406.
Muhajjar, R. A., Flayh, N. A., & Al-Zubaidie, M. (2023). A perfect security key management method for hierarchical wireless sensor networks in medical environments. Electronics, 12(4), 1011.
Gowda, N. C., Manvi, S. S., Malakreddy, B., & Lorenz, P. (2023). BSKM-FC: Blockchain-based secured key management in a fog computing environment. Future Generation Computer Systems, 142, 276–291.
Shyaa, G. S., & Al-Zubaidie, M. (2023). Utilizing trusted lightweight ciphers to support electronic-commerce transaction cryptography. Applied Sciences, 13(12), 7085.
Elmanakhly, D. A., Saleh, M. M., & Rashed, E. A. (2021). An improved equilibrium optimizer algorithm for features selection: Methods and analysis. IEEE Access, 9, 120309–120327.
Jia, H., Peng, X., Song, W., Lang, C., Xing, Z., & Sun, K. (2019). Multiverse optimization algorithm based on lévy flight improvement for multi-threshold color image segmentation. IEEE Access, 7, 32805–32844.
Li, Z., Li, Y., Yang, Y., Guo, R., Yang, J., Yue, J., & Wang, Y. (2021). A high-precision detection method of hydroponic lettuce seedlings status based on improved Faster RCNN. Computers and Electronics in Agriculture, 182, 106054.
Kandi, M. A., Kouicem, D. E., Doudou, M., Lakhlef, H., Bouabdallah, A., & Challal, Y. (2022). A decentralized blockchain-based key management protocol for heterogeneous and dynamic IoT devices. Computer Communications, 191, 11–25.
Azbeg, K., Ouchetto, O., & Andaloussi, S. J. (2022). BlockMedCare: A healthcare system based on IoT, Blockchain, and IPFS for data management security. Egyptian Informatics Journal, 23, 329–343.
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Human and animal rights
This article does not contain any studies with human or animal subjects performed by any of the authors.
Informed consent
Informed consent was obtained from all individual participants included in the study.
Consent to participate
Not applicable.
Consent for publication
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rejin Paul, N.R., Purnendu Shekhar, P., Singh, C. et al. SAIF-Cnet: self-attention improved faster convolutional neural network for decentralized blockchain-based key management protocol. Wireless Netw (2024). https://doi.org/10.1007/s11276-024-03728-y
Accepted:
Published:
DOI: https://doi.org/10.1007/s11276-024-03728-y