Abstract
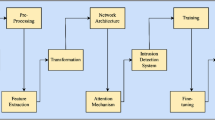
The Internet of Things (IoT) intelligently facilitates individuals interacting with the real-world applications which forms smart environment through internet connectivity at anywhere anytime (dynamic in nature), the devices in an IoT environment encounters several security threats. To overcome these security challenges numerous state of art approaches have been implemented to ensure the security of IoT appliances, but still innovative methods are desirable. The traditional Machine learning (ML) integrates with deep learning algorithm exhibits a potential of detecting abnormal intrusion patterns by formulating a seamless option for anomaly-based detection. This work proposed a Dynamic Distributed—Generative Adversarial Network (DD-GAN) with Improved Firefly Optimization- Hybrid Deep Learning based Convolutional Neural Network -Adaptive Neuro-Fuzzy Inference System (IFFO-HDLCNN + ANFIS) that takes gain of IoT's power, offers enhanced behavior for efficiently examining the entire traffic which traverses in the IoT. Initially, Synthetic Minority Over-sampling Technique (SMOTE) is engaged for pre-processing of data and then Modified Principal Component Analysis (MPCA) is being applied for feature reduction. The optimal features are selected through the Improve Firefly Optimization (IFFO) for optimum fitness value to enhance the classification accuracy of HDLCNN. Finally the intrusion detection is carried out by HDLCNN + ANFIS model, which is competent in detecting threats. The experimental results have proven that model demonstrates ability to perceive any kind of probable intrusion and anomalous behavior. In comparison to existing methods, the suggested IFFO-HDLCNN + ANFIS algorithm delivers improved intrusion detection performance regarding higher accuracy, precision, recall, f-measure, reduced False Positive Rate (FPR).










Similar content being viewed by others
Data availability
The datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
References
Gendreau, A. A., & Moorman, M. (2016, August). Survey of intrusion detection systems towards an end to end secure internet of things. In: 2016 IEEE 4th International conference on future internet of things and cloud (FiCloud) pp. 84–90. IEEE.
Bandyopadhyay, D., & Sen, J. (2011). Internet of things: Applications and challenges in technology and standardization. Wireless personal communications, 58(1), 49–69.
IoT Bots Cause Massive Internet Outage. https://www.beyondtrust.com/blog/iot-bots-cause-october-21st-2016-massive-internet-outage/. Accessed 22 Oct 2016.
Hodo, Elike, et al. 2016 Threat analysis of IoT networks using artificial neural network intrusion detection system.In: 2016 International symposium on networks, computers and communications (ISNCC). IEEE
Li, W., et al. (2019). Designing collaborative blockchained signature-based intrusion detection in IoT environments. Future Generation Computer Systems, 96, 481–489.
Ge, Mengmeng, et al. 2019 Deep learning-based intrusion detection for IoT networks. In: 2019 IEEE 24th Pacific Rim International Symposium on Dependable Computing (PRDC). IEEE
Ding, Yalei, and Yuqing Zhai. 2018 Intrusion detection system for NSL-KDD dataset using convolutional neural networks. In: Proceedings of the 2018 2nd International conference on computer science and artificial intelligence.
Ferdowsi, A., & Saad, W. (2018). Deep learning for signal authentication and security in massive internet-of-things systems. IEEE Transactions on Communications, 67(2), 1371–1387.
Miyato, Takeru, Toshiki Kataoka, Masanori Koyama, and Yuichi Yoshida. (2018) Spectral normalization for generative adversarial networks. arXiv preprint arXiv:1802.05957 .
Verma, A., & Ranga, V. (2020). Machine learning based intrusion detection systems for IoT applications. Wireless Personal Communications, 111(4), 2287–2310.
Yilmaz, Ibrahim, Rahat Masum, and Ambareen Siraj. 2020 Addressing imbalanced data problem with generative adversarial network for intrusion detection. In: 2020 IEEE 21st International conference on information reuse and integration for data science (IRI). IEEE
Ambusaidi, Mohammed A., et al. 2014 A novel feature selection approach for intrusion detection data classification. In: 2014 IEEE 13th International conference on trust, security and privacy in computing and communications. IEEE
Shu, Dule, et al. 2020 Generative adversarial attacks against intrusion detection systems using active learning. In: Proceedings of the 2nd ACM workshop on wireless security and machine learning
Liu, Caiming, et al. 2011 Research on immunity-based intrusion detection technology for the Internet of Things. In: 2011 Seventh International conference on natural computation. Vol. 1. IEEE
Thanigaivelan, Nanda Kumar, et al. "Distributed internal anomaly detection system for Internet-of-Things." 2016 13th IEEE annual consumer communications & networking conference (CCNC). IEEE, 2016.
Schlegl, Thomas, et al. Unsupervised anomaly detection with generative adversarial networks to guide marker discovery. In: International conference on information processing in medical imaging. Springer, Cham, 2017.
Vasan, K. K., & Surendiran, B. (2016). Dimensionality reduction using principal component analysis for network intrusion detection. Perspectives in Science, 8, 510–512.
Intrator, Yotam, Gilad Katz, and Asaf Shabtai. Mdgan (2018) Boosting anomaly detection using\\multi-discriminator generative adversarial networks. arXiv preprint arXiv:1810.05221
Seo, Jae-Hyun, and Yong-Hyuk Kim. (2018) Machine-learning approach to optimize smote ratio in class imbalance dataset for intrusion detection. Computational intelligence and neuroscience 2018.
Najeeb, R. F., & Dhannoon, B. N. (2018). A feature selection approach using binary firefly algorithm for network intrusion detection system. ARPN Journal of Engineering and Applied Sciences, 13(6), 2347–2352.
Rahman, Saoreen, et al. 2016 PHY/MAC layer attack detection system using neuro-fuzzy algorithm for IoT network. In: 2016 International conference on electrical, electronics, and optimization techniques (ICEEOT). IEEE
Yao, H., Wang, Q., Wang, L., Zhang, P., Li, M., & Liu, Y. (2019). An Intrusion Detection framework Based on Hybrid Multi-Level Data Mining. International Journal of Parallel Programming, 47(4), 740–758.
P. Toupas, D. Chamou, K. M. Giannoutakis, A. Drosou and D. Tzovaras, 2019 An Intrusion Detection System for Multi-class Classification Based on Deep Neural Networks, In: 2019 18th IEEE International conference on machine learning and applications (ICMLA) pp. 1253–1258, doi: https://doi.org/10.1109/ICMLA.2019.00206.
Tian Dong, Song Li, Han Qiu, Jialiang Lu., 2022, An Interpretable Federated learning based network intrusion Detection framework, cryptography and network security.
Xiong, Wei, et al. 2018 Learning to generate time-lapse videos using multi-stage dynamic generative adversarial networks. In: Proceedings of the IEEE conference on computer vision and pattern recognition.
Yin, Chuanlong, et al. 2018 An enhancing framework for botnet detection using generative adversarial networks. In: 2018 International conference on artificial intelligence and big data (ICAIBD). IEEE
Upasani, N., & Om, H. (2019). A modified neuro-fuzzy classifier and its parallel implementation on modern GPUs for real time intrusion detection. Applied Soft Computing, 82, 105595.
Zhang, H., et al. (2020). An effective convolutional neural network based on SMOTE and Gaussian mixture model for intrusion detection in imbalanced dataset. Computer Networks, 177, 107315.
Taguchi, Y. H., and Yoshiki Murakami. "Principal component analysis based feature extraction approach to identify circulating microRNA biomarkers." PloS one 8.6 (2013): e66714.
Pal, A. (2018). Principal Component Analysis of TF-IDF In Click Through Rate Prediction‖. International Journal of New Technology and Research IJNTR, ISSN: 2454-4116, 4(12), 24–26.
Yang, X.-S. (2010). Firefly algorithm, Levy flights and global optimization (pp. 209–218). Research and development in intelligent systems XXVI. Springer.
Kaur, A., Pal, S. K., & Singh, A. P. (2018). Hybridization of K-Means and Firefly Algorithm for intrusion detection system. International Journal of System Assurance Engineering and Management, 9.4, 901–910.
Zhang, L., Shan, L., & Wang, J. (2017). Optimal feature selection using distance-based discrete firefly algorithm with mutual information criterion. Neural Computing and Applications, 28(9), 2795–2808.
Cheung, N. J., Ding, X. M., & Shen, H. B. (2014). Adaptive firefly algorithm: Parameter analysis and its application. PLoS ONE, 9(11), e112634.
Turabieh, H., Mafarja, M., & Mirjalili, S. (2019). Dynamic adaptive network-based fuzzy inference system (D-ANFIS) for the imputation of missing data for Internet of medical Things applications. IEEE Internet of Things Journal, 6(6), 9316–9325.
Shahriar, Md Hasan, et al. 2020 G-ids: Generative adversarial networks assisted intrusion detection system. In: 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC). IEEE
Aslam, P. M., & Abulaish, M. (2019). Multi-label classification of microblogging texts using convolution neural network. IEEE Access, 7, 68678–68691.
Reyes-Ortiz, J.-L., et al. (2016). Transition-aware human activity recognition using smartphones. Neurocomputing, 171, 754–767.
Ferdowsi, A., & Saad, W. (2019). Generative adversarial networks for distributed intrusion detection in the internet of things. In: 2019 IEEE Global Communications Conference (GLOBECOM) pp. 1–6. IEEE.
Xie, G., Yang, L. T., Yang, Y., Luo, H., Li, R., & Alazab, M. (2021). Threat analysis for automotive CAN networks: A GAN model-based intrusion detection technique. IEEE Transactions on Intelligent Transportation Systems, 22(7), 4467–4477.
Funding
The authors did not receive support from any organization for the submitted work.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Balaji, S., Narayanan, S.S. Dynamic distributed generative adversarial network for intrusion detection system over internet of things. Wireless Netw 29, 1949–1967 (2023). https://doi.org/10.1007/s11276-022-03182-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-022-03182-8
Keywords
- Internet of things
- Machine learning
- Deep learning
- Anomaly-based detection
- Intrusion detection
- Dynamic distributed—generative adversarial network
- Improved firefly optimization
- Deep learning based convolutional neural network
- Adaptive neuro-fuzzy inference system
- Synthetic minority over-sampling technique and feature selection