Abstract
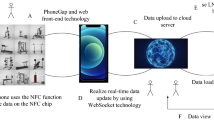
With the continuous maturity and adoption of mobile devices enabled by wireless communication technology, people are more apt to record their sport exercise data or healthcare data through various lightweight and smart devices, e.g., mobile phones and smart watches. Meanwhile, massive sport data or healthcare data keep being produced with time, which forms a main source of big healthcare data. Deep mining and analysis of such healthcare data are of positive significance for accurately recognizing the real-time health condition of mobile users and further recommend appropriate sport items to them. However, traditional centralized healthcare data mining and recommendation approaches require mobile users to transmit their health data collected by mobile devices to a remote cloud platform, which often involves heavy data transmissions from mobile devices to cloud platform. As a consequence, the transmission cost is high and the time delay is long. Moreover, long-distance data transmissions are prone to disclose user privacy. Considering these limitations, we bring forth a novel time-efficient and privacy-preserving healthcare data integration and mining approach for sport item recommendation, based on edge-cloud collaboration mechanism. At last, we design a group of simulation experiments to validate the effectiveness and efficiency of our approach. Experimental comparisons indicate a good balance between different evaluation metrics.





Similar content being viewed by others
References
Jiang, L., Shi, L., Liu, L., Yao, J., & Ali, M.E. (2019). User interest community detection on social media using collaborative filtering. Wireless networks, 1–7.
Feng, S., Shi, H., Huang, L., Shen, S., Yu, S., Peng, H., & Wu, C. (2021). Unknown hostile environment-oriented autonomous wsn deployment using a mobile robot. Journal of Network and Computer Applications, 182, 103053.
Yue, W., Zhao, S., & Zhu, Q. (2022). Mobility-aware caching in energy-harvesting-powered small-cell networks. Wireless Networks, 28(3), 1097–1111.
Feng, S., Wu, C., Zhang, Y., & Oliva, G. (2017). Wsn deployment and localization using a mobile agent. Wireless Personal Communications, 97(4), 4921–4931.
Qi, L., He, Q., Chen, F., Zhang, X., Dou, W., & Ni, Q. (2022). Data-driven web apis recommendation for building web applications. IEEE Transactions on Big Data, 8(3), 685–698.
Shen, S., Huang, L., Zhou, H., Yu, S., Fan, E., & Cao, Q. (2018). Multistage signaling game-based optimal detection strategies for suppressing malware diffusion in fog-cloud-based iot networks. IEEE Internet of Things Journal, 5(2), 1043–1054.
Zhang, Z., Cong, X., Feng, W., Zhang, H., Fu, G., & Chen, J. (2020). Waeas: An optimization scheme of eas scheduler for wearable applications. Tsinghua Science and Technology, 26(1), 72–84.
Qi, L., Song, H., Zhang, X., Srivastava, G., Xu, X., & Yu, S. (2021). Compatibility-aware web api recommendation for mashup creation via textual description mining. ACM Transactions on Multimidia Computing Communications and Applications, 17(1s), 1–19.
Zhang, S., Liu, H., He, J., Han, S., & Du, X. (2021). Deep sequential model for anchor recommendation on live streaming platforms. Big Data Mining and Analytics, 4(3), 173–182.
Song, Z., Cao, Z., Li, Z., Wang, J., & Liu, Y. (2021). Inertial motion tracking on mobile and wearable devices: Recent advancements and challenges. Tsinghua Science and Technology, 26(5), 692–705.
Liu, J., Wang, X., Shen, S., Yue, G., Yu, S., & Li, M. (2020). A bayesian q-learning game for dependable task offloading against ddos attacks in sensor edge cloud. IEEE Internet of Things Journal, 8(9), 7546–7561.
Sandhu, A. K. (2021). Big data with cloud computing: Discussions and challenges. Big Data Mining and Analytics, 5(1), 32–40.
Tan, X., Zhang, J., Zhang, Y., Qin, Z., Ding, Y., & Wang, X. (2020). A puf-based and cloud-assisted lightweight authentication for multi-hop body area network. Tsinghua Science and Technology, 26(1), 36–47.
Liu, J., Wang, X., Shen, S., Fang, Z., Yu, S., Yue, G., & Li, M. (2021). Intelligent jamming defense using dnn stackelberg game in sensor edge cloud. IEEE Internet of Things Journal.
Zhang, W., Chen, X., & Jiang, J. (2020). A multi-objective optimization method of initial virtual machine fault-tolerant placement for star topological data centers of cloud systems. Tsinghua Science and Technology, 26(1), 95–111.
Wang, F., Li, G., Wang, Y., Rafique, W., Khosravi, M. R., Liu, G., Liu, Y., & Qi, L. (2022). Privacy-aware traffic flow prediction based on multi-party sensor data with zero trust in smart city. ACM Transactions on Internet Technology. https://doi.org/10.1145/3511904
Qi, L., Hu, C., Zhang, X., Khosravi, M. R., Sharma, S., Pang, S., & Wang, T. (2021). Privacy-aware data fusion and prediction with spatial-temporal context for smart city industrial environment. IEEE Transactions on Industrial Informatics, 17(6), 4159–4167.
Li, F., Yu, X., Ge, R., Wang, Y., Cui, Y., & Zhou, H. (2021). Bcse: Blockchain-based trusted service evaluation model over big data. Big Data Mining and Analytics, 5(1), 1–14.
Kong, L., Wang, L., Gong, W., Yan, C., Duan, Y., & Qi, L. (2021). Lsh-aware multitype health data prediction with privacy preservation in edge environment. World Wide Web, 1–16 https://doi.org/10.1007/s11280-021-00941-z
Hou, C., Wu, J., Cao, B., & Fan, J. (2021). A deep-learning prediction model for imbalanced time series data forecasting. Big Data Mining and Analytics, 4(4), 266–278.
Martínez Cevallos, D., Alguacil, M., & Calabuig Moreno, F. (2020). Influence of brand image of a sports event on the recommendation of its participants. Sustainability, 12(12), 5040.
Dewi, R. K., Sari, Y. A., Widodo, A. W., Astungkoro, F. P., & Aziz, N. I. M. (2020). Testing for recommendation method in m-health sports venue recommendation system. International Journal of Innovative Technology and Exploring Engineering (IJITEE), 9(6), 2143–2146.
Li, X., & Sun, F. (2021). Sports training recommendation method under the background of data analysis. In 2021 International Conference on High Performance Big Data and Intelligent Systems (HPBD &IS), pp. 12–16. IEEE.
Meng, X., Li, Z., Wang, S., Karambakhsh, A., Sheng, B., Yang, P., Li, P., & Mao, L. (2020). A video information driven football recommendation system. Computers & Electrical Engineering, 85, 106699.
Jayanth, S. B., Anthony, A., Abhilasha, G., Shaik, N., & Srinivasa, G. (2018). A team recommendation system and outcome prediction for the game of cricket. Journal of Sports Analytics, 4(4), 263–273.
Matos, P., Rocha, J., Gonçalves, R., Almeida, A., Santos, F., Abreu, D., & Martins, C. (2019). Smart coach-a recommendation system for young football athletes. In International Symposium on Ambient Intelligence, pp. 171–178 . Springer.
Matos, P., Rocha, J., Gonçalves, R., Santos, F., Abreu, D., Soares, H., & Martins, C. (2020). Hybrid recommendation system for young football athletes customized training. In Future of Information and Communication Conference, pp. 431–442 . Springer.
Zhang, L., & Guo, L. (2022). Application of clustering and recommendation algorithm in sports competition pressure source. Scientific Programming ,2022.
Wang, S., Cong, Y., Zhu, H., Chen, X., Qu, L., Fan, H., Zhang, Q., & Liu, M. (2020). Multi-scale context-guided deep network for automated lesion segmentation with endoscopy images of gastrointestinal tract. IEEE Journal of Biomedical and Health Informatics, 25(2), 514–525.
Cui, W.-H., & Ye, J. (2019). Logarithmic similarity measure of dynamic neutrosophic cubic sets and its application in medical diagnosis. Computers in Industry, 111, 198–206.
Liu, H., Li, X., Luo, B., Wang, Y., Ren, Y., Ma, J., & Ding, H. (2019). Distributed k-anonymity location privacy protection scheme based on blockchain. Chinese Journal of Computers, 42(5), 942–960.
Bosri, R., Rahman, M. S., Bhuiyan, M. Z. A., & Al Omar, A. (2020). Integrating blockchain with artificial intelligence for privacy-preserving recommender systems. IEEE Transactions on Network Science and Engineering, 8(2), 1009–1018.
Li, T., Wang, H., He, D., Yu, J. (2022). Blockchain-based privacy-preserving and rewarding private data sharing for iot. IEEE Internet of Things Journal.
Xu, X., Liu, W., Zhang, Y., Zhang, X., Dou, W., Qi, L., & Bhuiyan, M.Z.A. (2021). Psdf: Privacy-aware iov service deployment with federated learning in cloud-edge computing. ACM Transactions on Intelligent Systems and Technology.
Wu, Z., Shen, S., Zhou, H., Li, H., Lu, C., & Zou, D. (2021). An effective approach for the protection of user commodity viewing privacy in e-commerce website. Knowledge-Based Systems, 220, 106952.
Wu, Z., Li, G., Shen, S., Lian, X., Chen, E., & Xu, G. (2021). Constructing dummy query sequences to protect location privacy and query privacy in location-based services. World Wide Web, 24(1), 25–49.
Wu, Z., Shen, S., Lian, X., Su, X., & Chen, E. (2020). A dummy-based user privacy protection approach for text information retrieval. Knowledge-Based Systems, 195, 105679.
Wu, B., Chen, X., Wu, Z., Zhao, Z., Mei, Z., & Zhang, C. (2021). Privacy-guarding optimal route finding with support for semantic search on encrypted graph in cloud computing scenario. Wireless Communications and Mobile Computing, 2021.
Wang, T., Bhuiyan, M. Z. A., Wang, G., Qi, L., Wu, J., & Hayajneh, T. (2020). Preserving balance between privacy and data integrity in edge-assisted internet of things. IEEE Internet of Things Journal, 7(4), 2679–2689.
Nosouhi, M.R., Yu, S., Sood, K., Grobler, M., Jurdak, R., Dorri, A., & Shen, S. (2021). Ucoin: An efficient privacy preserving scheme for cryptocurrencies. IEEE Transactions on Dependable and Secure Computing, 1–1.
Zhou, X., Li, Y., & Liang, W. (2020). Cnn-rnn based intelligent recommendation for online medical pre-diagnosis support. IEEE/ACM Transactions on Computational Biology and Bioinformatics, 18(3), 912–921.
Qi, L., Lin, W., Zhang, X., Dou, W., Xu, X., & Chen, J. (2022). A correlation graph based approach for personalized and compatible web apis recommendation in mobile app development. IEEE Transactions on Knowledge and Data Engineering. https://doi.org/10.1109/TKDE.2022.3168611
Gu, R., Chen, Y., Liu, S., Dai, H., Chen, G., Zhang, K., Che, Y., & Huang, Y. (2021). Liquid: Intelligent resource estimation and network-efficient scheduling for deep learning jobs on distributed gpu clusters. IEEE Transactions on Parallel and Distributed Systems. https://doi.org/10.1109/TPDS.2021.3138825
Zhou, X., Xu, X., Liang, W., Zeng, Z., & Yan, Z. (2021). Deep-learning-enhanced multitarget detection for end-edge-cloud surveillance in smart iot. IEEE Internet of Things Journal, 8(16), 12588–12596.
Zhou, D., Xue, X., & Zhou, Z. (2022). Sle2: The improved social learning evolution model of cloud manufacturing service ecosystem. IEEE Transactions on Industrial Informatics. https://doi.org/10.1109/TII.2022.3173053
Zhou, X., Liang, W., Kevin, I., Wang, K., & Yang, L. T. (2020). Deep correlation mining based on hierarchical hybrid networks for heterogeneous big data recommendations. IEEE Transactions on Computational Social Systems, 8(1), 171–178.
Li, J., Peng, H., Cao, Y., Dou, Y., Zhang, H., Yu, P., & He, L. (2021). Higher-order attribute-enhancing heterogeneous graph neural networks. IEEE Transactions on Knowledge and Data Engineering. https://doi.org/10.1109/TKDE.2021.3074654
Gu, R., Zhang, K., Xu, Z., Che, Y., Fan, B., Hou, H., Dai, H., Yi, L., Ding, Y., Chen, G., & Huang, Y. (2022). Fluid: Dataset abstraction and elastic acceleration for cloud-native deep learning training jobs. In The 38th IEEE International Conference on Data Engineering, 2183–2196.
Zhou, X., Yang, X., Ma, J., Kevin, I., & Wang, K. (2021). Energy efficient smart routing based on link correlation mining for wireless edge computing in iot. IEEE Internet of Things Journal. https://doi.org/10.1109/JIOT.2021.3077937
Xue, X., Wang, S., Zhang, L., Feng, Z., & Guo, Y. (2018). Social learning evolution (sle): Computational experiment-based modeling framework of social manufacturing. IEEE Transactions on Industrial Informatics, 15(6), 3343–3355.
Dai, H., Wang, X., Lin, X., Gu, R., Shi, S., Liu, Y., Dou, W., & Chen, G. (2021). Placing wireless chargers with limited mobility. IEEE Transactions on Mobile Computing. https://doi.org/10.1109/TMC.2021.3136967
Xie, R., Li, M., Miao, Z., Gu, R., Huang, H., Dai, H., & Chen, G. (2021). Hash adaptive bloom filter. In 2021 IEEE 37th International Conference on Data Engineering (ICDE), 636–647.
Catlett, C., Beckman, P., Ferrier, N., Nusbaum, H., Papka, M. E., Berman, M. G., & Sankaran, R. (2020). Measuring cities with software-defined sensors. Journal of Social Computing, 1(1), 14–27.
Dai, H., Xu, Y., Chen, G., Dou, W., Tian, C., Wu, X., & He, T. (2022). Rose: Robustly safe charging for wireless power transfer. IEEE Transactions on Mobile Computing, 21(6), 2180–2197.
Zhou, X., Liang, W., Li, W., Yan, K., Shimizu, S., & Wang, K.I.-K. (2021). Hierarchical adversarial attacks against graph neural network based iot network intrusion detection system. IEEE Internet of Things Journal. https://doi.org/10.1109/JIOT.2021.3130434
Nath, S., & Wu, J. (2020). Deep reinforcement learning for dynamic computation offloading and resource allocation in cache-assisted mobile edge computing systems. Intelligent and Converged Networks, 1(2), 181–198.
Qi, L.,Yang, Y.,Zhou, X.,Rafique, W., & Ma, J. (2021). Fast anomaly identification based on multi-aspect data streams for intelligent intrusion detection toward secure industry 4.0. IEEE Transactions on Industrial Informatics .https://doi.org/10.1109/TII.2021.3139363
Evans, J. (2020). Social computing unhinged. Journal of Social Computing, 1(1), 1–13.
Bouras, M. A., Farha, F., & Ning, H. (2020). Convergence of computing, communication, and caching in internet of things. Intelligent and Converged Networks, 1(1), 18–36.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Chen, C., Li, C. & Duan, Y. Mobile healthcare data mining for sport item recommendation in edge-cloud collaboration. Wireless Netw (2022). https://doi.org/10.1007/s11276-022-03059-w
Accepted:
Published:
DOI: https://doi.org/10.1007/s11276-022-03059-w