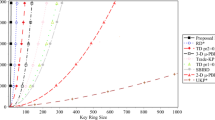
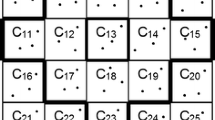
Abstract
Currently, IoT is being used as a novel tool in many applications. Some applications use the end nodes such as wireless sensor network, RFID and embedded systems referred to as resource-constrained devices. These devices have limitations in computing and communication power, memory capacity and power. One of the approaches to discuss key distribution in these devices is to apply and use key pre-distribution schemes (KPSs) as a lightweight solution. Also, the combinatorial designs application in key pre-distribution has been considered as a suitable method due to the low overhead in the shared key discovery phase between devices. This paper assessed the combinatorial designs used in key pre-distribution, and then, compared these designs using KPSs evaluation metrics. Finally, by tabulating all the considered key pre-distribution methods in a comparison table, it was stated that all of these methods could be used in different applications depending on their strengths.


























Similar content being viewed by others
References
Kouicem, D. E., Bouabdallah, A., & Lakhlef, H. (2018). Internet of things security: A top-down survey. Computer Networks, 141, 199–221.
Nikoletseas, S., & Rolim, J. D. P. (2011). Theoretical aspects of distributed computing in sensor networks. Springer. ISBN: 0387954872, Chapter 24.
Modiri, V., Javadi, H. H. S., & Anzani, M. (2017). A novel scalable key pre-distribution scheme for wireless sensor networks based on residual design. Wireless Personal Communications, 96, 2821–2841.
Eschenauer, L., & Gligor, V. D. (2002). A key management scheme for distributed sensor networks. In Proceedings of the 9th ACM conference on computer and communications security (pp. 41–47). ACM.
Chan, H., & Perrig, A. (2003). Random key pre-distribution schemes for sensor networks. In Proceedings of the 2003 IEEE symposium on security and privacy (SP 03) (pp. 197–213). IEEE.
Qian, S. (2012). A novel key pre-distribution for wireless sensor networks. Physics Procedia, 25, 2183–2189.
Li, W. S., Tsai, C. W., Chen, M., Hsieh, W. S., & Yang, C. S. (2013). Threshold behavior of multi-path random key pre-distribution for sparse wireless sensor networks. Mathematical and Computer Modeling, 57(11), 2776–2787.
Catakoglu, O., & Levi, A. (2013). Uneven key pre-distribution scheme for multi-phase wireless sensor networks. In E. Gelenbe & R. Lent (Eds.), Information sciences and systems (pp. 359–368). Springer.
Camtepe, S. A., & Yener, B. (2005). Key distribution mechanisms for wireless sensor networks: A survey. Rensselaer Polytechnic Institute, Computer Science Department, Technical Report-TR-05-07.
Blom, R. (1984). An optimal class of symmetric key generation systems. In Advances in cryptology: Proceedings of Eurocrypt 84, lecture notes in computer science (Vol. 209, pp. 335–338). Springer.
Chien, H. Y., Chen, R. C., & Shen, A. (2008). Efficient key pre-distribution for sensor nodes with strong connectivity and low storage space. In Proceedings of the 2nd international conference on advanced information networking and applications (AINA08), GinoWan, Okinawa, Japan (pp. 327–333). IEEE.
Blundo, C., Santis, A. D., Herzberg, A., Kutten, S., Vaccaro, U., & Yung, M. (1993). Perfectly secure key distribution for dynamic conferences. In Advances in cryptology: CRYPTO 92. LNCS (Vol. 740, pp. 471–486).
Wang, N. C., & Chen, H. L. (2013). Improving pairwise key pre-distribution in wireless sensor networks. In R. S. Chang, L. C. Jain, & S. L. Peng (Eds.), Advances in intelligent systems and applications, Hualien (Vol. 1, pp. 521–530). Springer.
Camtepe, S. A., & Yener, B. (2004). Combinatorial design of key distribution mechanisms for wireless sensor networks. In P. Samarati, P. Y. A. Ryan, D. Gollmann, & R. Molva (Eds.), ESORICS, lecture notes in computer science (Vol. 3193, pp. 293–308). Springer.
Lee, J., & Stinson, D. (2005). A combinatorial approach to key pre-distribution for distributed sensor networks. In IEEE wireless communications and networking conference (WCN’ 05) (Vol. 2, pp. 1200–1205). IEEE Communication Society.
Ruj, S., & Roy, B. (2007). Key pre-distribution using partially balanced designs in wireless sensor networks. In Proceedings of the 5th international conference on parallel and distributed processing and applications, Niagara Falls, Canada, Aug 29-31 (pp. 431–445).
Ruj, S., Nayak, A., & Stojmenovic, I. (2013). Pairwise and triple key distribution in wireless sensor networks with applications. IEEE Transactions on Computers, 62(11), 2224–2237.
Bechkit, W., Challal, Y., Bouabdallah, A., & Tarokh, V. (2013). A highly scalable key pre-distribution scheme for wireless sensor networks. IEEE Transactions on Wireless Communications, 12(2), 948–959.
Yuan, Q., Ma, C., Yu, H., & Bian, X. (2018). A key pre-distribution scheme based on \(\mu\)-PBIBD for enhancing resilience in wireless sensor networks. Sensors, 18, 1539.
Bahrami, P. N., Javadi, H. H., Dargahi, T., Dehghantanha, A., & Choo, K. R. (2019). A hierarchical key pre-distribution scheme for fog networks. Concurrency and Computation: Practice and Experience, 31(22), e4776.
Masaeli, N., Javadi, H. H. S., & Erfani, S. H. (2020). Key pre-distribution scheme based on transversal design in large mobile fog networks with multi-clouds. Journal of Information Security and Applications, 54, 102519. https://doi.org/10.1016/j.jisa.2020.102519.
Du, W., Deng, J., Han, Y. S., Varshney, P. K., Katz, J., & Khalili, A. (2005). A pairwise key pre-distribution scheme for wireless sensor networks. ACM Transactions on Information and System Security (TISSEC), 8(2), 228–258.
Lee, J., & Stinson, D. R. (2005). Deterministic key pre-distribution schemes for distributed sensor networks. In Selected areas in cryptography, Kingston (pp. 294–307). Springer.
Camtepe, S. A., & Yener, B. (2007). Combinatorial design of key distribution mechanisms for wireless sensor networks. Journal of ACM/IEEE Transactions on Networking, 15(2), 346–358.
Chakrabarti, D., Maitra, S., & Roy, B. (2006). A key pre-distribution scheme for wireless sensor networks: Merging blocks in combinatorial design. International Journal of Information Security, 5(2), 105–114.
Kavitha, T., & Sridharan, D. (2012). Hybrid design of scalable key distribution for wireless sensor networks. IACSIT International Journal of Engineering and Technology, 2(2), 136–141.
Dargahi, T., Javadi, H. H. S., & Hosseinzadeh, M. (2015). Application-specific hybrid symmetric design of key pre-distribution for wireless sensor networks. Security and Communication Networks, 8(8), 1561–1574.
Nguyen, K. T., Laurent, M., & Oualha, N. (2015). Survey on secure communication protocols for the Internet of things. Ad Hoc Networks, 32, 17–31.
Paterson, M. B., & Stinson, D. R. (2014). A unified approach to combinatorial key pre-distribution schemes for sensor networks. Design, Codes and Cryptography, 71(3), 433–457.
Bose, M., Dey, A., & Mukerjee, R. (2013). Key pre-distribution schemes for distributed sensor networks via block designs. Design, Codes and Cryptography, 67(1), 111–136.
Henry, K. J., Paterson, M. B., & Stinson, D. R. (2014). Practical approaches to varying network size in combinatorial key pre-distribution schemes. In Selected areas in cryptography (SAC) 2013, number 8282 in lecture notes in computer science (pp. 89–117). Springer.
Stinson, D. R. (2003). Combinatorial designs: Construction and analysis. Springer, ISBN: 0387954872.
Anderson, I. (1990). Combinatorial designs: Construction methods. Ellis Horwood.
Yağan, O., & Makowski, A. M. (2016). Wireless sensor networks under the random pairwise key pre-distribution scheme: Can resiliency be achieved with small key rings? IEEE/ACM Transactions on Networking, 24(6), 3383–3396.
Eletreby, R., & Yağan, O. (2018). Connectivity of wireless sensor networks secured by the heterogeneous random pairwise key pre-distribution scheme. In Proceedings of IEEE conference on decision and control (CDC), 2018. IEEE.
Zhao, J. (2017). Topological properties of wireless sensor networks under the q-composite key pre-distribution scheme with unreliable links. IEEE/ACM Transactions on Networking, 25(3), 1789–1802.
El Hajjar, A., Roussos, G., & Paterson, M. (2016). On the performance of key pre-distribution for RPL-based IoT networks. In N. Mitton, H. Chaouchi, T. Noel, T. Watteyne, A. Gabillon, & P. Capolsini (Eds.), Interoperability, safety and security in IoT (pp. 67–78). Springer.
Kolagar, Q., Javadi, H. H. S., & Bijani, S. (2017). A deterministic multiple key space scheme for wireless sensor networks via combinatorial designs. Journal of Communication Engineering, 6(1), 53–70.
Lee, J., & Stinson, D. R. (2008). On the construction of practical key pre-distributoin schemes for distributed sensor networks. Journal of ACM Transactions on Information and Systems Security, 11(2), 1–35.
Anzani, M., Javadi, H. H. S., & Modiri, V. (2017). Key management scheme for wireless sensor networks based on merging blocks of symmetric design. Wireless Networks, 24, 1–13.
Javanbakht, M., Erfani, H., Javadi, H. H. S., & Daneshjoo, P. (2014). Key pre-distribution scheme for clustered hierarchical wireless sensor networks based on combinatorial designs. Security and Communication Networks, 7, 2003–2014.
Lee, J., & Stinson, D. R. (2006). Common intersection designs. Journal of Combinatorial Designs, 14(4), 251–269.
Dong, J., Pei, D., & Wang, X. (2008). A key pre-distribution scheme based on \(3\)-designs. In Information security and crptography, lecture notes in computer science (Vol. 4990, pp. 81–92).
Liu, D., Ning, P., & Li, R. (2005). Establishing pairwise keys in distributed sensor networks. ACM Transactions on Information and System Security (TISSEC), 8(1), 41–77.
Kolagar, I. Q., Javadi, H. H. S., & Anzani, M. (2017). Hypercube bivariate-based key management for wireless sensor networks. Journal of Sciences, Islamic Republic of Iran, 28(3), 273–285.
Dong, J. W., Pei, D. Y., & Wang, X. L. (2008). A class of key pre-distribution schemes based on orthogonal arrays. Journal of Computer Science and Technology, 23(5), 825–831.
Bush, K. A. (1952). Orthogonal arrays of index unity. The Annals of Mathematical Statistics, 23(3), 426–434.
Pang, S. Q., & Chen, L. Y. (2017). Generalized latin matrix and construction of orthogonal arrays. Acta Mathematicae Applicatae Sinica, 33(4), 1083–1092.
Pang, S. Q., Xu, W. J., Chen, G. Z., & Wang, Y. (2018). Construction of symmetric and asymmetric orthogonal arrays of strength \(t\) from orthogonal partition. Indian Journal of Pure and Applied Mathematics, 49(4), 663–669.
Gao, Q., Ma, W. P., & Li, X. P. (2017). A key pre-distribution scheme based on mixed-level orthogonal arrays. Ad Hoc & Sensor Wireless Networks, 37, 53–69.
Gao, Q., Ma, W. P., & Luo, W. (2018). Key pre-distribution schemes for wireless sensor networks based on combinations of orthogonal arrays. Ad Hoc Networks, 73, 40–50.
Pang, S., Li, Y., Gao, Q., Xia, Y., & Hu, X. (2020). Key pre-distribution schemes based on orthogonal arrays with unique Hamming distance distribution. Wireless Personal Communications, 112, 1919–1945. https://doi.org/10.1007/s11277-020-07133-4.
Sudan, M. (2001). Algorithmic introduction to coding theory lecture 4. http://people.csail.mit.edu/madhu/FT01/scribe/lect4.ps. Accessed 10 Feb 2020.
Ruj, S., & Roy, B. (2008). Key pre-distribution schemes using codes in wireless sensor networks. In Information security and cryptology (pp. 275–288). Springer.
Sarkar, P., Saha, A., & Chowdhury, M. U. (2010). Secure connectivity model in wireless sensor networks (WSN) using first order Reed–Muller codes. In 2010 IEEE 7th International conference on mobile adhoc and sensor systems (MASS) (pp. 507–512). IEEE.
Hui, K. (2011). Secure communication of wireless sensor network (WSN) using coding theory. International Journal of Computer Networks and Communications Security, 1, 342–346.
Dalai, D. K., & Sarkar, P. (2017). Sensornet: A key pre-distribution scheme for distributed sensors using nets. In SENSORNETS (pp. 49–58).
Biswas, C., & Dutta, R. (2020). Implementation of key pre-distribution scheme in WSN based on binary Goppa codes and Reed–Solomon codes with enhanced connectivity and resiliency. Journal of Ambient Intelligence and Humanized Computing. https://doi.org/10.1007/s12652-020-01869-4.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Solari Esfehani, N., Haj Seyyed Javadi, H. A survey of key pre-distribution schemes based on combinatorial designs for resource-constrained devices in the IoT network. Wireless Netw 27, 3025–3052 (2021). https://doi.org/10.1007/s11276-021-02629-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-021-02629-8