Abstract
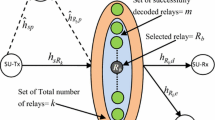
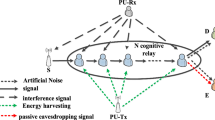
In this paper, we evaluate the secrecy outage performance and throughput of a hybrid cognitive radio network, where a secondary user (SU) accesses the primary spectrum either in underlay or overlay mode based on spectrum sensing decision. In underlay, the transmit power of the SU as well as the relay is limited by the maximum acceptable interference at primary user (PU) receiver as required by an PU outage constraint, a quality of service for PU. The secondary network employs a decode and forward relay which harvests energy from the radio frequency signal of SU following a time switching relaying protocol. We develop analytical expressions for secrecy outage considering the impact of sensing decision and sensing time. Impact of sensing time, imperfect channel state information of interfering link, energy harvesting time, acceptable interference threshold and PU outage constraint on the secrecy outage probability, as well as throughput of SU are investigated. Further, an interplay between throughput performance and secrecy outage of the network is highlighted.







Similar content being viewed by others
References
Mitola, J. (2000). Cognitive radio: An integrated agent architecture for software defined radio, PhD dissertation, Royal Institute of Technology (KTH), Stockholm, Sweden
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220. https://doi.org/10.1109/JSAC.2004.839380.
Goldsmith, A., Jafar, S. A., Maric, I., & Srinivasa, S. (2009). Breaking spectrum gridlock with cognitive radios: An information theoretic perspective. IEEE Proceedings, 97(5), 894–914.
Song, H., Hong, J. P., & Choi, W. (2013). On the optimal switching probability for a hybrid cognitive radio system. IEEE Transactions on Wireless Communications, 12(4), 1594–1605.
Senthuran, S., Anpalagan, A., & Das, O. (2012). Throughput analysis of opportunistic access strategies in hybrid underlay-overlay cognitive radio networks. IEEE Transactions on Wireless Communications, 11(6), 2024–2035.
Akyildiz, I. F., Lee, W.-Y., Vuran, M. C., & Mohanty, S. (2006). NeXt generation/dynamic spectrum access/cognitive radio wireless networks: A survey. Computer Networks, 50(13), 2127–2159.
Urkowitz, H. (1967). Energy detection of unknown deterministic signals. Proceedings of IEEE, 55(4), 523–531.
Liang, Y. C., Zeng, Y., Peh, E. C. Y., & Hoang, A. T. (2008). Sensing—Throughput tradeoff for cognitive radio network. IEEE Transactions on Wireless Communications, 7(4), 1326–1337.
Zhang, Q., Jia, J., & Zhang, J. (2009). Cooperative relay to improve diversity in cognitive radio networks. IEEE Communications Magazine, 47(2), 111–117.
Nasir, A. A., Zhou, X., Durrani, S., & Kennedy, R. A. (2013). Relaying protocols for wireless energy harvesting and information processing. IEEE Transactions on Wireless Communications, 12(7), 3622–3636. https://doi.org/10.1109/TWC.2013.062413.122042.
Zhou, X., Zhang, R., & Ho, C. K. (2013). Wireless information and power transfer: Architecture design and rate-energy tradeoff. IEEE Transactions on Communications, 61(11), 4754–4767.
Zhao, N., Zhang, S., Yu, F. R., Chen, Y., Nallanathan, A., & Leung, V. C. M. (2017). Exploiting interference for energy harvesting: A survey. IEEE Access Research Issues, and Challenges, 5, 10403–10421.
Zhao, N., Cao, Y., Yu, F. R., Chen, Y., Jin, M., & Leung, V. C. M. (2018). Artificial noise assisted secure interference networks with wireless power transfer. IEEE Transactions on Vehicular Technology, 67(2), 1087–1098.
Zhao, N., Yu, F. R., & Leung, V. C. M. (2015). Wireless energy harvesting in interference alignment networks. IEEE Communications Magazine, 53(6), 72–78.
Zhou, L., & Chao, H. C. (2011). Multimedia traffic security architecture for the internet of things. IEEE Network, 25(3), 35–40.
Delfs, H., & Knebl, H. (2007). Introduction to cryptography: Principles and applications (2nd ed.). Berlin: Springer.
Hong, Y. W. P., Lan, P. C., & Kuo, C. C. J. (2013). Enhancing physical-layer secrecy in multiantenna wireless systems: An overview of signal processing approaches. IEEE Signal Processing Magazine, 30(5), 29–40. https://doi.org/10.1109/MSP.2013.2256953.
Wyner, A. D. (1975). The wire-tap channel. The Bell System Technical Journal, 54(8), 1355–1387. https://doi.org/10.1002/j.1538-7305.1975.tb02040.x.
Bloch, M., Barros, J., Rodrigues, M. R. D., & McLaughlin, S. W. (2008). Wireless information-theoretic security. IEEE Transactions on Information Theory, 54(6), 2515–2534.
Maji, P., Prasad, B., Roy, S. D., & Kundu, S. (2018). Secrecy outage of a cognitive radio network with selection of energy harvesting relay and imperfect CSI. Wireless Personal Communications, 100(2), 571–586.
Prasad, B., Roy, S. D., & Kundu, S. (2014). Outage performance of cognitive relay network with imperfect channel estimation under proactive DF relaying. In Twentieth National Conference on Communications (NCC), Kanpur (pp. 1–6).
Maji, P., Dhar Roy, S., & Kundu, S. (2018). Physical layer security in cognitive radio network with energy harvesting relay and jamming in the presence of direct link. IET Communications, 12(11), 1389–1395.
Suraweera, H. A., Smith, P. J., & Shafi, M. (2010). Capacity limits and performance analysis of cognitive radio with imperfect channel knowledge. IEEE Transactions on Vehicular Technology, 59(4), 1811–1822.
Zhang, X., Xing, J., Yan, Z., Gao, Y., & Wang, W. (2013). Outage performance study of cognitive relay networks with imperfect channel knowledge. IEEE Communications Letters, 17(1), 27–30.
Gradshteyn, I. S., & Ryzhik, I. M. (2000). Table of integrals, series, and products (7th ed.). New York: Academic Press.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix 1. Derivation of CDF of \(\gamma _{sr}^u\)
Similarly, we can derive the CDF of \({F_{\gamma _{se}^u}}(x)\) as
Appendix 2. Derivation of CDF of \(\gamma _{rd}^u\)
Now the CDFs of \({F_{{X_1}}}({x_1})\) and \({F_{{X_2}}}({x_2})\) can be derived as,
where Ei(.) is the exponential integral [25], 3.353.3]
Substituting the CDFs \({F_{{X_1}}}({x_1})\) and \({F_{{X_2}}}({x_2})\) from Eqs. (53) and 54 respectively into Eq. (52)
Appendix 3. Derivation of CDF of \(\gamma _{m}^u\)
By substituting the CDFs of \({F_{\gamma _{sr}^u}}(x)\) and \({F_{\gamma _{rd}^u}}(x)\) from Eqs. (50) and (55) respectively in the above Eq. (56) we can get
Appendix 4. Derivation of CDF of \(\gamma _{rd}^o\)
where \({a_2} = \frac{{2\delta \alpha {P_{m\,}}}}{{(1 - \alpha )\,{\sigma ^2}}}\) , \(\beta = \frac{{4x}}{{{a_2}{\lambda _{sr}}}}\), \(\gamma = \frac{1}{{{\lambda _{rd}}}}\) and \(K_1()\) is the first-order modified Bessel function of the second kind.By using the formula \(\int \limits _0^\infty {\exp \left( { - \frac{\beta }{{4x}} - \gamma x} \right) } \,dx = \sqrt{\frac{\beta }{\gamma }} {K_1}(\sqrt{\beta \gamma } )\),[25],3.324.1] we have calculated the above Eq. (58).
Appendix 5. Derivation of CDF of \(\gamma _{m}^o\)
By substituting the CDFs of \({F_{\gamma _{sr}^o}}(x)\) and \({F_{\gamma _{rd}^o}}(x)\) from Eqs. (36) and 58 respectively in the above Eq. (59) we can get
Rights and permissions
About this article
Cite this article
Maji, P., Yadav, K., Roy, S.D. et al. Secrecy and throughput performance of an energy harvesting hybrid cognitive radio network with spectrum sensing. Wireless Netw 26, 1301–1314 (2020). https://doi.org/10.1007/s11276-019-02183-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-019-02183-4