Abstract
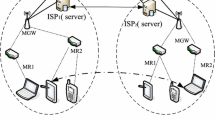
Wireless mesh networks (WMNs) are a kind of wireless ad hoc networks that are multi-hop where packets are forwarded from source to destination by intermediate notes as well as routers that form a kind of network infrastructure backbone. We investigate the security of the recently proposed first known secure authentication and billing architecture for WMNs which eliminates the need for bilateral roaming agreements and that for traditional home-foreign domains. We show that this architecture does not securely provide incontestable billing contrary to designer claims and furthermore it does not achieve entity authentication. We then present an enhanced scheme that achieves entity authentication and nonrepudiable billing.
Similar content being viewed by others
References
Abdalla, M., Fouque, P.-A., & Pointcheval, D. (2006). Password-based authenticated key exchange in the three-party setting. IEE Proceedings-Information Security, 153(1), 27–39.
Akyildiz, I. F., & Wang, X. (2005). A survey on wireless mesh networks. IEEE Communications Magazine, 43(9), S23–S30.
Akyildiz, I. F., Wang, X., & Wang, W. (2005). Wireless mesh networks: A survey. Computer Networks, 47(4), 445–487.
Boyd, C., & Mathuria, A. (2003). Protocols for authentication and key establishment. Berlin: Springer.
Choo, K.-K. R., Boyd, C., & Hitchcock, Y. (2005). Examining indistinguishability-based proof models of key establishment protocols. Advances in Cryptology-ASIACRYPT ’05 LNCS, 3788, 585–604.
Diffie, W.,van Oorschot, P. C., & Wiener, M. J. (1992). Authentication and authenticated key exchanges. Design, Codes and Cryptography, 2(2), 107–125.
Gennaro, R., & Rohatgi, P. (2001). How to sign digital streams. Information and Computation, 165(1), 100–116.
Just, M., & Vaudenay, S. (1996). Authenticated multi-party key agreement. Advances in Cryptology-Asiacrypt ’96 LNCS, 1163, 36–49.
Kaliski, Jr., B. S. (2001). An unknown key-share attack on the MQV key agreement protocol. ACM TISSEC, 4(3), 275–288.
Lee, T.-F., Chang, S.-H., Hwang, T., & Chong, S.-K. (2009). Enhanced delegation-based authentication protocol for PCSs. IEEE Transactions on Wireless Communications, 8(5), 2166–2171.
Lee, M. J., Zheng, J., Ko, Y.-B., & Shrestha, D. M. (2006). Emerging standards for wireless mesh technology. IEEE Wireless Communications, 13(2), 56–63.
Lin, X., Lu, R., Ho, P.-H., & Shen, X. S. (2008). TUA: A Novel compromise-resilient authentication architecture for wireless mesh networks. IEEE Transactions on Wireless Communications, 7(4), 1389–1399.
Menezes, A. J., van Oorschot, P. C., & Vanstone, S. A. (1997). Handbook of applied cryptography. FL: CRC Press.
Portmann, M., & Pirzada, A. A. (2008). wireless mesh networks for public safety and crisis management applications. IEEE Internet Computing, 12(1), 18–25.
Ren, K., Lou, W., Zeng, K., & Moran, P. J. (2007). On broadcast authentication in wireless sensor networks. IEEE Transactions on Wireless Communications, 6(11), 4136–4144.
Tang, C., & Wu, D. O. (2008). mobile privacy in wireless networks–revisited. IEEE Transactions on Wireless Communications, 7(3), 1035–1042.
Tang, C., & Wu, D. O. (2008). An efficient mobile authentication scheme for wireless networks. IEEE Transactions on Wireless Communications, 7(4), 1408–1416.
Zhang ,Y., & Fang, Y. (2006). ARSA: An attack-resilient security architecture for multihop wireless mesh networks. IEEE Journal on Selected Areas in Communications, 24(10), 1916–1928.
Zhang, Y., & Fang, Y. (2007). A secure authentication and billing architecture for wireless mesh networks. Wireless Networks, 13(5), 663–678.
Zhang, Y., Lou, W., & Fang, Y. (2007). A secure incentive protocol for mobile ad hoc networks. Wireless Networks, 13(5), 569–582.
Zhou, Y., & Fang, Y. (2007). A Two-layer key establishment scheme for wireless sensor networks. IEEE Transactions on Mobile Computing, 6(9), 1009–1020.
Zhu, H., Lin, X., Lu, R., Ho, P.-H., & Shen, X. S. (2008). SLAB: A secure localized authentication and billing scheme for wireless mesh networks. IEEE Transactions on Wireless Communications, 7(10), 3858–3868.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Phan, R.CW. Non-repudiable authentication and billing architecture for wireless mesh networks. Wireless Netw 17, 1055–1061 (2011). https://doi.org/10.1007/s11276-011-0334-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-011-0334-y