Abstract
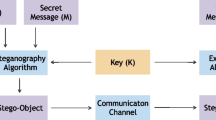
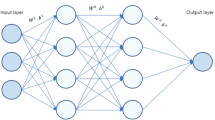
Artificial neural networks have advanced the frontiers of reversible steganography. The core strength of neural networks is the ability to render accurate predictions for a bewildering variety of data. Residual modulation is recognised as the most advanced reversible steganographic algorithm for digital images. The pivot of this algorithm is predictive analytics in which pixel intensities are predicted given some pixel-wise contextual information. This task can be perceived as a low-level vision problem and hence neural networks for addressing a similar class of problems can be deployed. On top of the prior art, this paper investigates predictability of pixel intensities based on supervised and unsupervised learning frameworks. Predictability analysis enables adaptive data embedding, which in turn leads to a better trade-off between capacity and imperceptibility. While conventional methods estimate predictability by the statistics of local image patterns, learning-based frameworks consider further the degree to which correct predictions can be made by a designated predictor. Not only should the image patterns be taken into account but also the predictor in use. Experimental results show that steganographic performance can be significantly improved by incorporating the learning-based predictability analysers into a reversible steganographic system.












Similar content being viewed by others
References
Goodfellow, I., Shlens, J., & Szegedy, C. (2015). Explaining and harnessing adversarial examples. In Proceedings of international conference on learning representations (ICLR), San Diego, CA, USA (pp. 1–11).
Moosavi-Dezfooli, S.-M., Fawzi, A., & Frossard, P. (2016). DeepFool: A simple and accurate method to fool deep neural networks. In Proceedings of IEEE conference on computer vision and pattern recognition (CVPR), Las Vegas, NV, USA (pp. 2574–2582).
Muñoz-González, L., Biggio, B., Demontis, A., Paudice, A., Wongrassamee, V., Lupu, E. C., & Roli, F. (2017). Towards poisoning of deep learning algorithms with back-gradient optimization. In Proceedings of ACM workshop on artificial intelligence and security (AISec), Dallas, TX, USA (pp. 27–38).
Anderson, R., & Petitcolas, F. (1998). On the limits of steganography. IEEE Journal on Selected Areas in Communications, 16(4), 474–481.
Bartolini, F., Tefas, A., Barni, M., & Pitas, I. (2001). Image authentication techniques for surveillance applications. Proceedings of the IEEE, 89(10), 1403–1418.
Abolfathi, M., & Amirfattahi, R. (2012). Design and implementation of a reliable and authenticated satellite image communication. Telecommunication Systems, 49(2), 171–177.
Fridrich, J., Goljan, M., & Du, R. (2002). Lossless data embedding—New paradigm in digital watermarking. EURASIP Journal on Advances in Signal Processing, 986842(2002), 185–196.
De Vleeschouwer, C., Delaigle, J.-F., & Macq, B. (2003). Circular interpretation of bijective transformations in lossless watermarking for media asset management. IEEE Transactions on Multimedia, 5(1), 97–105.
Tian, J. (2003). Reversible data embedding using a difference expansion. IEEE Transactions on Circuits and Systems for Video Technology, 13(8), 890–896.
Celik, M. U., Sharma, G., & Tekalp, A. M. (2006). Lossless watermarking for image authentication: A new framework and an implementation. IEEE Transactions on Image Processing, 15(4), 1042–1049.
Ni, Z., Shi, Y.-Q., Ansari, N., & Su, W. (2006). Reversible data hiding. IEEE Transactions on Circuits and Systems for Video Technology, 16(3), 354–362.
Lee, S., Yoo, C. D., & Kalker, T. (2007). Reversible image watermarking based on integer-to-integer wavelet transform. IEEE Transactions on Information Forensics and Security, 2(3), 321–330.
Coltuc, D. (2012). Low distortion transform for reversible watermarking. IEEE Transactions on Image Processing, 21(1), 412–417.
Feng, G., Qian, Z., & Zhang, X. (2012). Spectrum-estimation based lossless information recovery for sparse array patterns. Telecommunication Systems, 49(2), 163–169.
Shi, Y.-Q., Li, X., Zhang, X., Wu, H., & Ma, B. (2016). Reversible data hiding: Advances in the past two decades. IEEE Access, 4, 3210–3237.
Shannon, C. E. (1948). A mathematical theory of communication. Bell System Technical Journal, 27(3), 379–423.
Thodi, D. M., & Rodriguez, J. J. (2007). Expansion embedding techniques for reversible watermarking. IEEE Transactions on Image Processing, 16(3), 721–730.
Fallahpour, M. (2008). Reversible image data hiding based on gradient adjusted prediction. IEICE Electronics Express, 5(20), 870–876.
Dragoi, I., & Coltuc, D. (2014). Local prediction based difference expansion reversible watermarking. IEEE Transactions on Image Processing, 23(4), 1779–1790.
Hwang, H. J., Kim, S., & Kim, H. J. (2016). Reversible data hiding using least square predictor via the LASSO. EURASIP Journal on Image and Video Processing, 2016(1), 42.
Kalker, T. & Willems, F. M. J. (2002). Capacity bounds and constructions for reversible data-hiding. In Proceedings of international conference on digital signal processing (DSP), Santorini, Greece (pp. 71–76).
Carli, M., Campisi, P., & Neri, A. (2006). Perceptual aspects in data hiding. Telecommunication Systems, 33(1), 117–129.
Wang, J., Ni, J., Zhang, X., & Shi, Y.-Q. (2017). Rate and distortion optimization for reversible data hiding using multiple histogram shifting. IEEE Transactions on Cybernetics, 47(2), 315–326.
Hu, R., & Xiang, S. (2021). CNN prediction based reversible data hiding. IEEE Signal Processing Letters, 28, 464–468.
Chang, C.-C. (2021). Neural reversible steganography with long short-term memory. Security and Communication Networks, 2021, 5580272.
Tai, Y., Yang, J., Liu, X., & Xu, C. (2017). MemNet: A persistent memory network for image restoration. In Proceedings of IEEE international conference on computer vision (ICCV), Venice, Italy (pp. 4549–4557).
Sachnev, V., Kim, H. J., Nam, J., Suresh, S., & Shi, Y.-Q. (2009). Reversible watermarking algorithm using sorting and prediction. IEEE Transactions on Circuits and Systems for Video Technology, 19(7), 989–999.
Li, X., Yang, B., & Zeng, T. (2011). Efficient reversible watermarking based on adaptive prediction-error expansion and pixel selection. IEEE Transactions on Image Processing, 20(12), 3524–3533.
Peng, F., Li, X., & Yang, B. (2012). Adaptive reversible data hiding scheme based on integer transform. Signal Processing, 92(1), 54–62.
Cao, F., An, B., Yao, H., & Tang, Z. (2019). Local complexity based adaptive embedding mechanism for reversible data hiding in digital images. Multimedia Tools and Applications, 78(7), 7911–7926.
LeCun, Y., Bengio, Y., & Hinton, G. E. (2015). Deep learning. Nature, 521(7553), 436–444.
Baluja, S. (2017). Hiding images in plain sight: Deep steganography. Proceedings of international conference on neural information processing systems (NeurIPS), 30, 2066–2076.
Hayes, J., & Danezis, G. (2017). Generating steganographic images via adversarial training. In Proceedings of international conference on neural information processing systems (NeurIPS), Long Beach, CA, USA (pp. 2066–2076)
Tang, W., Tan, S., Li, B., & Huang, J. (2017). Automatic steganographic distortion learning using a generative adversarial network. IEEE Signal Processing Letters, 24(10), 1547–1551.
Zhu, J., Kaplan, R., Johnson, J., & Li, F.-F. (2018). HiDDeN: Hiding data with deep networks. In Proceedings of European conference on computer vision (ECCV), Munich, Germany (pp. 682–697).
Volkhonskiy, D., Nazarov, I., & Burnaev, E. (2019). Steganographic generative adversarial networks. In Proceedings of international conference on machine vision (ICMV), Amsterdam, Netherlands (pp. 1–15).
Wengrowski, E., & Dana, K. (2019). Light field messaging with deep photographic steganography. In Proceedings of IEEE conference on computer vision and pattern recognition (CVPR), Long Beach, CA, USA (pp. 1515–1524).
Tancik, M., Mildenhall, B., & Ng, R. (2020). StegaStamp: Invisible hyperlinks in physical photographs. In Proceedings of IEEE/CVF conference on computer vision and pattern recognition (CVPR), Seattle, WA, USA (pp. 2114–2123).
Luo, X., Zhan, R., Chang, H., Yang, F., & Milanfar, P. (2020) Distortion agnostic deep watermarking. In Proceedings of IEEE/CVF conference on computer vision and pattern recognition (CVPR), Seattle, WA, USA (pp. 13545–13554).
Zhang, Z., Fu, G., Di, F., Li, C., & Liu, J. (2019). Generative reversible data hiding by image-to-image translation via GANs. Security and Communication Networks, 2019, 4932782.
Duan, X., Jia, K., Li, B., Guo, D., Zhang, E., & Qin, C. (2019). Reversible image steganography scheme based on a U-Net structure. IEEE Access, 7, 9314–9323.
Lu, S.-P., Wang, R., Zhong, T., & Rosin, P. L. (2021). Large-capacity image steganography based on invertible neural networks. In Proceedings of IEEE/CVF conference on computer vision and pattern recognition (CVPR), virtual (pp. 10816–10825).
Chang, C.-C. (2020). Adversarial learning for invertible steganography. IEEE Access, 8, 198425–198435.
Krizhevsky, A., Sutskever, I., & Hinton, G. E. (2012). ImageNet classification with deep convolutional neural networks. In Proceedings of international conference on neural information processing systems (NeurIPS), Lake Tahoe, NV, USA (pp. 1097–1105).
Simonyan, K., & Zisserman, A. (2015) Very deep convolutional networks for large-scale image recognition. In Proceedings of international conference on learning representations (ICLR), San Diego, CA, USA (pp. 1–14).
Szegedy, C., Liu, W., Jia, Y., Sermanet, P., Reed, S., Anguelov, D., Erhan, D., Vanhoucke, V., & Rabinovich, A. (2015). Going deeper with convolutions. In Proccedings of IEEE conference on computer vision and pattern recognition (CVPR), Boston, MA, USA (pp. 1–9).
Wilson, E. B. (1923). First and second laws of error. Journal of the American Statistical Association, 18(143), 841–851.
Zhang, Y., Tian, Y., Kong, Y., Zhong, B., & Fu, Y. (2018). Residual dense network for image super-resolution. In Proceedings of IEEE conference on computer vision and pattern recognition (CVPR), Salt Lake City, UT, USA (pp 2472–2481).
Glorot, X., Bordes, A., & Bengio, Y. (2011). Deep sparse rectifier neural networks. In Proceedings of international conference on artificial intelligence and statistics (AISTATS), Fort Lauderdale, FL, USA (pp. 315–323).
Lin, M., Chen, Q., & Yan, S. (2014). Network in network. In Proceedings of international conference on learning representations (ICLR), Banff, AB, Canada (pp. 1–10).
He, K., Zhang, X., Ren, S., & Sun, J. (2016). Deep residual learning for image recognition. In Proceedings of IEEE conference on computer vision and pattern recognition (CVPR) (pp. 770–778).
Zhang, Y., Tian, Y., Kong, Y., Zhong, B., & Fu, Y. (2021). Residual dense network for image restoration. IEEE Transactions on Pattern Analysis and Machine Intelligence, 43(7), 2480–2495.
Rumelhart, D. E., Hinton, G. E., & Williams, R. J. (1986). Learning representations by back-propagating errors. Nature, 323(6088), 533–536.
De Stefano, C., Sansone, C., & Vento, M. (2000). To reject or not to reject: That is the question—An answer in case of neural classifiers. IEEE Transactions on Systems, Man, and Cybernetics, 30(1), 84–94.
Geifman, Y., & El-Yaniv, R. (2019). SelectiveNet: A deep neural network with an integrated reject option. In Proceedings of international conference on machine learning (ICML), Long Beach, CA, USA (pp. 2151–2159).
Thulasidasan, S., Bhattacharya, T., Bilmes, J., Chennupati, G., & Mohd-Yusof, J. (2019). Combating label noise in deep learning using abstention. In Proceedings of international conference on machine learning (ICML), vol. 97, Long Beach, CA, USA (pp. 6234–6243).
Kompa, B., Snoek, J., & Beam, A. L. (2021). Second opinion needed: Communicating uncertainty in medical machine learning. NPJ Digital Medicine, 4(1), 4: 1-6.
Ronneberger, O., Fischer, P., & Brox, T. (2015). U-Net: Convolutional networks for biomedical image segmentation. In Proceedings of international conference on medical image computing and computer-assisted intervention (MICCAI), Munich, Germany (pp. 234–241).
Bas, P., Filler, T., & Pevný, T. (2011). Break our steganographic system: The ins and outs of organizing BOSS. In Proceedings of international workshop on information hiding (IH), Prague, Czech Republic (pp. 59–70).
Weber, A. G. (2006). The USC-SIPI image database: Version 5. USC Viterbi School of Engineering, Signal and Image Processing Institute, Los Angeles, CA, USA, Technical Report, 315.
Funding
This work was partially supported by KAKENHI Grants (JP16H06302, JP18H04120, JP20K23355, JP21H04907 and JP21K18023) from the Japan Society for the Promotion of Science (JSPS) and CREST Grants (JPMJCR18A6 and JPMJCR20D3) from the Japan Science and Technology Agency (JST).
Author information
Authors and Affiliations
Contributions
All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chang, CC., Wang, X., Chen, S. et al. On the predictability in reversible steganography. Telecommun Syst 82, 301–313 (2023). https://doi.org/10.1007/s11235-022-00985-0
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-022-00985-0