Abstract
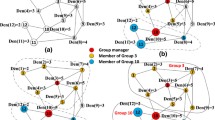
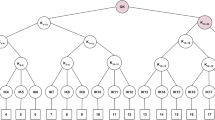
Heterogeneous networks, which can be either integrated wired and wireless networks or fully wireless networks, are convenient as they allow user nodes to be connected whenever and wherever they desire. Group key agreement (GKA) protocols are used to allow nodes in these networks to communicate securely with each other. Dynamic GKA protocols such as Join and Leave Protocol are also important since users can join and leave the network at anytime and the group key has to be changed to provide backward and forward secrecy. Denial-of-Service (DoS) attacks on GKA protocols can disrupt GKA services for secure group communications but most GKA protocols in current literature do not consider protection against DoS attacks. Furthermore, most current GKA protocols only consider outsider attacks and do not consider insider attacks. In this paper, we present three authenticated, energy-efficient and scalable GKA protocols, namely Initial GKA, Join and Leave Protocol, that provide protection against insider and DoS attacks and key confirmation properties. We also present a detection protocol to detect malicious group insiders and continue establishing a group key after blocking these malicious insiders. Unlike current communication energy analysis that uses a single energy per bit value, our communication energy analysis separates point-to-point (P2P) and broadcast communications to provide more detailed study on communications in GKA. Both the complexity and energy analysis show that the three proposed protocols are efficient, scalable and suitable for heterogeneous networks.
Similar content being viewed by others
References
Akyildiz, I. F., Wang, X., & Wang, W. (March 2005). Wireless mesh networks: A survey. Computer Networks Journal.
Burmester, M., & Desmedt, Y. (1995). A secure and efficient conference key distribution system. In Lecture notes in computer science: Vol. 950. Proc. advances in cryptography – Eurocrypt ’94 (pp. 275–286)
Carman, D. W., Kruss, P. S., & Matt, B. J. (September 2000). Constraints and approaches for distributed sensor network security. NAI Labs Technical Report #00-010.
Damodaran, D., Singh, R., & Le, P. D. (2006). Group key management in wireless networks using session keys. Proc. of ITNG 2006 (pp. 402–407), April 2006.
Desmedt, Y., Pieprzyk, J., Steinfeld, R., & Wang, H. X. (2006). A non-malleable group key exchange protocol robust against active insiders. In Lecture notes in computer science: Vol. 4176. Proc. of ISC 2006 (pp. 459–475).
Feeney, L., & Nilsson, M. (2001). Investigating the energy consumption of a wireless network interface in an ad hoc networking environment. IEEE INFOCOM 2001 (pp. 1548–1557), April 2001.
Ghosh, S. K., Patro, R. K., Raina, M., Thejaswi, C., & Ganapathy, V. (2006). Secure group communication in wireless sensor networks. In Proc. of 1st international symposium on wireless pervasive computing, 2006, Jan. 2006.
Ingemarsson, I., Tang, D. T., & Wong, C. K. (1982). A conference key distribution system. IEEE Transactions on Information Theory, 28(5), 714–720.
Intel StrongARM SA-1110 Microprocessor Datasheet. http://download.intel.com/design/strong/datashts/27824105.pdf.
Jung, B. E. (2006). An efficient group key agreement protocol. IEEE Communications Letters, 10(2), 106–107.
Katz, J., & Yung, M. (2003). Scalable protocols for authenticated group key exchange. In Lecture notes in computer science: Vol. 2729. Advances in cryptography – Crypto’03 (pp. 110–125).
Kim, H.-J., Lee, S.-M., & Lee, D.-H. (2004). Constant-round authenticated group key exchange for dynamic groups. In Lecture notes in computer science: Vol. 3329. Proc. of AsiaCrypt 2004 (pp. 245–259).
Kim, Y., Perrig, A., & Tsudik, G. (2004). Tree-based group key agreement. ACM Transaction on Information and System Security, 7(1), 60–96.
Lee, P. P. C., Lui, J. C. S., & Yau, D. K. Y. (2006). Distributed collaborative key agreement and authentication protocols for dynamic peer groups. IEEE/ACM Transactions on Networking, 14(2), 263–276.
Liao, L. J., & Manulis, M. (2006). Tree-based group key agreement framework for mobile ad-hoc networks. In Proc. of AINA 2006 (Vol. 2, pp. 5–9), April 2006.
MIRACL, Multiprecision Integer and Rational Arithmetic C/C++ Library. http://indigo.ie/~mscott/.
Nam, J., Kim, S., & Won, D. (2005). Secure group communications over combined wired and wireless networks. In Lecture notes in computer science: Vol. 3592. Proc. of TrustBus 2005 (pp. 90–99), August 2005.
Nam, J., Lee, J., Kim, S., Kim, S., & Won, D. (2004). Provably-secure and communication-efficient protocol for dynamic group key exchange. Journal of the KIISC (Korean Institute of Information Security and Cryptology), 14(4), 163–181.
Panja, B., Madria, S. K., & Bhargava, B. (2006). Energy and communication efficient group key management protocol for hierarchical sensor networks. In Proc. of IEEE international conference on sensor networks, ubiquitous, and trustworthy computing 2006 (Vol. 1, pp. 384–393), June 2006.
Potlapally, N. R., Ravi, S., Raghunathan, A., & Jha, N. K. (2006). A study of the energy consumption characteristics of cryptographic algorithms and security protocols. IEEE Transactions in Mobile Computing, 5(2), 128–143.
Rivest, R. L., Shamir, A., & Adleman, L. M. (1978). A method for obtaining digital signatures and public-key cryptosystems. Communications of the ACM, 21(2), 120–126.
Shen, Z.-D., Wu, X.-P., Wang, Y.-H., Peng, W.-L., & Zhang, H.-G. (2006). Group key management in grid environment. In Proceedings of first IMSCCS 2006 (Vol. 1, pp. 626–631), June 2006.
Srinivasan, T., Sathish, S., Kumar, R. V., & Vijayender, M. V. B. (2006). A hybrid scalable group key management approach for large dynamic multicast networks. In Proceedings of CIT 2006 (pp. 102–102), Sept. 2006.
Steiner, M., Tsudik, G., & Waidner, M. (2000). Key agreement in dynamic peer groups. IEEE Transactions on Parallel and Distributed Systems, 11(8), 769–780.
Tan, C. H., & Teo, J. C. M. (2005). An authenticated group key agreement for wireless networks. In Proceedings of IEEE Wireless Communications and Networking Conference 2005 (WCNC 2005) (Vol. 4, pp. 2100–2105), March 2005.
Teo, J. C. M., & Tan, C. H. (2005). Energy-efficient and scalable group key agreement for large ad hoc networks. In Proc. of PE-WASUN ’05 (pp. 114–121), October 2005.
Teo, J. C. M., Tan, C. H., & Ng, J. M. (2006). Low-power group key agreement for heterogeneous wireless networks. In Proc. of IWCMC 2006 (pp. 177–182), July 2006.
Teo, J. C. M., Tan, C. H., & Ng, J. M. (2007). Authenticated group key agreement against DoS in heterogeneous wireless networks. In Proceedings of IEEE Wireless Communications and Networking Conference 2007 (WCNC 2007), March 2007.
Trappe, W., Wang, Y. & Liu, K. J. R. (2005). Resource-aware conference key establishment for heterogeneous networks. IEEE/ACM Transactions on Networking, 13(1), 134–146.
Author information
Authors and Affiliations
Corresponding author
Additional information
This is an extended version of a conference paper published in IEEE WCNC 2007 (J.C.M. Teo et al. in Proceedings of IEEE Wireless Communications and Networking Conference 2007 (WCNC 2077), 2007).
Rights and permissions
About this article
Cite this article
Teo, J.C.M., Tan, C.H. & Ng, J.M. Denial-of-service attack resilience dynamic group key agreement for heterogeneous networks. Telecommun Syst 35, 141–160 (2007). https://doi.org/10.1007/s11235-007-9045-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-007-9045-1