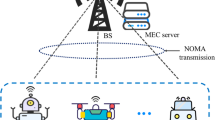
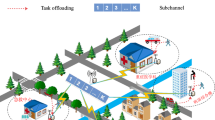
Abstract
Computation offloading can efficiently expand edge resources and is widely used to perform computing-intensive and delay-sensitive tasks. The inability of existing offloading strategies to pay attention to both packet loss problem and performance problems caused by channel noise usually lead to serious encoding costs and retransmission costs in offloading by traditional communication protocols. To address these issues, we propose a dynamic analog-digital coding QUIC (DQUIC) protocol to ensure the efficiency and reliability of edge computing data transmission. The DQUIC protocol uses a dynamic encoding method based on continuous slot communication state to handle sudden errors with a small encoding cost. Moreover, we design a dynamic multi-access edge computing (MEC) model using the DQUIC protocol for communication, which considers the impact of channel noise on communication rate and channel packet loss rate. In the dynamic MEC environment, the double deep Q-learning (DDQN) algorithm is used to solve the offloading decision problem and find the optimal offloading strategy. The experimental results demonstrate that our computation strategy, which leverages DQUIC, surpasses those strategies grounded in the DQUIC protocol and Coco protocol within a dynamic MEC environment.












Similar content being viewed by others
Data availibility
Not applicable
References
Shafi M, Molisch AF, Smith PJ et al (2017) 5g: a tutorial overview of standards, trials, challenges, deployment, and practice. IEEE J Sel Areas Commun 35(6):1201–1221
Shen J, Tan HW, Wang J et al (2015) A novel routing protocol providing good transmission reliability in underwater sensor networks. J Internet Technol 16(1):171–178
Pan Z, Zhang Y, Kwong S (2015) Efficient motion and disparity estimation optimization for low complexity multiview video coding. IEEE Trans Broadcast 61(2):166–176
Zhang J, Yu FR, Wang S et al (2018) Load balancing in data center networks: a survey. IEEE Commun Surv Tutor 20(3):2324–2352
Asif-Ur-Rahman M, Afsana F, Mahmud M et al (2018) Toward a heterogeneous mist, fog, and cloud-based framework for the internet of healthcare things. IEEE Internet Things J 6(3):4049–4062
Hui JW, Culler D (2004) The dynamic behavior of a data dissemination protocol for network programming at scale. In: Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, pp 81–94
Kulkarni S, Wang L (2009) Energy-efficient multihop reprogramming for sensor networks. ACM Trans Sens Netw (TOSN) 5(2):1–40
Naik V, Arora A, Sinha P et al (2007) Sprinkler: a reliable and energy efficient data dissemination service for extreme scale wireless networks of embedded devices. IEEE Trans Mob Comput 6(7):777–789
Iyengar J, Thomson M, et al (2021) Quic: a udp-based multiplexed and secure transport. In: RFC 9000
Roskind J (2013) Experimenting with quic. The Chromium Blog
Wei Y, Yu FR, Song M et al (2018) Joint optimization of caching, computing, and radio resources for fog-enabled IOT using natural actor-critic deep reinforcement learning. IEEE Internet Things J 6(2):2061–2073
Khadir AA, Seno SAH (2021) SDN-based offloading policy to reduce the delay in fog-vehicular networks. Peer-to-Peer Netw Appl 14:1261–1275
Tran TX, Pompili D (2018) Joint task offloading and resource allocation for multi-server mobile-edge computing networks. IEEE Trans Veh Technol 68(1):856–868
Dinh TQ, Tang J, La QD et al (2017) Offloading in mobile edge computing: task allocation and computational frequency scaling. IEEE Trans Commun 65(8):3571–3584
Huang L, Setia S (2008) Cord: Energy-efficient reliable bulk data dissemination in sensor networks. In: IEEE INFOCOM 2008-The 27th Conference on Computer Communications, IEEE, pp 574–582
Zhao Z, Dong W, Bu J, et al (2014) Exploiting link correlation for core-based dissemination in wireless sensor networks. In: 2014 Eleventh Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), IEEE, pp 372–380
Zhao Z, Bu J, Dong W et al (2016) Coco+: exploiting correlated core for energy efficient dissemination in wireless sensor networks. Ad Hoc Netw 37:404–417
De Coninck Q, Bonaventure O (2017) Multipath quic: Design and evaluation. In: Proceedings of the 13th International Conference on Emerging Networking Experiments and Technologies, pp 160–166
Viernickel T, Froemmgen A, Rizk A, et al (2018) Multipath quic: a deployable multipath transport protocol. In: 2018 IEEE International Conference on Communications (ICC), IEEE, pp 1–7
Wang P, Bianco C, Riihijärvi J, et al (2018) Implementation and performance evaluation of the quic protocol in linux kernel. In: Proceedings of the 21st ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, pp 227–234
Duan Y, Gallo M, Traverso S, et al (2017) Towards a scalable modular quic server. In: Proceedings of the Workshop on Kernel-Bypass Networks, pp 19–24
Zhang H, Guo J, Yang L, et al (2017) Computation offloading considering fronthaul and backhaul in small-cell networks integrated with MEC. In: 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), IEEE, pp 115–120
Kamoun M, Labidi W, Sarkiss M (2015) Joint resource allocation and offloading strategies in cloud enabled cellular networks. In: 2015 IEEE International Conference on Communications (ICC), IEEE, pp 5529–5534
Labidi W, Sarkiss M, Kamoun M (2015) Energy-optimal resource scheduling and computation offloading in small cell networks. In: 2015 22nd International Conference on Telecommunications (ICT), IEEE, pp 313–318
Zhang K, Mao Y, Leng S, et al (2017) Optimal delay constrained offloading for vehicular edge computing networks. In: 2017 IEEE International Conference on Communications (ICC), IEEE, pp 1–6
Zeng F, Chen Y, Yao L et al (2021) A novel reputation incentive mechanism and game theory analysis for service caching in software-defined vehicle edge computing. Peer-to-Peer Netw Appl 14:467–481
Liu L, Chang Z, Guo X et al (2017) Multiobjective optimization for computation offloading in fog computing. IEEE Internet Things J 5(1):283–294
Li H, Xu H, Zhou C et al (2020) Joint optimization strategy of computation offloading and resource allocation in multi-access edge computing environment. IEEE Trans Veh Technol 69(9):10214–10226
Zhao Z, Zhao R, Xia J et al (2019) A novel framework of three-hierarchical offloading optimization for MEC in industrial IOT networks. IEEE Trans Industr Inf 16(8):5424–5434
Tang C, Wu H (2022) Joint optimization of task caching and computation offloading in vehicular edge computing. Peer-to-Peer Netw Appl 15:1–16
Yi M, Yang P, Du M et al (2022) Dmadrl: a distributed multi-agent deep reinforcement learning algorithm for cognitive offloading in dynamic MEC networks. Neural Process Lett 54(5):4341–4373
Li P, Xiao Z, Wang X et al (2024) Eptask: deep reinforcement learning based energy-efficient and priority-aware task scheduling for dynamic vehicular edge computing. IEEE Trans Intell Veh 9(1):1830–1846. https://doi.org/10.1109/TIV.2023.3321679
Zhang Z, Chen Y, Zhang D et al (2023) Ctfnet: long-sequence time-series forecasting based on convolution and time-frequency analysis. IEEE Trans Neural Netw Learn Syst. https://doi.org/10.1109/TNNLS.2023.3294064
Yi M, Yang P, Chen M et al (2022) A DRL-driven intelligent joint optimization strategy for computation offloading and resource allocation in ubiquitous edge IOT systems. IEEE Trans Emerg Top Comput Intell 7(1):39–54
Chen P, Luo X, Guo D, et al (2022) Secure task offloading for MEC-aided-UAV system. IEEE Trans Intell Veh
Liao BLJ, Wu W, Li Y (2023) Intelligent reflecting surface assisted secure computation of wireless powered MEC system. IEEE Trans Mobile Comput 11:11593–11605
Chen M, Liu A, Xiong NN et al (2023) Sgpl: an intelligent game-based secure collaborative communication scheme for metaverse over 5g and beyond networks. IEEE J Select Areas Commun 42:767–782
Zhonghua C, Goyal S, Rajawat AS (2024) Smart contracts attribute-based access control model for security & privacy of IOt system using blockchain and edge computing. J Supercomput 80(2):1396–1425
Ju Y, Chen Y, Cao Z et al (2023) Joint secure offloading and resource allocation for vehicular edge computing network: a multi-agent deep reinforcement learning approach. IEEE Trans Intell Trans Syst 24:5555–5569
Rossi M, Bui N, Zanca G et al (2010) Synapse++: code dissemination in wireless sensor networks using fountain codes. IEEE Trans Mob Comput 9(12):1749–1765
Du W, Liando JC, Zhang H, et al (2015) When pipelines meet fountain: fast data dissemination in wireless sensor networks. In: Proceedings of the 13th ACM Conference on Embedded Networked Sensor Systems, pp 365–378
Cui Y, Wang L, Wang X et al (2014) Fmtcp: a fountain code-based multipath transmission control protocol. IEEE/ACM Trans Netw 23(2):465–478
Hagedorn A, Starobinski D, Trachtenberg A (2008) Rateless deluge: Over-the-air programming of wireless sensor networks using random linear codes. In: 2008 International Conference on Information Processing in Sensor Networks (ipsn 2008), IEEE, pp 457–466
Srinivasan K, Kazandjieva MA, Agarwal S, et al (2008) The \(\beta \)-factor: measuring wireless link burstiness. In: Proceedings of the 6th ACM Conference on Embedded Network Sensor Systems, pp 29–42
Gómez D, Agüero R, García-Arranz M et al (2015) On the use of hidden Markov processes and auto-regressive filters to incorporate indoor Bursty wireless channels into network simulatioN platforms. Wireless Netw 21(7):2137–2154
Ghadimi E, Landsiedel O, Soldati P et al (2014) Opportunistic routing in low duty-cycle wireless sensor networks. ACM Trans Sens Netw (TOSN) 10(4):1–39
Chen F, Zhang Z, Li P (2022) Multi-user scheduling and resource allocation algorithm based on transmission delay in 802.11 ax system. J Signal Process 38(3)
Zhao X, Huang G, Jiang J et al (2022) Task offloading of cooperative intrusion detection system based on deep q network in mobile edge computing. Expert Syst Appl 206(117):860
Funding
This work was supported in part by the Consulting Project of Chinese Academy of Engineering under Grant 2023-XY-09, the National Natural Science Foundation of China under Grant 62272100, and in part by the Fundamental Research Funds for the Central Universities and the Academy-Locality Cooperation Project of Chinese Academy of Engineering under Grant JS2021ZT05.
Author information
Authors and Affiliations
Contributions
All authors contributed to the study’s conception and design. Peng Yang performed the methodology, funding acquisition, and project administration. Peng Yang and Ruochen Ma wrote the main manuscript text. Meng Yi provided material preparation, data collection, and analysis. Ruochen Ma and Yifan Zhang carried out experimental verification. Bing Li and Zijian Bai prepared the figures and provided valuable comments on previous versions of the manuscript. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that there is no potential conflict (financial or nonfinancial) of interests regarding the publication of this paper.
Consent to publish
Not applicable.
Ethics approval
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Yang, P., Ma, R., Yi, M. et al. A computation offloading strategy for multi-access edge computing based on DQUIC protocol. J Supercomput (2024). https://doi.org/10.1007/s11227-024-06176-9
Accepted:
Published:
DOI: https://doi.org/10.1007/s11227-024-06176-9