Abstract
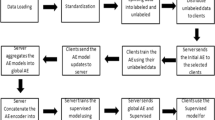
Industrial internet of things (IIoT) is considered as large-scale IoT-based network comprising of sensors, communication channels, and security protocols used in Industry 4.0 for diverse real-time operations. Industrial IoT (IIoT) networks are vulnerable to diverse cyber threats and attacks. Attack detection is the biggest security issue in the IIoT. Various traditional attack detection methods are proposed by several researchers but all are insufficient to protect privacy and security. To address the issue, a novel Gradient Descent Scaling and Segmented Regression Fine-tuned Federated Learning (GDS-SRFFL) method is introduced for IIoT network attack detection. The aim of the GDS-SRFFL method is to enhance the security of an IIoT network. Initially, the novelty of Gradient Descent Scaling-based preprocessing is applied to the raw dataset for obtaining feature feature-scaled preprocessed network sample. Then, the unwanted intrusions are discovered by using a Segmented Regression Fine-tuned Mini-batch Federated Learning model to ensure the protection of IoT networks with the novelty of SoftMax Regression. In order to validate the proposed methodology, experimentations were conducted on different parameters, namely accuracy, precision, recall, specificity, and attack detection time, and the results concluded that proposed GDS-SRFFL has improved accuracy by 10%, precision by 13%, recall by 10%, specificity by 11% as well as minimum attack detection time by 28% as compared to existing techniques like CNN + LSTM (Altunay and Albayrak in Eng Sci Technol Int J 38:101322, 2023, https://doi.org/10.1016/j.jestch.2022.101322), Enhanced Deep and Ensemble learning in SCADA-based IIoT network (Khan et al. in IEEE Trans Ind Inf 19(1):1030–1038, https://doi.org/10.1109/TII.2022.3190352), RNN (Ullah and Mahmoud in IEEE Access 10:62722–62750, 2022, https://doi.org/10.1109/ACCESS.2022.3176317), and other CNN methods. The proposed method “GDS-SRFFL” has overall accuracy of 89.42% as compared to other existing methods.









Similar content being viewed by others
Data availability
Authors declare that all the data being used in the design and production cum layout of the manuscript are declared in the manuscript.
References
Altunay HC, Albayrak Z (2023) A hybrid CNN+ LSTM based intrusion detection system for industrial IoT networks. Eng Sci Technol Int J 38:101322. https://doi.org/10.1016/j.jestch.2022.101322
Khan F, Alturki R, Rahman MA, Mastorakis S, Razzak I, Shah ST (2022) Trustworthy and reliable deep-learning-based cyberattack detection in industrial IoT. IEEE Trans Ind Inf 19(1):1030–1038. https://doi.org/10.1109/TII.2022.3190352
Salehi M, De Borger G, Hughes D, Crispo B (2022) NemesisGuard: mitigating interrupt latency side channel attacks with static binary rewriting. Comput Netw 205:108744. https://doi.org/10.1016/j.comnet.2021.108744
Ngo QD, Nguyen HT, Le VH, Nguyen DH (2020) A survey of IoT malware and detection methods based on static features. ICT Express 6(4):280–286. https://doi.org/10.1016/j.icte.2020.04.005
Yazdinejad A, Kazemi M, Parizi RM, Dehghantanha A, Karimipour H (2023) An ensemble deep learning model for cyber threat hunting in industrial internet of things. Digit Commun Netw 9(1):101–110. https://doi.org/10.1016/j.dcan.2022.09.008
Sarjan H, Ameli A, Ghafouri M (2022) Cyber-security of industrial internet of things in electric power systems. IEEE Access 10:92390–92409. https://doi.org/10.1109/ACCESS.2022.3202914
Ullah I, Mahmoud QH (2022) Design and development of RNN anomaly detection model for IoT networks. IEEE Access 10:62722–62750. https://doi.org/10.1109/ACCESS.2022.3176317
Priya V, Thaseen IS, Gadekallu TR, Aboudaif MK, Nasr EA (2021) Robust attack detection approach for IIoT using ensemble classifier. Comput Mater Contin. https://doi.org/10.32604/cmc.2021.013852
Nasser N, Fadlullah ZM, Fouda MM, Ali A, Imran M (2022) A lightweight federated learning based privacy preserving B5G pandemic response network using unmanned aerial vehicles: a proof-of-concept. Comput Netw 205:108672. https://doi.org/10.1016/j.comnet.2021.108672
Li B, Wu Y, Song J, Lu R, Li T, Zhao L (2020) DeepFed: federated deep learning for intrusion detection in industrial cyber–physical systems. IEEE Trans Ind Inf 17(8):5615–5624. https://doi.org/10.1109/TII.2020.3023430
Anwer M, Khan SM, Farooq MU (2021) Attack detection in IoT using machine learning. Eng Technol Appl Sci Res 11(3):7273–7278. https://doi.org/10.48084/etasr.4202
Benaddi H, Jouhari M, Ibrahimi K, Ben Othman J, Amhoud EM (2022) Anomaly detection in industrial IoT using distributional reinforcement learning and generative adversarial networks. Sensors 22(21):8085. https://doi.org/10.3390/s22218085
Ferrag MA, Friha O, Maglaras L, Janicke H, Shu L (2021) Federated deep learning for cyber security in the internet of things: concepts, applications, and experimental analysis. IEEE Access 9:138509–138542. https://doi.org/10.1109/ACCESS.2021.3118642
Kasongo SM (2021) An advanced intrusion detection system for IIoT based on GA and tree based algorithms. IEEE Access 9:113199–113212. https://doi.org/10.1109/ACCESS.2021.3104113
Nayak S, Ahmed N, Misra S (2021) Deep learning-based reliable routing attack detection mechanism for industrial internet of things. Ad Hoc Netw 123:102661. https://doi.org/10.1016/j.adhoc.2021.102661
Ma C, Yu H, Li Z, Yang Z (2022) Federated learning framework based on data value evaluation in industrial IoT. Secur Commun Netw. https://doi.org/10.1155/2022/7424094
Guo J, Shen Y (2022) Online anomaly detection of industrial IoT based on hybrid machine learning architecture. Comput Intell Neurosci. https://doi.org/10.1155/2022/8568917
Latif S, Zou Z, Idrees Z, Ahmad J (2020) A novel attack detection scheme for the industrial internet of things using a lightweight random neural network. IEEE access 8:89337–89350. https://doi.org/10.1109/ACCESS.2020
Wang Y, Jiang Y, Lan J (2021) Fcnn: an efficient intrusion detection method based on raw network traffic. Secur Commun Netw 2021:1–13. https://doi.org/10.1155/2021/5533269
Aboelwafa MM, Seddik KG, Eldefrawy MH, Gadallah Y, Gidlund M (2020) A machine-learning-based technique for false data injection attacks detection in industrial IoT. IEEE Internet Things J 7(9):8462–8471. https://doi.org/10.1109/JIOT.2020.2991693
Vargas H, Lozano-Garzon C, Montoya GA, Donoso Y (2021) Detection of security attacks in industrial IoT networks: a blockchain and machine learning approach. Electronics 10(21):2662. https://doi.org/10.3390/electronics10212662
Alkahtani H, Aldhyani TH (2021) Botnet attack detection by using CNN-LSTM model for internet of things applications. Secur Commun Netw 2021:1–23. https://doi.org/10.1155/2021/3806459
Li A, Yi S (2022) Intelligent intrusion detection method of industrial internet of things based on CNN-BiLSTM. Secur Commun Netw. https://doi.org/10.1155/2022/5448647
Tharewal S, Ashfaque MW, Banu SS, Uma P, Hassen SM, Shabaz M (2022) Intrusion detection system for industrial internet of things based on deep reinforcement learning. Wirel Commun Mob Comput 2022:1–8. https://doi.org/10.1155/2022/9023719
Jeribi F (2022) A novel classifier for cyber attack detection system in industrial internet of things. J Eng Appl Sci 9(2):1–16. https://doi.org/10.5455/jeas.2022110103
The TON_IoT Datasets. https://research.unsw.edu.au/projects/toniot-datasets. Accessed 10 Dec 2023
Funding
The authors received no specific funding for this study.
Author information
Authors and Affiliations
Contributions
Author Contributions: Idea Conceptualization: Vijay Anand R, Alagiri I, Jayalakshmi P, Anand Nayyar, Balamurugan Balusamy, Writing and Drafting: Vijay Anand R, Alagiri I, Jayalakshmi P, Anand Nayyar, Balamurugan Balusamy; Editing and Language Checks: Anand Nayyar, Jayalakshmi P; Experimentation: Vijay Anand R, Alagiri I, Jayalakshmi P, Balamurugan Balusamy; Proofing: Anand Nayyar, Balamurugan Baluswamy;
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflicts of interest to report regarding the present study.
Ethical approval
No human beings/animals are involved in the research. All the authors have consented to participate and consented to publish in this Journal.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rajasekaran, V.A., Indirajithu, A., Jayalakshmi, P. et al. Gradient scaling and segmented SoftMax Regression Federated Learning (GDS-SRFFL): a novel methodology for attack detection in industrial internet of things (IIoT) networks. J Supercomput (2024). https://doi.org/10.1007/s11227-024-06109-6
Accepted:
Published:
DOI: https://doi.org/10.1007/s11227-024-06109-6