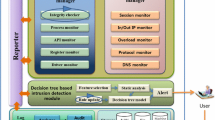
Abstract
Advanced persistent threat attacks are considered as a serious risk to almost any infrastructure since attackers are constantly changing and evolving their advanced techniques and methods. It is difficult to use traditional defense for detecting the advanced persistent threat attacks and protect network information. The detection of advanced persistent threat attack is usually mixed with many other attacks. Therefore, it is necessary to have a solution that is safe from error and failure in detecting them. In this paper, an intelligent approach is proposed called “APT-Dt-KC” to analyze, identify, and prevent cyber-attacks using the cyber-kill chain model and matching its fuzzy characteristics with the advanced persistent threat attack. In APT-Dt-KC, Pearson correlation test is used to reduce the amount of processing data, and then, a hybrid intrusion detection method is proposed using Bayesian classification algorithm and fuzzy analytical hierarchy process. The experimental results show that APT-Dt-KC has a false positive rate and false negative rate 1.9% and 3.6% less than the existing approach, respectively. The accuracy and detection rate of APT-Dt-KC has reached 98% with an average improvement of 5% over the existing approach.









Similar content being viewed by others
References
Alazzam H, Sharieh A, Sabri KE (2020) A feature selection algorithm for intrusion detection system based on Pigeon inspired optimizer. Expert Syst Appl. https://doi.org/10.1016/j.eswa.2020.113
Quincozes SE, Albuquerque C, Passos D, Mossé D (2021) A survey on intrusion detection and prevention systems in digital substations. Comput Netw. https://doi.org/10.1016/j.comnet.2020.107679
Bostani H, Sheikhan M (2017) Modification of supervised OPF-based intrusion detection systems using unsupervised learning and social network concept. Pattern Recogn 62:56–72
Hassan MM, Gumaei A, Alsanad A, Alrubaian M, Fortino G (2020) A hybrid deep learning model for efficient intrusion detection in big data environment. Inf Sci 513:386–396
Condomines JP, Zhang R, Larrieu N (2019) Network intrusion detection system for UAV ad-hoc communication: From methodology design to real test validation. Ad Hoc Netw. https://doi.org/10.1016/j.adhoc.2018.09.004
Martinez CV, Vogel-Heuser B (2021) A host intrusion detection system architecture for embedded industrial devices. J Franklin Inst 358:210–236
Setiawan B, Djanali S, Ahmad T, Aziz MN (2019) Assessing centroid-based classification models for intrusion detection system using composite indicators. Procedia Comput Sci 161:665–676
Rahouma K, Ali A (2019) Applying intrusion detection and response systems for securing the client data signals in the Egyptian optical network. Procedia Comput Sci 163:538–549
Dong Y, Wang R, He J (2019) "Real-Time Network Intrusion Detection System Based on Deep Learning," in: 2019 IEEE 10th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, pp 1–4
Zhou Y, Mazzuchi TA, Sarkani S (2020) M-AdaBoost-A based ensemble system for network intrusion detection. Expert Syst Appl 162:2020. https://doi.org/10.1016/j.eswa.2020.113864
Zimba A, Chen H, Wang Z (2019) Bayesian network based weighted APT attack paths modeling in cloud computing. Futur Gener Comput Syst 96:525–537
Lee M, Choi J, Choi C, Kim P (2017) APT attack behavior pattern mining using the FP-growth algorithm," in: 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, USA, pp 1-4
Hasan K, Shetty S, Ullah S (2019) Artificial Intelligence Empowered Cyber Threat Detection and Protection for Power Utilities, in: 2019 IEEE 5th International Conference on Collaboration and Internet Computing (CIC), Los Angeles, USA, pp 354–359
Wang Q, Cai X, Tang Y, Ni M (2021) Methods of cyber-attack identification for power systems based on bilateral cyber-physical information. Int J Elect Power Energy Syst. https://doi.org/10.1016/j.ijepes.2020.106515
Bhatnagar D, Som S, Khatri SK (2019) Advance Persistant Threat and Cyber Spying - The Big Picture, Its Tools, Attack Vectors and Countermeasures, in: 2019 Amity International Conference on Artificial Intelligence (AICAI), Dubai, United Arab Emirates, pp 828–839
Eggers S (2021) A novel approach for analyzing the nuclear supply chain cyber-attack surface. Nucl Eng Technol 53:879–887
Gu J, Wang L, Wang H, Wang S (2019) A novel approach to intrusion detection using SVM ensemble with feature augmentation. Comput Secur 86:53–62
Zulkefli Z, Singh MM, Shariff ARM, Samsudin A (2017) Typosquat cyber crime attack detection via smartphone. Procedia Comput Sci 124:664–671
Cho DX, Nam HH (2019) |A method of monitoring and detecting APT attacks based on unknown domains. Procedia Comput Sci 150:316–323
Dargahi T, Dehghantanha A, Nikkhah Bahrami P, Conti M, Bianchi G, Benedetto L (2019) A Cyber-Kill-Chain based taxonomy of crypto-ransomware features. J Comput Virol Hack Tech 15:277–305
Tankard C (2011) Advanced Persistent threats and how to monitor and deter them. Netw Secur 2011:16–19
Khan MS, Siddiqui S, Ferens K (2018) “A Cognitive and Concurrent Cyber Kill Chain Model”, 2018, in: Computer and Network Security Essentials, Springer, pp 585-602
Bryant B, Saiedian H (2017) A novel kill-chain framework for remote security log analysis with SIEM software. Comput Secur 67:198–210
Yadav T, Rao AM (2015) “Technical Aspects of Cyber Kill Chain”, In: Security in Computing and Communications. (SSCC 2015), Communications in Computer and Information, Vol 536. Springer, https://doi.org/10.1007/978-3-319-22915-7_40
Mohsin M, Anwar Z (2016) "Where to Kill the Cyber Kill-Chain: An Ontology-Driven Framework for IoT Security Analytics," in: 2016 International Conference on Frontiers of Information Technology (FIT), Islamabad, 2016, Islamabad, Pakistan, pp 23-28
Kiwiaa D, Dehghantanhaa A, Choob K-KR, Slaughter J (2018) A cyber kill chain based taxonomy of banking Trojans for evolutionary computational intelligence. J Comput Sci 27:394–409
Verma R, Chandra S (2020) "A Fuzzy AHP Approach for Ranking Security Attributes in Fog-IoT Environment," in: A Fuzzy AHP Approach for Ranking Security Attributes in Fog-IoT Environment (ICCCNT), Kharagpur, India, pp 1–5
Ogundoyin SO, Kamil IA (2020) A Fuzzy-AHP based prioritization of trust criteria in fog computing services. Appl Soft Comput 97:106789
Liu Y, Eckert CM, Earl C (2020) A review of fuzzy AHP methods for decision-making with subjective judgements. Expert Syst Appl 161:113738
Kalaiselvi B, Thangamani M (2020) An efficient Pearson correlation based improved random forest classification for protein structure prediction techniques. Measurement 162:107885
Singh VK, Callupe SP, Govindarasu M (2019) Testbed-based Evaluation of SIEM Tool for Cyber Kill Chain Model in Power Grid SCADA System”, in: 2019 North American Power Symposium (NAPS), Wichita, KS, USA
Kim J, Baskerville RL, Ding Y (2020) Breaking the privacy kill chain: protecting individual and group privacy online. Inf Syst Front 22:171–185
Shameli-Sendi A, Dagenais M (2014) ARITO: cyber-attack response system using accurate risk impact tolerance. Int J Inf Secur 13:367–390
Duncan A, Creese S, Goldsmith M (2019) "A Combined Attack-Tree and Kill-Chain Approach to Designing Attack-Detection Strategies for Malicious Insiders in Cloud Computing", in: 2019 International Conference on Cyber Security and Protection of Digital Services (Cyber Security),Oxford, United Kingdom, United Kingdom, pp 1–9
Schneier B (2019) Attack Trees, Dr. Dobb’s Journal, 24
Hoffmann R (2019) "Markov Models of Cyber Kill Chains with Iterations", in: International Conference on Military Communications and Information Systems (ICMCIS), Budva, Montenegro
Hoffmann R (2018) The general cyber-attack life cycle and its continuous time Markov chain model. Ekonomiczne Problemy Usług 10:121–130
Hutchins EM, Cloppert MJ, Amin RM (2011) "Intelligence-driven computer network defense informed by analysis of adversary campaigns and intrusion kill chains", Leading Issues in Information Warfare and Security Research, pp 78–104
Martin L (2015) "Seven Ways to Apply the Cyber Kill Chain with a Threat Intelligence Platform," [Online]. Available: https://www.lockheedmartin.com/content/dam/
Yang L, Li P, Yang X, Xiang Y, Jiang F, Zhou W (2019) "Effective Quarantine and Recovery Scheme Against Advanced Persistent Threat”, IEEE Transactions on Systems, Man, and Cybernetics: Systems, pp1–5
Joloudari JH, Haderbadi M, Mashmool A, Ghasemigol M, Band SS, Mosavi A (2020) Early detection of the advanced persistent threat attack using performance analysis of deep learning. IEEE Access 8:186125–186137
Yan D, Liu F, Jia K (2019) "Modeling an Information-Based Advanced Persistent Threat Attack on the Internal Network," in: IEEE International Conference on Communications (ICC), Shanghai, China, pp 1–7
Yang L-X, Huang K, Yang X, Zhang Y, Xiang Y, Tang YY (2020) "Defense against advanced persistent threat through data backup and recovery," IEEE Transactions on Network Science and Engineering, pp 1–1
Ahmed Y, Asyhari AT, Rahman MA (2021) A cyber kill chain approach for detecting advanced persistent threat. Comput Mater Continua 67:2497–2513
Xuan CD (2021) Detecting APT Attacks Based On Network Traffic Using Machine Learning. Journal of Web Engineering. https://doi.org/10.13052/jwe1540-9589.2019
Immink KAS, Weber JH (2014) Minimum Pearson distance detection for multilevel channels with gain and/or offset mismatch. IEEE Trans Inf Theory 60:5966–5974
Rummel RJ (1976) Understanding Correlation, Life Time of Correlations and its Applications. Wydawnictwo Niezależne, pp 5–21
Mu Y, Liu X, Wang L (2018) A Pearson’s correlation coefficient based decision tree and its parallel implementation. Inf Sci 435:40–58
Kyrimi E, Neves MR, McLachlan S, Neil M, Marsh W, Fenton N (2020) Medical idioms for clinical Bayesian network development. J Biomed Inform 108:103495
Mohammadi H (2012) "Strategic Decision Making in Resource Selection", 2, 1-12
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Panahnejad, M., Mirabi, M. APT-Dt-KC: advanced persistent threat detection based on kill-chain model. J Supercomput 78, 8644–8677 (2022). https://doi.org/10.1007/s11227-021-04201-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-021-04201-9